
When we speak of necessary evils, some images readily spring to mind. A dental appointment, automobile insurance, and many others. In cybersecurity, audits fit this image quite well. There are many uncomfortable aspects of audits, including the need to maintain accurate records, as well as finding the time to perform all the work required to satisfy the auditors.
Deep down, we all know that audits are necessary. After all, we want to think that our systems are as secure as we say they are. All of the hard work, the due diligence, the checking and double-checking assures us that everything is up to its best level. However, the discomfort of proving that we have done what we say we have is where many characterize the audit process as pure evil.
While it is easy to worry that an auditor may give us a low grade, the stress is increased when your industry is one that tolerates zero down time. The industry that immediately comes to mind is the electricity sector. This is one of the three members of the Energy Sector in the United States. This is an industry that is expected to provide uninterrupted service, regardless of all imaginable conditions. When the power goes out, it is often headline news.
The standards for operating efficiency are set forth by the North American Electric Reliability Corporation Critical Infrastructure Protection (NERC CIP), which, while referred to as standards, are actually requirements, with the power of law to enforce them. This is one of those rare times when a standard is actually supported with regulatory muscle.
Key Challenges of Preparing for a NERC CIP Audit
Some of the key challenges with preparing for a NERC CIP audit resemble that of any other type of audit; gathering all the evidence in time for the audit review. Evidence is usually stored as documents, or spreadsheets, of which the audit team can sort through to satisfy the compliance checklist. Even the best curated evidence often sends evidence producers into a mad scramble when the auditors request more information.
Even though an audit can be scheduled 90 days in advance, when one considers the legions of assets in an environment, it is easy to see how fast an audit deadline can creep up on an organization. The NERC CIP audit criteria are quite detailed:

Tripwire and Towerline
Fortunately, there is a tool that can ease the burden of the NERC CIP audit process. Tripwire, in conjunction with Towerline, can eliminate much of the anxiety associated with the NERC CIP audit process.
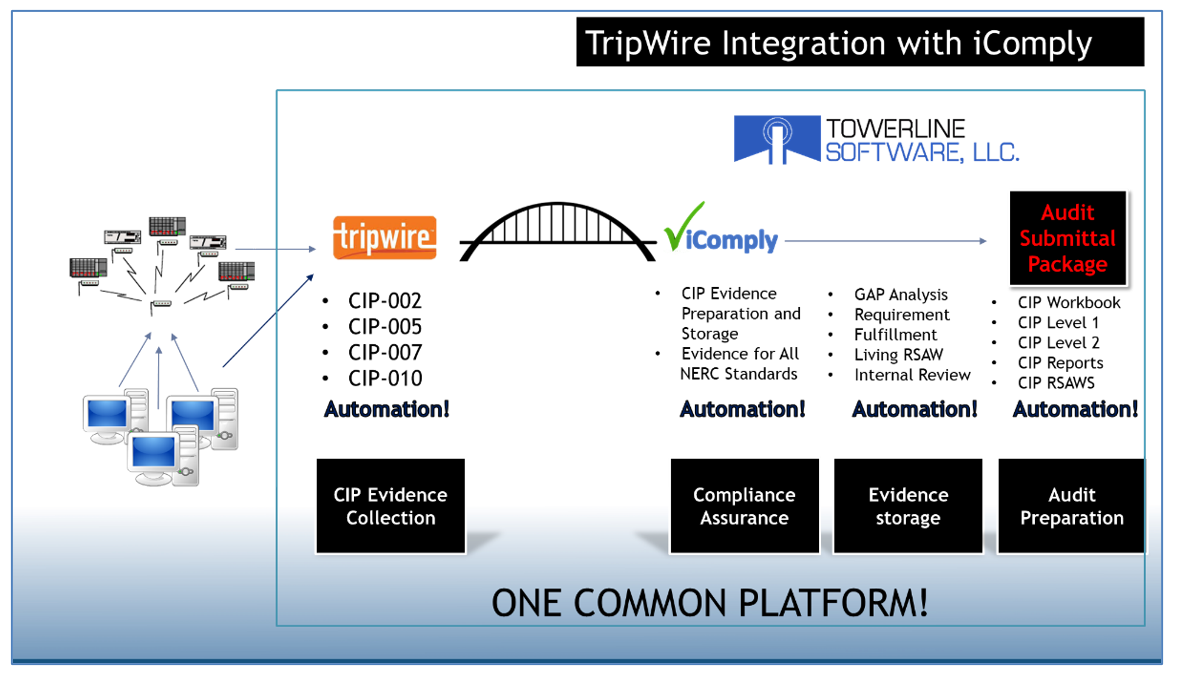
One of the most important elements of understanding a system is the ability to know how everything is interconnected. An accurate mapping is essential to meeting this goal. Some preparation is required to get to that point. Towerline software pulls the data from Tripwire to show the unmapped assets. Unmapped assets are a problem, representing a gap in an organization’s evidence. Once these assets are revealed, the old method of manually tracing the asset becomes a detective game. Once the correct mapping location is found for the orphaned asset, associating it into its location in the environment can create significant problems for all of the previous audit documentation.
With a simple drag and drop, a previously unmapped asset can be moved to its proper location. It's a big tree structure, but when you're done, the software knows everything about the system. It knows where all the data is, and it knows how to get it with the press of a button. It does it not only with the press of a button, but it does this automatically, retrieving the data and presenting it in a usable form. This also causes the respective reporting documentation to be updated accordingly.

