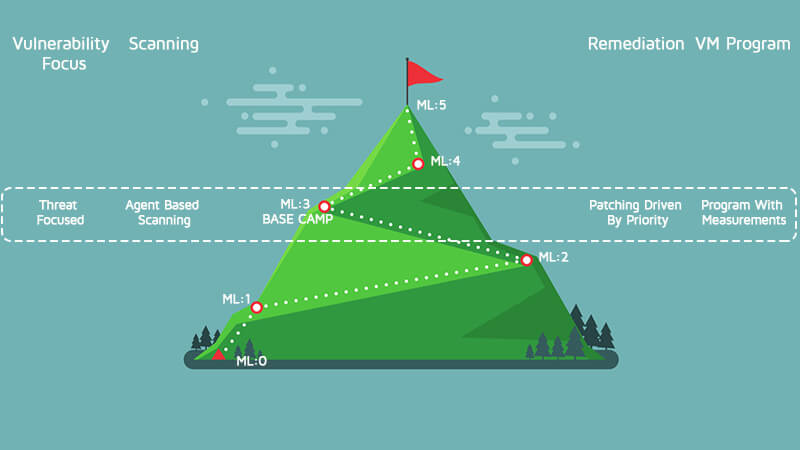
ML:3 is base camp, and getting here means you have reached a level that others have only dreamed about. At this level, the VM program is very good, and your visibility into threats to the environment is much better than it has ever been.
Prioritizing Asset Assessment
The biggest change at this level is the focus on the breadth of assessment going on in the organization. The goal at this point is to increase the coverage of assessed assets at least monthly. While it would be great to assess everything, it is not always practical, so the priority of the asset will determine the cadence. For example,
- External facing Critical Assets - If compromised, will stop the business – assessed at least once every day
- Non-external facing Critical Assets – if compromised, will stop the business - assessed at least every three days
- Important Assets – if compromised, would cause an outage in the business – assessed at least every five days
- Standard Assets – these are the assets that generally have one user, e.g. workstations and laptops. – assessed at least every 10 days
- Low Priority Assets – these are assets like would cause a nuance if compromised, e.g printers.
The cadence of patches can also play a role in these assessment times, as mentioned in the last blog.
Asset Assessment Categories
With this increased coverage, a variety of assessment technologies are used to cover the organization. Scanning is generally broken down into three categories. The category to use depends on the assets in scope.
- External assessments or remote checks – These assess the vulnerability of a system without logging into the system. This style of checks will send packets to the target and determine vulnerability status based on the reply from the target.
- Internal assessments or local checks – These use credentials to log into the asset and determine a vulnerable state by checking items like file versions, configurations, rpm versions, registry keys, etc. These require elevated system access on each asset to perform correctly.
- Agent-based checks – These perform like the local checks, but instead of logging-in to an asset, the agent runs assessments locally on a cadence. The agent runs with elevated privileges, so there is no need to manage passwords, and this is good for transient assets that may not be on the network at the time of a scheduled scan.
At this stage, the Vulnerability Management Program is more advanced, and metrics are being created and tracked. The remediation patching is being driven by the threat to your environment. Use threat intelligence supplied by your vendor or a third party as an input to remediation priority. Remember that not all vulnerabilities are exploitable, so use this data along with the asset classification to prioritize the order of remediation.
Tracking Associated Metrics for Base Camp
It is time to start tracking some program and environment metrics. At this point, just tracking them to determine any trends is useful. They will be used to extend the program later. Some metrics to consider for base camp are:
- Percentage of Coverage across the organization – What percentage of the organization is currently assessed? Use this to determine how to close the gap, and make sure this percentage is not dropping.
- The number of Truly Critical Vulnerabilities – This is based on the risk score mentioned above. A numeric scoring system allows for the creation of a high-water mark so that any issues that score above the line can be remediated imminently.
- Mean Time to Resolution (MTR) – How long does it take on average to remediate a vulnerability? Is this getting lower or higher?
- Time to Detect – How long did it take to discover a new vulnerability once it was introduced? For instance, when a new vulnerability was introduced due to the installation of a new application, whether it was detected in minutes, hours, days, weeks, etc.
The Only Way is Up from Base Camp
Now take some time to celebrate. Getting to ML:3 aka Base Camp is no small feat and is something many organizations strive for and may never reach. The view is great, and you will spend some time here acclimatizing your organization to these new policies and metrics. The climb will continue, but it will not get any easier, so make sure everyone is ready before we take up the trail again.
FURTHER READING ON CLIMBING THE VULNERABILITY MANAGEMENT MOUNTAIN:
- Climbing the Vulnerability Management Mountain
- Climbing the Vulnerability Management Mountain: Gearing Up and Taking Step One
- Climbing the Vulnerability Management Mountain: Taking the First Steps Towards Enlightenment
- Climbing the Vulnerability Management Mountain: Reaching Maturity Level 1
- Climbing the Vulnerability Management Mountain: Reaching Maturity Level 2

