
Not too long ago, I watched an automobile commercial on television in which the manufacturer placed a huge emphasis on integrity, going on to define the lines of the automobile. I was impressed by this advertisement, so much so that I started looking at all vehicles in a new way. I would walk around the vehicle and look to ensure the spaces between the hood and the fenders were identical, the space between the doors and the fenders were also identical, and that all the parts of that vehicle fit together seamlessly like the stamped pieces of a picture puzzle.
So how do we apply the concept of integrity to our corporate infrastructures today? How do we apply this to computers, network devices, firewalls, databases and application configurations? When IT departments provision new systems for deployment, it’s assumed the integrity is complete and ready for production. How do teams keep it that way?
Guidance from NIST
The Cybersecurity and Privacy Reference Tool (CPRT) supplement to the National Institute of Standards and Technology (NIST) document SP800-53, lists security control 3.19 as “SI-7 SOFTWARE, FIRMWARE, AND INFORMATION INTEGRITY.” The CPRT offers the following guidance and discussion:
- Employ integrity verification tools to detect unauthorized changes to the following software, firmware, and information: [Assignment: organization-defined software, firmware, and information]; and
- Take the following actions when unauthorized changes to the software, firmware, and information are detected: [Assignment: organization-defined actions].
NIST provides a description in this manner:
Unauthorized changes to software, firmware, and information can occur due to errors or malicious activity. The software includes operating systems (with key internal components, such as kernels or drivers), middleware, and applications. Firmware interfaces include Unified Extensible Firmware Interface (UEFI) and Basic Input/Output System (BIOS). Information includes personally identifiable information and metadata that contains security and privacy attributes associated with information. Integrity-checking mechanisms—including parity checks, cyclical redundancy checks, cryptographic hashes, and associated tools—can automatically monitor the integrity of systems and hosted applications.
Integrity is a Foundational Component of Zero Trust
So why are we discussing something so mundane as integrity? Is integrity a deal breaker? Should integrity be a part of my “Zero Trust Architecture” (ZTA)? There is a strong argument to be made that zero trust without integrity as the foundation is not zero trust.”
Zero trust is increasingly becoming an essential element of cybersecurity programs. Those responsible for implementation must have a clear understanding of what ZTA is and how best to implement it for maximum impact.
The Look of Integrity
So, what should integrity encompass in a corporate infrastructure? The diagram below is a non-exhaustive list of the items that must be known within an infrastructure. These are also subject to change regularly as the business requirements shift. As a result, these items must be monitored for known, changed, and updated states. In order to maintain integrity, you must know what you own, how it’s configured, how it’s used, what type of change is normal, and what type of change is abnormal.
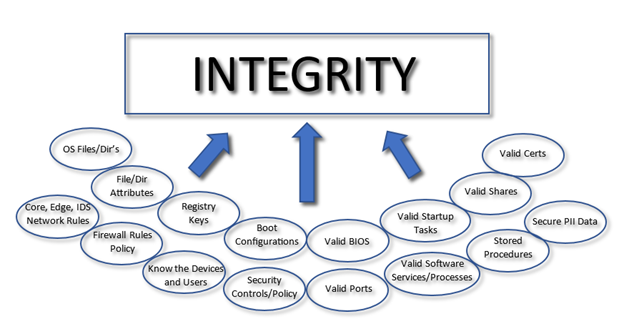
How Tripwire Can Help
Integrity does not just encompass files, better known as File Integrity Monitoring (FIM). As a matter of fact, FIM is just one major aspect underneath the umbrella of integrity, it sits right alongside many other technical aspects of the infrastructure that together make up the whole of what would be known as System Integrity.
Knowing what your infrastructure looks like, how it operates, what and who is valid to be on it, what comes in and what goes out, and who is going where are all extremely important. At all those steps along the way, the integrity of your infrastructure can change.
Fortra’s Tripwire Enterprise (TE) includes the ability to baseline all the above items and then monitor the same for deviation from the baseline, and TE can then take action as dictated by your team. TE collects the who, what, where, when, and how of changes. TE also collects all the event data (footprint) information around any activity that impacts integrity. This footprint information can be forwarded to any SIEM tool of choice to include Splunk, Tripwire LogCenter (TLC), or Alert Logic (AL) for processing.
Fortra’s Tripwire helps to ensure the attack surface that intruders or bad actors want access to, is severely reduced making it very hard to perform any malicious activity without being seen or noticed. With real-time monitoring, regularly scheduled checks, along with reporting and alerting, TE helps to keep the integrity of your infrastructure secure, compliant and free from unknown activity.
At Fortra, we take cybersecurity very seriously, and we prove it by offering a cybersecurity portfolio that is unmatched in the market today.
5 Things Your FIM Solution Should Be Doing for You
Discover the pivotal role of File Integrity Monitoring in maintaining system security and compliance with major standards. Tripwire Enterprise stands out as an advanced solution, offering real-time detection and detailed context for system changes, making it a superior choice for robust cybersecurity.

