
To most people, the process of logging into a Microsoft Windows machine is a simple process of entering a username and a password. However, for a cybersecurity professional, the process is a carefully orchestrated mechanism. Unfortunately, throughout the history of the various Windows operating system versions, criminals have also sought ways to disrupt this process in order to breach a network. The primary target of these attacks is the Security Account Manager (SAM).
What Is the Security Accounts Manager (SAM)?
The Security Account Manager (SAM) is a critical Windows operating system database housing user account credentials, including usernames and hashed passwords. It helps secure system data in the event of a breach. Managed by the Local Security Authority (LSA), it validates user logins by cross-referencing passwords within the SAM database. Stored in the c:\windows\system32\config\SAM directory and HKEY_LOCAL_MACHINE\SAM registry, the SAM file is tightly secured during system runtime, preventing direct copying or relocation. This protection is achieved with exclusive file system locks enforced by the operating system.
The system locks that restrict online copying of the SAM file remain active until the OS encounters a critical error or shutdown. Despite this protection, threat actors may extract password hashes for offline brute-force attacks by dumping the SAM file's on-disk contents using various methods.
This is what the contents of the SAM file look like:
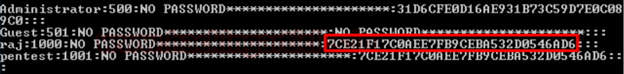
The above image lists the user details registered on the system. The third field, "raj," represents the username, "1000" signifies the user ID, "NO PASSWORD" followed by asterisks indicates the LM Hash, and the highlighted box in red denotes the NTLM hash.
Let’s dive deeper into what LM hash and NTLM hash are.
Windows hashes
LM and NTLM hashes are cryptographic representations of passwords in Windows systems.
LM hash: LM hashes represent the oldest form of password storage in Windows, originating from OS/2 in the 1980s; their limited character set makes them susceptible to password-cracking attacks. If accessible, LM hashes can be obtained from the SAM database on a Windows system or the NTDS database on the Domain Controller. Starting with Windows Vista/Server 2008, LM was disabled by default due to its vulnerabilities, but the LM hash is still stored for backward compatibility reasons. Preventing the storage of LM hash is possible by using passwords longer than 14 characters or incorporating specific Unicode characters.
NTLM hash: In contemporary Windows operating systems, this hash represents a more secure method of password storage than LM. It is computed based on the entirety of the user-entered password.
SAM database attacks
Pass-the-hash attack: In this attack, threat actors retrieve stored hashes from the SAM database on Windows systems and then utilize these stolen hashes to gain unauthorized access to network resources by injecting them into local sessions. This method can affect servers using NTLM or LM authentication across various operating systems, although Windows, due to its Single-Sign-On (SSO) feature, might face increased vulnerability by allowing access to resources with a one-time login.
Corrupting the SAM database: A threat actor with administrative access may manipulate the SAM database, creating new accounts, altering passwords, or disabling existing ones. Poor user account management might lead to surplus or obsolete accounts, expanding the attack surface and facilitating unauthorized access.
Deleting the SAM database: Prior to the release of Windows 2000, deleting the SAM file allowed threat actors to bypass local authentication, granting access to any account without a password. Microsoft addressed this vulnerability in Windows XP by shutting down the system if an attempt to delete the SAM file occurred. However, threat actors can still delete the SAM file using software utilities such as an emulated virtual device or a boot disk.
Best practices for securing the SAM database
- Audit SAM database access: Activate the Audit Policy: Object Access: SAM feature to monitor SAM database access, detecting any unauthorized attempts.
- Restrict administrative privileges: Minimize the count of users with administrative rights to mitigate privilege escalation threats and limit SAM database access.
- Implement strong, unique passwords: Utilize robust and distinct passwords for each user account to deter pass-the-hash attacks and other credential theft methods.
- Monitor security logs: Analyze security logs to track SAM database access, security-related events, and suspicious activity. Establish a response plan for detected security incidents.
- Review accounts regularly: Validate all accounts on the system, removing unnecessary or outdated ones associated with former employees or outdated processes. This practice reduces the attack surface and thwarts the reuse of obsolete accounts.
- Enforce access control: Apply access control measures to safeguard sensitive files and folders, preventing unauthorized entry and increasing defenses against privilege escalation attacks.
Conclusion
The Windows SAM is crucial for storing user credentials and password hashes. Although NTLM hashes provide better security than the vulnerable legacy LM hashes, threats to compromising Windows user passwords persist. Hence, organizations must prioritize this issue, implementing essential security measures to safeguard Windows credentials.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor and do not necessarily reflect those of Tripwire.
Mastering Security Configuration Management
Master Security Configuration Management with Tripwire's guide on best practices. This resource explores SCM's role in modern cybersecurity, reducing the attack surface, and achieving compliance with regulations. Gain practical insights for using SCM effectively in various environments.

