
Within a matter of hours, an updated version of WannaCryptor ransomware struck hospitals belonging to the National Health Service (NHS), Telefonica, and several other high-profile targets. News of the attacks first broke on the morning of 12 May, when a doctor operating under the pseudonym "B" broke posted the following message on Twitter: https://twitter.com/brobertson2010/status/863016453209038848 Healthcare workers responded to "B's" tweet by providing further details about the attack targeting the NHS. One such commenter named Mike Lightfoot explained that the attack is confirmed to have affected several hospitals in England's national healthcare system. https://twitter.com/MikeLightfoot83/status/863018249369333764 Another added Essex. Yet another named Lincoln. Doctors and hospitals have also been writing in to describe the damage the attack has done to their institutions' systems. A message from one doctor sheds some light on the nature of the incident. As quoted by The Guardian:
"So our hospital is down … We got a message saying your computers are now under their control and pay a certain amount of money. And now everything is gone."
Locked computers? A ransom demand? It sounds like ransomware. This isn't the first time a hospital has suffered a ransomware attack. In February 2016, Hollywood Presbyterian Medical Center temporarily shut down its IT systems because of a Locky ransomware attack. The facility diverted patients to other facilities for treatment and shut down several departments before ultimately deciding to pay the ransom of 40 Bitcoins (approximately $17,000 USD at the time). More than a year later, it appears East and North Hertfordshire NHS is responding to this attack in a similar fashion. As quoted in a statement provided to The Register:
"Today, the Trust has experienced a major IT problem, believed to be caused by a cyber attack. "Immediately on discovering of the problem, the Trust acted to protect its IT systems by shutting them down; it also meant that the Trust’s telephone system is not able to accept incoming calls. "The Trust is postponing all non-urgent activity for today and is asking people not to come to A&E - please ring NHS111 for urgent medical advice or 999 if it is a life-threatening emergency."
The IT teams at East and North Hertfordshire NHS are currently working to address the issue. East and North Hertfordshire NHS isn't the only hospital to shut down its systems, either. https://twitter.com/DCHStrust/status/863034592613322753 Several hours after news of the attack first emerged, the National Health Service released a statement regarding its hospitals' recovery efforts:
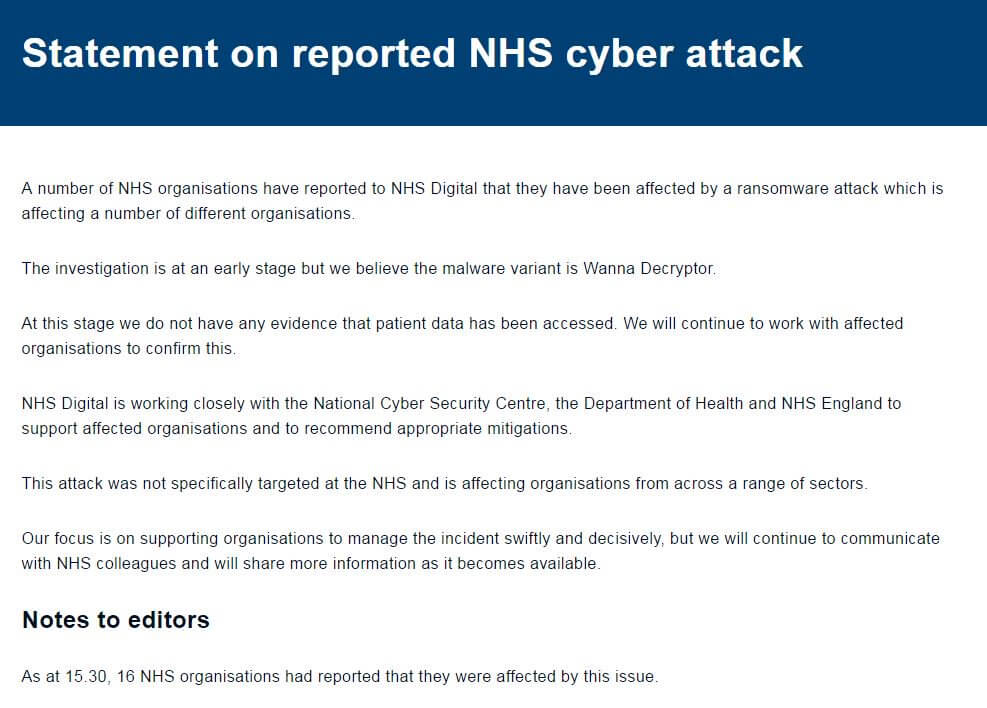
Source: BBC News
"A number of NHS organizations have reported to NHS Digital that they have been affected by a ransomware attack which is affecting a number of different organizations. "The investigation is at an early state but we believe the malware variant is Wanna Decryptor. "At this stage we do not have any evidence that patient data has been accessed. We will continue to work with affected organizations to confirm this."
Wanna Decryptor, aka WCry, WannaCry, and WannaCryptor, is a type of ransomware that's been in circulation since at least 10 February 2017. On 12 May, an independent security researcher named MalwareHunter discovered a new version of the malware. Since then, the ransomware has taken off. https://twitter.com/malwrhunterteam/status/862988042231054338 NHS notes in its statement "this attack was not specifically targeted at the NHS and is affecting organizations from across a range of sectors." Indeed, earlier in the day, news emerged in El Mundo that WannaCryptor had infected 100 computers at Telefonica, Spain's former state telecommunications company. The ISP, which instructed its employees to turn off their computers and disconnect from the internal Wi-Fi network, confirmed the attack in a statement:
"Earlier today Telefónica detected a cibersecurity incident affecting the PC's of some employees within the company's internal corporate network. Telefónica inmediately activated the security protocols for this type of incident in order to resolve the problem as soon as possible."
According to International Business Times, the attackers have demanded that the company pay the ransom fee of approximately 300 dollars by 15 May. If not, the attackers will raise the price. Should they not receive payment by 19 May, WCry's handlers said they'll delete the encryption key.
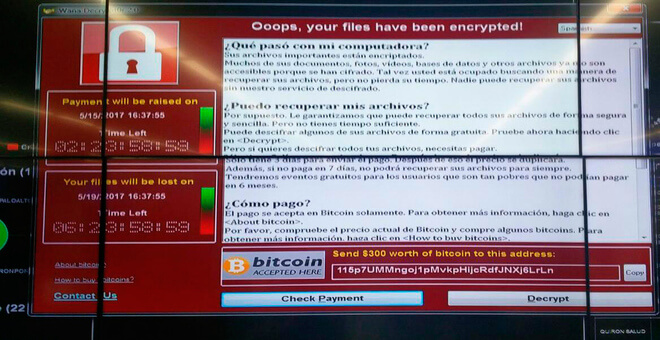
WCry decrypter on a computer screen (Source: El Mundo) In addition to Telefonica, El Pais received reports on 12 May indicating the ransomware has affected other companies in Spain including consultancy firm KPMG, banks BBVA and Santander, power company Iberdrola, and telecoms giant Vodafone. None of those companies confirmed the attack had infected their systems at the time of publication. Alternatively, you can find out more about the malware's operation and how you can prevent a similar attack here.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

