A security firm has spotted a new spam campaign that seeks to trick email users into downloading Dridex banking malware. According to research conducted by Heimdal Security, the spam campaign’s email messages are delivered with a .doc attachment that contains macros, which attempt to download Dridex. The contents of each spam message reads as follows:
From: [spoofed / fake return address] Subject Line: Scanned from a Xerox Multifunction Printer Body: Please open the attached document. It was scanned and sent to you Using a Xerox Multifunction Printer. Attachment File Type: DOC, Multi-Page Multifunction Printer Location: Device Name: XRX9C934E5EEC46 For more information on Xerox products and solutions, please visit http://www.xerox.com Attached: Scanned from a Xerox Multifunction Printer.doc
Once the suspicious document is opened, it attempts to use the macros to call up Dridex from the following locations, all of which have been sanitized by Heimdal: hxxp: // tgequestriancentre [.] co.uk/708/346.exe hxxp: // sudburyhive [.] org / 708 / 346.exe hxxp: // werktuigmachines [.] be / 708 / 346.exe hxxp: // colchester-institute [.] com / 708 / 346.exe As Dridex runs in memory and never drops a file into the hard drive, its payload leaves a small footprint, which bolster’s the malware’s evasive capabilities. Even so, according to Virus Total, more than half (almost 55 percent) of antivirus companies have successfully detected the Trojan as part of this spam campaign at the time of this writing. Once activated, the malware contacts a series of C&C servers to deliver all information stolen from the victim and writes the following Binary Large OBjects to the registry:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\CLSID\{91179CCE-14A2-1D89-01D5-125992394513}\ShellFolder
01D3A3627F1088934 “=
hex:90,77,a9,7c,3c,f2,f0,e5,46,1c,c3,7b,fd,97,c1,19,aa,ce,1f,c5,2f,51,80,82,3a,7f,ec,
26,a9,83,df,19,aa,d7,12,cd,2f,51,83,cc,6e,38,e3,09,ea,d9,44,13,5c,57,81,ce,ec,89,a1,
9b,d1,dc,ab,58,05,37,8b,62,0c,50,0e,bd [..]
The data is then split into two data sets, both of which are XOR’d and contain configuration and web injects. Morten Kjaersgaard, CEO of Heimdal Security, told SCMagazine.com in an email that though this particular spam run is not too unusual when compared to other campaigns, it's much more “refined and stealthy” in its attack mechanisms. “As users we need to constantly remind ourselves that hackers are getting better at what they do,” he said. “This is serious business [for them] and we should consider this a serious threat.” Kjaersgaard is right. Dridex, the direct successor of the online banking malware Cridex, was first detected back in November of 2014. Since then, it has evolved significantly with respect to its delivery methods, as analyzed by a recent FireEye report. These changes have made Dridex a significant player in the arena of online banking malware. In June, SecurityScorecard, a company dedicated to helping organizations better understand, identify, and mitigate risks to their computer systems, released “The Current State of Banking Malware Q1/Q2 2015.” The report identified 55 malware families, accounting for a total of 11,952 infections at entities in different industries, and found that Dridex recorded the highest number of infections in the manufacturing industry (27 percent of attacks).
“Manufacturing companies often purchase large quantities of raw materials from foreign countries and complete the transactions via wire transfer. Therefore, Dridex wire transfer attacks against a manufacturing company’s corporate business account are more likely to go undetected by banks and businesses. The bank will see a foreign wire transfer for a large amount as a common occurrence and will be less likely to flag it, whereas the business may not notice the missing funds until it is too late.”
This is followed by the retail sector with 20.7%, a finding which SecurityScorecard attributes to the industry-wide use of both the Windows OS and overseas financial institutions for the purchase of wholesale items.
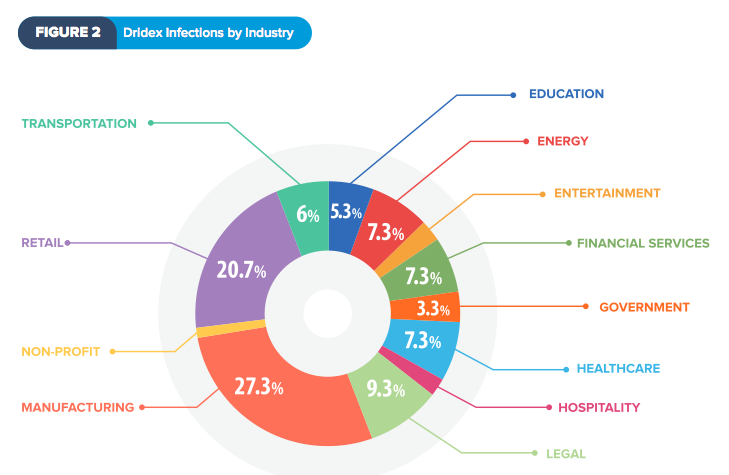
Source: SecurityScorecard Heimdal Security recommends that users never download email attachments from suspicious emails and active two-factor authentication on their online banking accounts whenever possible. For more information on how you can protect you financial data against Dridex and other threats, please read this security guide. Title image courtesy of ShutterStock

