
2016 marks the ninth year Verizon has published its annual Data Breach Investigations Report (DBIR). Once again, organizations sent their data on thousands of security incidents and data breaches to Verizon, whose researchers analyzed that information to highlight new patterns, steady trends, and interesting tidbits in the evolving digital threat landscape. For its 2016 Data Breach Investigations Report (available for download here), Verizon used a final dataset of 64,199 security incidents and 2,260 data breaches. Here are some important takeaways from this year's report.
OVERALL STATS
No locale, industry, or organization is safe from attackers who wish to compromise their data. Verizon's dataset illustrates exactly that point. This year's incidents occurred in over 82 countries across a variety of industries, especially in the public, entertainment, finance, and information sectors. There were far more security incidents than data breaches, or security incidents which resulted in the confirmed disclosure (not just potential exposure) of data to an unauthorized party. Verizon's dataset revealed that most data breaches affected organizations in the financial, accommodation, information, and public sectors. On a deeper level, a majority of the attackers behind this year's incidents were external actors motivated by financial gain. They went about their attacks by means of hacking, malware distribution, and phishing, with social engineering attacks considerably boosted by Dridex-based campaigns. Phishing is a quick and easy way for attackers to steal a victim's credentials, which might explain why in 81.9 percent of incidents, the initial compromise took minutes. By contrast, exfiltration took days in more than half (67.8 percent) of cases, a period of time which reflects a rise in point-of-sale attacks where malicious actors drop malware that capture, package, and execute scheduled exfiltration reports. As the time for attackers to compromise a target decreases, so too does the time for companies to discover a security incident. Close to a quarter of events included in Verizon's dataset were discovered in a matter of "days or less." Unfortunately, that percentage is increasing at a slower rate than the proportion of compromises that took "days or less", which means attackers are one step ahead of security personnel.
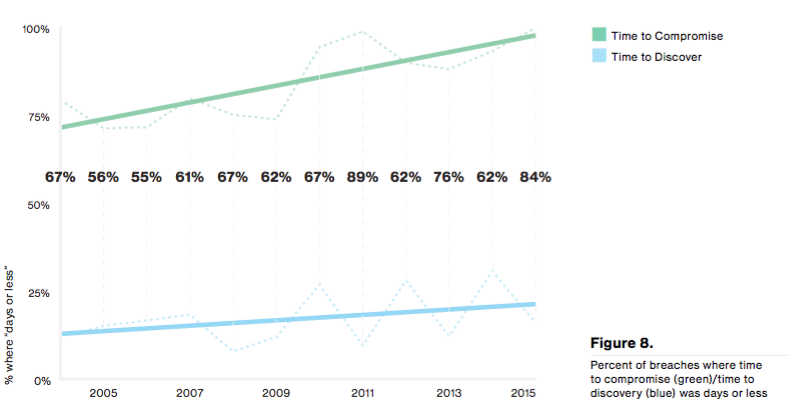
Source: Verizon DBIR 2016, p.10 IT staff continue to struggle with detection and response. Indeed, internal breach discovery detected fewer incidents than did fraud detection, third parties, and law enforcement.
VULNERABILITIES
Not all vulnerabilities are exploited the same. Some flaws found in Adobe and Microsoft were exploited in a matter of days, whereas attackers waited months to exploit bugs in Apple and Mozilla. On average, bad actors took about a month to exploit a vulnerability, with half of all first exploitation attempts having occurred within a period of between 10 and 100 days. That doesn't mean attackers focused in only on new vulnerabilities. Quite the contrary, older vulnerabilities still proved to be a favorite tool among malicious actors. Some attackers also automated the delivery of weaponized vulnerabilities across the web. Those attacks notwithstanding, the security industry generally kept pace with last year's vulnerabilities. Indeed, the millions of flaws that were opened in 2015 for the most part balanced out with those that were closed.
"Basically, we confirmed across multiple datasets that we are treading water--we aren’t sinking in new vulnerabilities, but we’re also not swimming to the land of instantaneous remediation and vuln-free assets," Verizon explains in its report. "However, all that patching is for naught if we’re not patching the right things. If we’re going to tread, let’s tread wisely."
