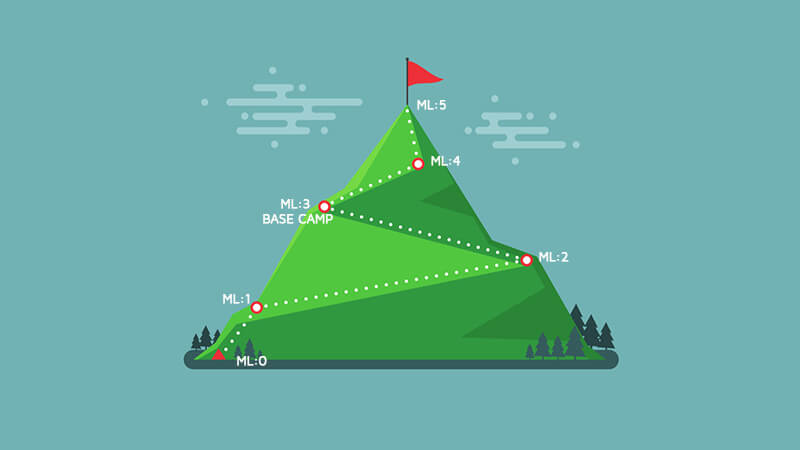
As I discussed in the first blog in this series, the purpose of this series is to guide you on your journey up the Vulnerability Management Mountain (VMM). Like climbing a mountain, there is a lot of planning and work required, but when you get to the top, the view is amazing and well worth the journey. For the first phase, let's start by planning the trip up Vulnerability Mountain. When you get ready to climb a mountain, you need gear, and you need to know what to ask for at the store. If you are not educated, you can easily wind up with a bunch of gear, products and plans that do not work together and thus expand your risk. We will start by defining some of the terms we will be using so we can speak the same language. Vulnerability – A vulnerability (from RFC 4949) is A flaw or weakness in a system's design, implementation, or operation and management that could be exploited to violate the system's security policy. Asset – The idea of an asset has changed over the years and has evolved from being physical hardware like servers, desktops and network gear to any device (virtual or physical), object, device or other component in a network or environment. This now includes laptops, containers, serverless code and even IoT devices. Vulnerability Assessment – The process of identifying a vulnerability in a network or environment. This assessment is a look at the state of your assets at a single point in time. This assessment can be done by an assessment tool or by a manual pentest. Remediation – The process of fixing, stopping or working around a vulnerability. Remediation can be done by applying a patch, changing a configuration or even blocking exploit attempts with a network device. Vulnerable – An asset that is vulnerable has a known vulnerability. An asset that is vulnerable does not have to be exploitable to be vulnerable. Even if there are remediations in place, an asset with a vulnerability is vulnerable until the vulnerability has been fixed or patched. An asset is vulnerable but not exploitable if the vulnerability cannot be exploited due to other factors like configurations or security controls.
The Vulnerability Maturity Model is our Map of the Mountain
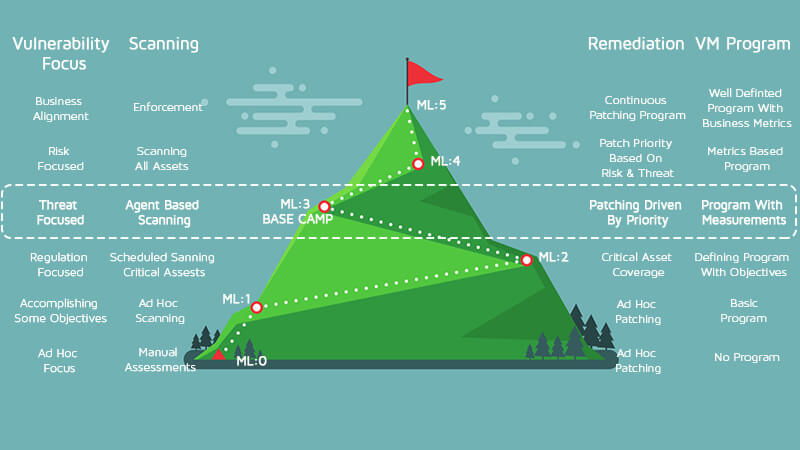
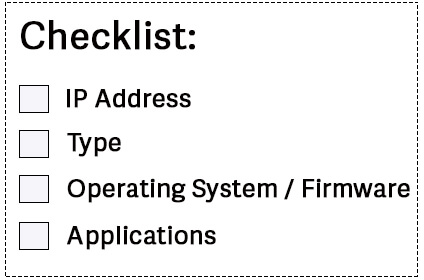
From here, determine where you are on the climb. It is probable that you are more advanced in some areas than others, but you are not able to advance to the next level until you have satisfied all items in the current level. Your last preparations will be to inventory, your gear or assets in our situation. Figuring out what assets are in your environment seems like it would be an easy thing to do at first, but it always ends up becoming hard to answer, especially when you consider BYOD, cloud assets and virtual assets like container and VMs. If you have a Configuration Management Database (CMDB), is it up to date? Your best option is to use a tool to do an in-depth scan of your network. Your tool should scan every IP address on your network and return the needed information about your assets. At a minimum, you should have:
When you start assessing your environment for vulnerabilities, it will be much easier if you break this up into manageable sections. This can be done by asset type, geolocation, owner, purpose, etc. There is no right way to do this, so look at your environment and make the decision. You just took your first step on the climb. Congratulations! Next, we will make it to our first checkpoint ML:0.
FURTHER READING ON CLIMBING THE VULNERABILITY MANAGEMENT MOUNTAIN:
-
- Climbing the Vulnerability Management Mountain
- Climbing the Vulnerability Management Mountain: Gearing Up and Taking Step One
- Climbing the Vulnerability Management Mountain: Taking the First Steps Towards Enlightenment
Mastering Security Configuration Management
Master Security Configuration Management with Tripwire's guide on best practices. This resource explores SCM's role in modern cybersecurity, reducing the attack surface, and achieving compliance with regulations. Gain practical insights for using SCM effectively in various environments.

