
Recently at its re:Invent 2017 conference, Amazon announced an interesting new security offering called GuardDuty. GuardDuty uses threat intelligence, machine learning and anomaly detection to deliver agentless security findings across a variety of AWS services. This blog will discuss a bit about GuardDuty and show one example of how to gather custom data within the Cloud Management Assessor.
What is GuardDuty?
GuardDuty gathers data from multiple streams, including threat intelligence feeds, and creates a data set that can be compared against DNS logs, VPC flow logs and CloudTrail events. This allows Amazon to report on numerous types of suspicious behavior. Much of this suspicious behavior detection has previously only been found within complex network security products. For example, Amazon will determine if your ec2 host contacts known botnet command and control IP addresses or DNS lookups using DGAs (Domain Generation Algorithms), alerting you to possible machine compromise. Amazon will also log findings in GuardDuty if you have hosts communicating with Bitcoin-related sites. This is useful since many attackers will attempt to mine cryptocurrency if they are able to compromise an AWS host or management account. Other findings are more closely coupled with AWS – for instance, noting suspicious disabling of CloudTrail logs or when credentials generated specifically for an ec2 instance are used from external IP addresses. Obviously, there are a lot of interesting things that can be found by GuardDuty, and the best part is that you can get these advanced security findings without any third-party hardware or software – It’s all built natively into AWS. Now that we’ve learned a bit about the GuardDuty, let’s look at how to use the Cloud Management Assessor to alert you to the existence of high severity GuardDuty findings from within Tripwire Enterprise. You will need to know your GuardDuty detector ID, which can be found with the AWS command line interface command “aws guardduty list-detectors.”
Step 1. Create A Custom Execution Action
On your Actions panel within Tripwire Enterprise, duplicate the AWS – Custom Action and set an appropriate name. In the command line edit box, set an appropriate element name in the element field and use the following in the command field replacing <detector_id> with your own detector id: "guardduty get-findings-statistics --detector-id <detector_id> --finding-statistic-types COUNT_BY_SEVERITY”
Step 2. Create A Conditional Action
Once again on the Actions panel, create a Content Conditional Action. This action allows for performing additional actions based on any data condition.
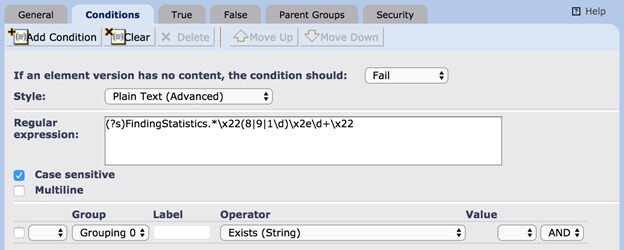
Create a condition to match the content returned by our custom action. This example will match findings with an 8, 9, or 10 severity. On the True tab, add your own response action. You have numerous options here for notifications, but for our example, we’ll use an E-mail action, so we will be notified by email if there are severe findings.
Step 3. Assign Conditional Action To Rule
On the Rules tab, find the AWS – External Rule under Cloud Management Assessor Rules. On the AWS – External Rule Actions tab, simply add the conditional action we created in step two. Now, when we run the Cloud Management Assessor tasks, we will gather GuardDuty finding severity data within Tripwire Enterprise. If there are findings with a severity greater than 8.0, we will be notified via e-email. AWS GuardDuty is a new feature that will likely be changing as more events and options are added. You may need to update your AWS CLI application in order to access this new functionality. Learn how to ensure the secure configuration of your cloud management console here.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