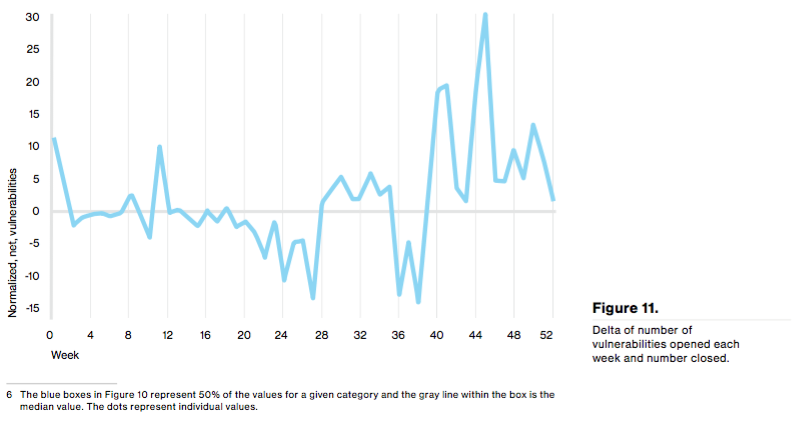
Source: Verizon DBIR 2016, p.14 Going forward, organizations should prioritize which vulnerabilities should be remediated first, apply risk mitigations or replace an asset if it can't be patched, and implement vulnerability scanning to help detect unknown vulnerabilities.
PHISHING
In 2015, there were 9,576 phishing incidents, 916 of which reported a breach of data. Phishing is type of social engineering that attempts to lure a recipient into clicking on an attachment or URL in some piece of malicious correspondence. It has been around for years, but employees still struggle to identify an attack email. To illustrate, 30 percent of phishing messages were opened by the target across all campaigns last year. It took a recipient an average of one minute 40 seconds to open the email and three minutes 45 seconds to click on the malicious attachment.
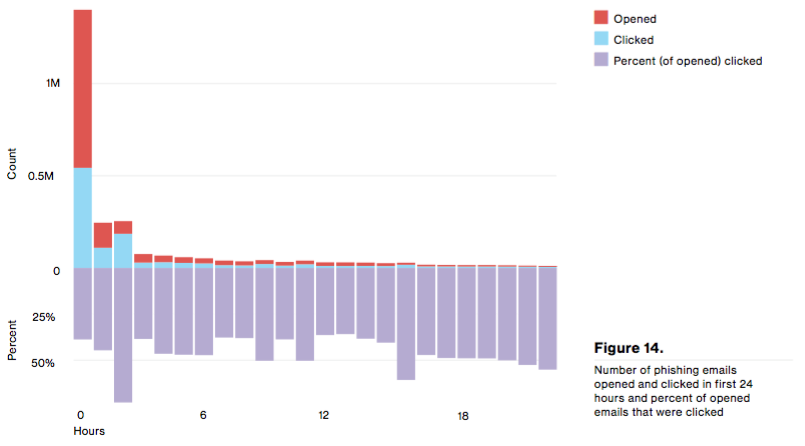
Source: Verizon DBIR 2016, p.18 The main perpetrators behind last year's phishing campaigns were organized crime syndicates (89 percent) and state-sponsored actors (nine percent). Once again, Dridex shifted the report's findings towards the former.
"The smaller proportion of nation-state Actors in this year’s data is due to a large contribution from a particular contributor who saw a great deal of 'Dridex' campaigns which skewed the data toward organized crime," Verizon observes. "We should not conclude from this that certain groups from East Asia have had a crisis of conscience and mended their wicked ways."
Those incidents that disclosed people's information mainly consisted of stolen credentials (91 percent), though attackers did make off with organizations' trade secrets, as well. To protect against phishing attacks, Verizon recommends that enterprises implement email filtering, conduct employee awareness training on how to spot a phish, segment the network and integrate secure authentication procedures to limit the impact of a successful phish should it occur, and monitor the network for signs of data exfiltration.
CREDENTIALS
For the first time in the history of Verizon's DBIR, the topic of credentials received its own section. There were 1,429 incidents of credential theft last year. In those instances, attackers made off with credentials via hacking and malware, and they in turn used the stolen credentials more than three quarters (77 percent) of the time.
