
Updated 01/29/20 with statement from Zoom spokesperson
Remote conferencing services provider Zoom patched a vulnerability that could have allowed an attacker to find and join active meetings. Check Point explained that the issue stemmed from the way in which Zoom secured certain meetings:
If you use Zoom, you may already know that Zoom Meeting IDs are composed of 9, 10 or 11 digits. The problem was that if you hadn’t enabled the “Require meeting password” option or enabled Waiting Room, which allows manual participants admission, these 9-10-11 digits were the only thing that secured your meeting i.e. prevented an unauthorized person from connecting to it.
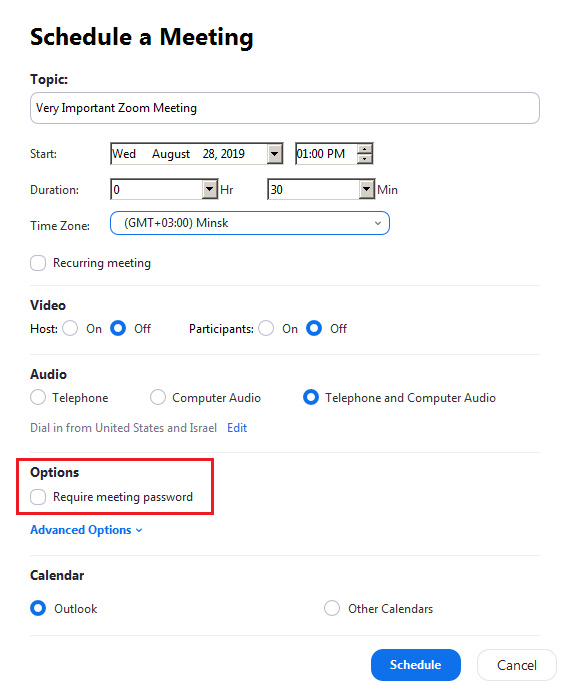
Zoom's meeting scheduling tool with its "Require meeting password" option outlined in red. (Source: Check Point) Researchers at the security firm came up with a list of potentially viable meeting IDs and prepared a URL string for joining the meeting. They then used a "div" element contained in the HTML body of the response returned by accessing this URL to develop a way of verifying the legitimacy of a meeting ID. By automating this approach, Check Point succeeded in predicting about four percent of the randomly generated meeting IDs. These results constituted a much higher success rate than what they could have achieved using manual brute force attacks, the researchers noted. On July 22, 2019, Check Point notified Zoom about the vulnerability in the spirit of responsible disclosure. The remote conferencing services provider responded by re-implementing the meeting ID generation algorithm, instituting a cryptographically strong randomization function, increasing the number of characters in a meeting ID, and forcing users to begin using passwords/PINs/SSO for authorization purposes. A spokesperson for Zoom also issued this statement:
The privacy and security of Zoom’s users is our top priority. The issue was addressed in August of 2019, and we have continued to add additional features and functionalities to further strengthen our platform. We thank the Check Point team for sharing their research and collaborating with us.
News of this vulnerability and its subsequent fix come less than a year after Zoom plugged a security issue that could have allowed an attacker to hijack a Mac user's webcam without their permission by tricking them into visiting a malicious website.

