Just as you would map a hike or climb by creating waypoints you plan to hit each day, you must plan your vulnerability management process by creating similar goals. We call these goals Maturity Levels, from ML0 to ML5, as we defined them in the last blog. You have your asset inventory from an open-source tool, asset tracking database or maybe your preferred vulnerability assessment tool. Now it is time to climb to the first waypoint ML0 ML0 may be the hardest waypoint to hit because to get here you are starting from pretty much nothing and doing a lot of manual work. As a climber progresses up a mountain, they will get used to the environment and rigor, thereby becoming faster and stronger. The same is true when climbing the Vulnerably Mountain; speed and strength will come in the form of automation, integration and well-defined processes. Look at the asset inventory. How do you decide which systems to focus on first? Is it the DMZ, code repositories or even the CEO’s laptop? The urge here is to try to assess everything, but if you are using a vulnerability assessment tool or a pentesting team, you will likely get way too much information to be actionable, and the cost can be quite high to pentest of this large scope. Pick your targets wisely thinking of:
- Company value
- Ease of remediation
- Staffing and owners
- Change control windows
- Can the asset be restored from a backup if compromised?
- Is the asset under a maintenance contract so that I can get patches?
- Are there any mitigations in place (IPS, network/host configurations, etc.)
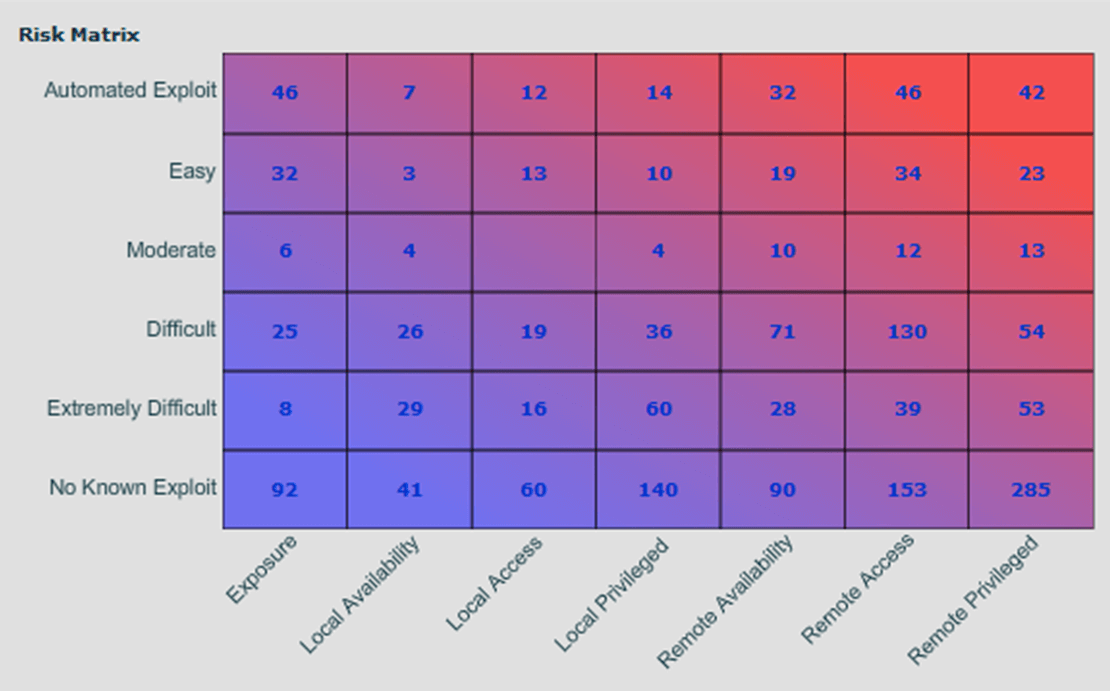
This is a balance of business and security goals. For instance, if the next change control window for servers in the DMZ in three months away, it is probably not the best place to start because of all the wasted time between the assessment and when changes can be made. On the flip side, these systems might be the highest value to your company, so having an assessment of these systems would give a good view of their status. This view may also show the need for an emergency change control window to remediate a critical exploitable vulnerability. There is no best place to start for every organization. It depends on your goals. Once you get your report from a manual pentest or a product vulnerability scan, it is time to prioritize the results. The tool or consultant may have sorted the vulnerabilities by Critical, High, Medium, Low or CVSS. The problem here is that the scores will clump up into big groups, so which of the 50 critical vulnerabilities is the most critical? CVSS is better, but they still group up, thus making it hard to pick the most important one. A good Vulnerability Management product will sort the results in a logical, more granular manner. If you are having trouble deciding where to start, pick the most important asset and then look at the vulnerabilities on it. Sorting the vulnerabilities by ease of exploit and risk will give you the best results. The vulnerabilities that are the easiest to exploit and give the most access to the system are the ones that pose the highest risk.
Now you just read the remediation information for the vulnerabilities and apply accordingly. This can be done by applying patches or making configuration changes on the host or network. Congratulations, you have reached ML0.
FURTHER READING ON CLIMBING THE VULNERABILITY MANAGEMENT MOUNTAIN:
- Climbing the Vulnerability Management Mountain
- Climbing the Vulnerability Management Mountain: Gearing Up and Taking Step One
- Climbing the Vulnerability Management Mountain: Taking the First Steps Towards Enlightenment
Mastering Security Configuration Management
Master Security Configuration Management with Tripwire's guide on best practices. This resource explores SCM's role in modern cybersecurity, reducing the attack surface, and achieving compliance with regulations. Gain practical insights for using SCM effectively in various environments.