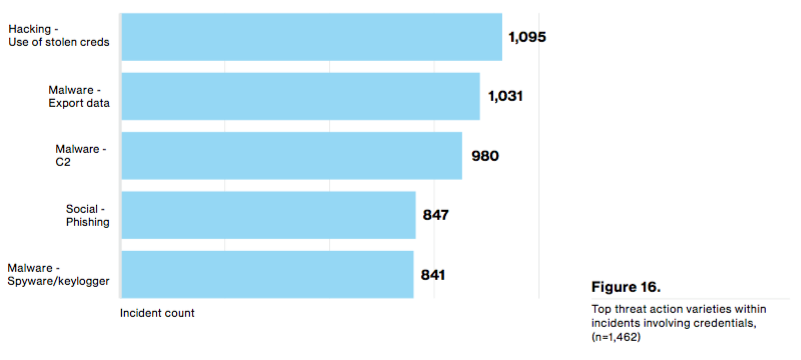
Source: Verizon DBIR 2016, p.21
"We are realists here, we know that implementation of multi-factor authentication is not easy," Verizon admits. "We know that a standard username and password combo may very well be enough to protect your fantasy football league. We also know that implementation of stronger authentication mechanisms is a bar raise, not a panacea. Even with all of that, 63% of confirmed data breaches involved leveraging weak/default/stolen passwords. This statistic drives our recommendation that this is a bar worth raising."
INCIDENT CLASSIFICATION PATTERNS
As with years past, 90 percent of the breaches found in this year's DBIR fit into one of nine classification patterns: web app attacks, POS intrusions, miscellaneous errors, privilege misuse, cyber-espionage, payment card skimmers, physical theft/loss, crimeware, denial of service, and "everything else." Not much has changed in the ranking of these patterns since last year. Crimeware fell from third last year to sixth this year. This development could reflect Verizon's rejection of incidents involving secondary motives for its dataset, or it could simply be due to changes in the organizations that contributed data this year. Here are a few highlights in this section that do stand out:
- There were a lot of denial-of-service attacks across all industries.
- Web apps accounted for the greatest number of confirmed data breaches, particularly in the finance, information, entertainment, and educational sectors.
- Patterns commonly classified as incidents as opposed to confirmed data breaches (Crimeware, Insider and Privilege Misuse, and Physical Theft and Loss) were mostly provided by public sector and healthcare.
All of the incident classification pattern subsections are chock full of information. With that in mind, those who are interested in reading about a specific classification pattern's evolution are encouraged to read this year's DBIR in full.
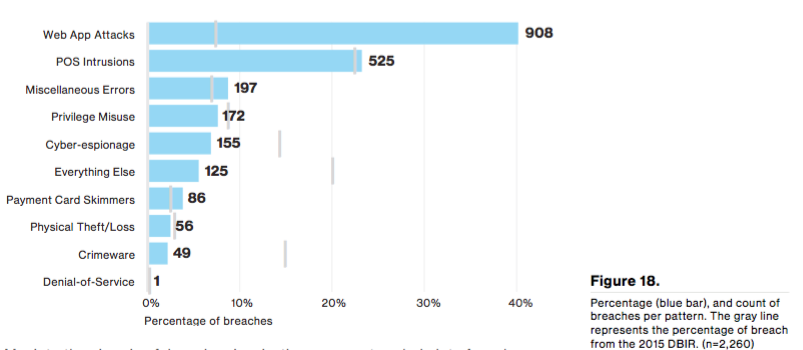
Source: Verizon DBIR 2016, p.23
CONCLUSION
As always, Verizon's Data Breach Investigations Report provides important insight into nine classification patterns with which most security incidents are associated. But as we all know, those patterns do not operate in a vacuum. An attacker could use phishing to steal a person's stolen credentials, which they could then use as the launch point for a secondary attack by which they gain access to a network and choose to download malware or install a backdoor.
"Having an understanding of how patterns can complement each other and share portions of event chains can help direct your efforts as to what to prioritize your limited resources against. That is, knowing the processes used by the Actors, the tools (Actions) to accomplish their goals and how many of these patterns begin with the same or similar bag of tricks."
For more information on what threats you should look out for this year, please download Verizon's report here. Title image courtesy of ShutterStock
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

