
What is an Attack Surface?
An attack surface is the total number of channels, pathways, or areas that threat actors can utilize to gain unauthorized access to networks. The result is that they can obtain private information or carry out a cyber-attack. An attack surface comprises the organizational assets a threat actor can exploit to gain unauthorized access.
Attack surfaces include systems that are directly involved in mission-critical operations, as well as those that provide peripheral services or access to important data. Reducing your organization's attack surface is essential to protect against potential threats. By understanding which areas have potential vulnerabilities and taking steps to manage them, you can minimize the chances of being compromised.
For most modern organizations, the attack surface is intricate and vast. For instance, the attack surface of businesses employing cloud services and hybrid work methods grows larger and more sophisticated by the day, and this can pose a cybersecurity risk. The larger the attack surface, the more opportunities for a potential attacker to exploit vulnerabilities and compromise the system's security.
There are several measures organizations can implement to reduce their attack surface and the risk of cyber attacks. These include network segmentation, regular security audits, vulnerability scanning, and other security best practices throughout the organization's infrastructure.
Understanding attack surfaces is crucial for businesses seeking to bolster their security policies. A poorly controlled attack surface can lead to catastrophic consequences.
Types of Attack Surfaces to Watch
Attack surfaces can be divided into two types: digital and physical.
Digital Attack Surfaces
Digital attack surfaces encompass software, networks, and other computerized assets susceptible to cyber threats. Common types of digital attack surfaces include:
- Weak Passwords: Passwords that are simple to crack by brute-force attacks increase the likelihood that cybercriminals would breach user accounts. They can then gain network access, steal sensitive information, transmit malicious software, and harm infrastructure.
- Network Perimeter: The boundary of a network is a fundamental digital attack surface. It includes internet-facing servers, routers, and firewalls. Unauthorized users can attempt to exploit potential vulnerabilities in these components to breach a network.
- Applications and Software: Web applications, mobile apps, and other operating system components contribute to the digital attack surface. Vulnerabilities in these applications can provide opportunities for exploitation.
Physical Attack Surfaces
Physical attack surfaces, on the other hand, pertain to tangible assets such as servers, computers, and IoT devices. These surfaces are vulnerable to physical manipulation, theft, or destruction. Common examples of physical attack surfaces include:
- Physical Infrastructure: Physical facilities, such as data centers, server rooms, and telecommunications infrastructure, are part of the physical attack surface. Unauthorized physical access to these areas can result in data breaches.
- Device Theft: Criminals may steal or get access to endpoint devices by breaking into an organization's premises. The thieves can access data and processes stored on these devices once they obtain the hardware. They may also utilize the identity and permissions of the device to get unauthorized access to other network resources. Endpoints utilized by remote workers, employees' personal and mobile devices, and incorrectly discarded gadgets are common targets of theft.
The image below shows the digital and physical attack surfaces vulnerable to threat actors:
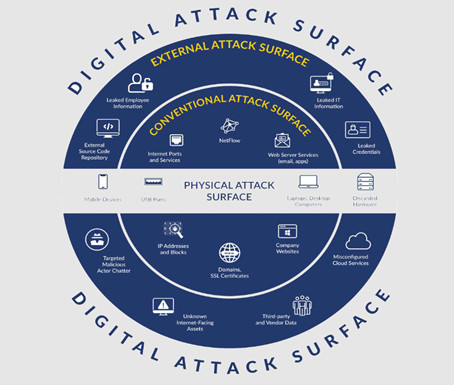
To effectively protect an organization's digital assets from cyber-attacks, a comprehensive security strategy is required.
How to Reduce Your Digital and Physical Attack Surface
Reducing the attack surface is critical to enhancing cybersecurity. This involves taking a proactive approach to securing your organization's digital and physical assets.
Addressing the Digital Attack Surface
A network attack surface is made up of all security vulnerabilities and flaws in connected hardware and software. To ensure the network remains secure, network administrators can follow these tips to reduce the digital attack surface:
- Reduce the Amount of Code Being Executed: The more code that runs on a system, the more likely that system will have an exploitable vulnerability. Reducing the amount of code executed can help reduce the attack surface and protect data from cyber-attacks.
