Researchers investigating a newly-discovered botnet have admitted that they "accidentally" broke it.
In November, security experts at Akamai described a Golang-based botnet that they had discovered, hijacking PCs via SSH and weak credentials in order to launch distributed denial-of-service (DDoS) attacks and mine cryptocurrency.
The botnet, which the researchers called KmsdBot attacked both Windows and Linux devices, and was seen targeting technology companies, gaming firms, and luxury car manufacturers.
In a follow-up blog post published yesterday, researcher Larry Cashdollar described how the team's deeper examination of the botnet actually resulted in its demise.
As Cashdollar describes, in an attempt to better understand KmsdBot's functionality they sent commands to the bot in a controlled environment, with unexpected results:
"Interestingly, after one single improperly formatted command, the bot stopped sending commands. Naturally, we began an investigation. It's not every day you come across a botnet that the threat actors themselves crash their own handiwork."
It transpired that whoever coded the bot had not put sufficient effort into building an error-checking system that would properly validate commands being sent to it.
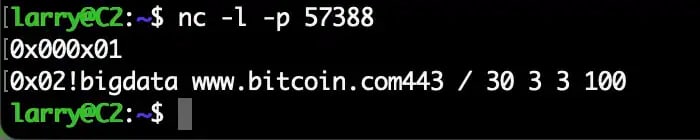
Perhaps the malicious hackers responsible for KmsdBot thought that the only people who would ever send the botnet commands would be careful not to make any typos...
During the testing, we noticed the botnet stopped sending attack commands after observing a single malformed command that arrived. The command: !bigdata www.bitcoin.com443 / 30 3 3 100 A keen observer will notice the lack of space between the target website and the port. The bot doesn’t have error-checking built into its code to verify that the commands are properly formatted.
As a result of entering the malformed command, the botnet crashed. And it had no means of pulling itself up by its own bootstraps, meaning that the only way forward would be for someone to infect the computer again. Yes, a single accidental typo had mitigated the threat.
“This botnet has been going after some very large luxury brands and gaming companies, and yet, with one failed command it cannot continue,” CashDollar concluded.
Humans make mistakes. Programmers (malicious or otherwise) are only human. We can all make mistakes. Those who develop malicious botnets are no different.
On this occasion, we can be grateful that the bad guys did not put more effort into producing secure, stable code. But we should not make the mistake of being complacent, as the rest of us could make mistakes too.
All organisations would benefit from taking a long hard look at their security and following some simple steps to harden their defences.
For instance, to avoid falling victim to a botnet it would be wise to check that none of your servers or apps are using default passwords, and ensuring that nothing is defended with weak credentials. In addition, all software used across your business should be patched and up-to-date, and - to prevent the brute-forcing of credentials - public key authentication for SSH connections should be deployed to help fend off unauthorised access.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

