
Researchers have discovered that malicious actors leveraged the TRITON framework at a second critical infrastructure facility. In this particular attack, the threat actor maintained access to the target corporate networks for nearly a year before gaining access to the Safety Instrumented System (SIS) engineering workstation. They remained relatively quiet all the while as they worked to access the OT network. FireEye reveals as much in its threat analysis of this previously undisclosed attack:
They did not exhibit activities commonly associated with espionage, such as using key loggers and screenshot grabbers, browsing files, and/or exfiltrating large amounts of information. Most of the attack tools they used were focused on network reconnaissance, lateral movement, and maintaining presence in the target environment.
The threat actor used multiple techniques to avoid detection. In some cases, for instance, they renamed their files to look like legitimate ones. In other cases, they deleted their dropped attack tools and execution logs after they finished with them. After gaining access to the SIS engineering workstation, the attacker focused much of their effort on refining and delivering a backdoor payload using the TRITON attack framework. They also interacted with all target controllers during off-hours in order to further avoid detection.
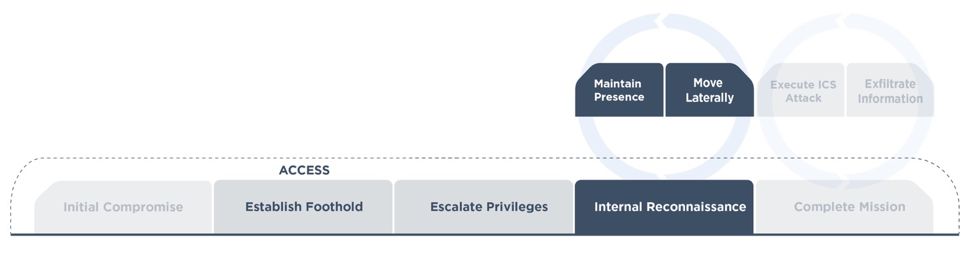
The targeted attack lifecycle, as observed by FireEye This infection chain is consistent with that which the threat actor used in their first documented attack. In that campaign, the malefactor could have used the TRITON attack framework to shut down the targeted plant. Instead they leveraged it to upload malicious code to the organization's SIS controllers. Only a flaw in the attack code's prevented the actor from achieving some outcome beyond a process shutdown. This latest attack highlights how industrial organizations need to protect their IT and OT environments against sophisticated threats like TRITON, Industroyer and Stuxnet. As part of this process, organizations should consider investing in a sophisticated solution that can help them assess their environments for ICS security risks and secure their endpoints. Learn how Tripwire can help.