- Microsegmentation: This technique divides a network into isolated, logical pieces, each with its security settings. Isolating these units aids in the containment of threats to the unit and prevents bad actors from making unwanted lateral movements.
- Network Access Control: NAC allows a company to prevent unauthorized users from accessing a private network.
Addressing the Physical Attack Surface
A physical attack surface refers to all network endpoint devices, such as desktop systems, laptops, USB ports, mobile phones, and hard drives. Threat actors with physical access to a computing device can utilize it to search for digital attack surface entry points such as default security settings, unpatched software, misconfigurations, or vulnerabilities.
Insider threats such as employees fooled by social engineering attacks, rogue employees, and criminal intruders imitating service workers can exploit the physical attack surface. External dangers include physical break-ins and carelessly discarded hardware that may contain sensitive information.
Here's how you can reduce your physical attack surface:
- Physical Access Control: Erect physical barriers to prevent prospective break-ins. You should also harden physical installations against accidents, natural disasters, or cyber attackers. Access control systems, such as key cards and smart locks, are two examples.
- Surveillance and Notification Systems: Install security cameras and notification systems to monitor sensitive locations. You can employ intrusion detection sensors and heat sensors.
- Disaster Recovery: Develop policies and processes and test them regularly to guarantee their effectiveness and relevance. These practices help to maintain safety while also shortening recovery times following disruptive disasters.
2 General Cyber Security Strategies to Follow
Complement your security with these general cyber security tips for the best results:
- Regular Security Audits and Vulnerability Scanning: Regular security assessments and vulnerability scanning can help you identify weaknesses in your systems. It is critical to have complete attack surface visibility to prevent problems with cloud and on-premises networks and to ensure that only authorized devices can access them. A thorough scan should not only detect security issues but also demonstrate how endpoints can be manipulated.
- User Training and Awareness: Regular training about data security best practices, phishing awareness, and social engineering tactics will empower users to recognize and avoid potential threats. This is vital for all employees, from the interns through the C-Suite. No one is exempt from being targeted by cybercrime. Teams that handle sensitive data but have limited cybersecurity knowledge. That includes your sales and marketing department and even some company executives. Well-informed staff are less likely to fall victim to attacks, thereby shrinking the risk of cyber attacks.
You can even go a step further and encourage select employees–maybe your IT department—to get top security certifications from reputable associations like ISC2 and CompTIA, for example. This way, apart from playing their original roles in the company, they can contribute to ensuring the security of your systems when the need arises. This helps establish a culture of security throughout the organization. Besides, it's a great opportunity for employees to enhance their professional skills for career advancement.
Overall, the best way to protect yourself from cyber attacks is to view cyber security holistically. That means considering not just the specific points that can be exploited and possible attack vectors but also the human element.
In Closing
The attack surface represents the points of vulnerability of a business. Reducing the attack surface is not a one-time effort but an ongoing process that requires continuous vigilance and adaptability. Understanding your digital and physical attack surfaces and employing proactive strategies to reduce them is essential for safeguarding your known and unknown assets.
By investing in robust security measures and fostering a security-conscious organizational culture, businesses can significantly minimize their attack surface and mitigate the risks posed by malicious actors.
About the author:

Nathan House is the founder and CEO of StationX. He has over 25 years of experience in cyber security, where he has advised some of the largest companies in the world. Nathan is the author of the popular "The Complete Cyber Security Course," which has been taken by over half a million students in 195 countries. He is the winner of the AI "Cyber Security Educator of the Year 2020" award and a finalist for Influencer of the Year 2022.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire.
Mastering Security Configuration Management
Master Security Configuration Management with Tripwire's guide on best practices. This resource explores SCM's role in modern cybersecurity, reducing the attack surface, and achieving compliance with regulations. Gain practical insights for using SCM effectively in various environments.