Another important aspect of any audit is assigning responsibility for each task. The Towerline software includes built in alerting, so if a person has something that is due, all the responsible parties can be notified of the upcoming deadline.
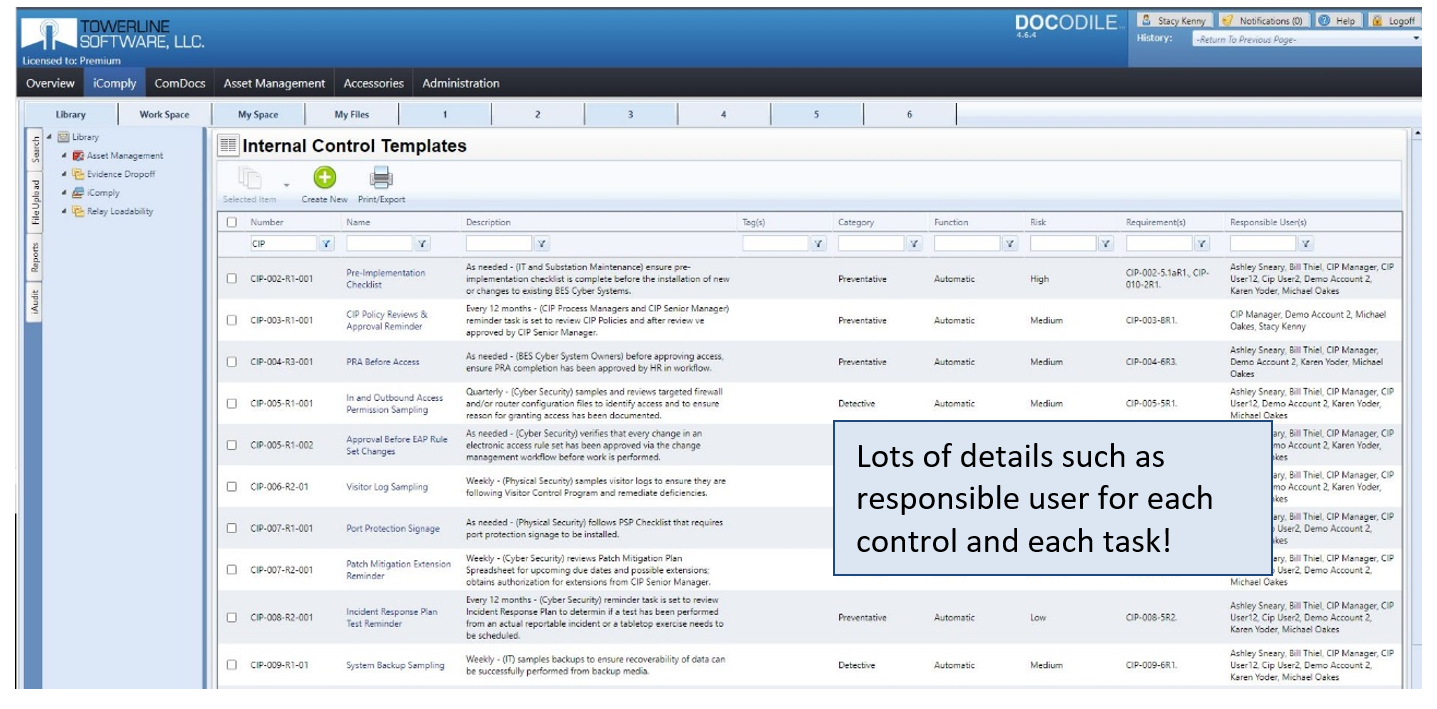
The bridge between Tripwire and Towerline eliminates the old spreadsheet method of tracking audit items. It also enables granular control, so if an auditor wants just one field of information, it is easy to present that information. What makes a NERC CIP audit more vexing than any other IT audit, is that the information must be presented in a specific format. Towerline includes a module to organize the relevant information into Reliability Standard Audit Worksheets (RSAWs).

Auditors love automation. With Tripwire and Towerline, automation is built in, making the NERC CIP audit process smoother for your organization.
For more information about how Towerline and Tripwire Enterprise can help support your business, contact us today.
About the Author:
Thomas Adams is the owner and president of Towerline Software, LLC, which specializes in compliance software, as well as the owner and president of Epoch Technical Solutions, LLC, which specializes in technical consulting. He is an electrical engineer with a lifelong involvement in the electrical energy industry, having worked both as an employee and consultant to electric utilities. He has extensive experience supervising, designing, and project managing just about everything relevant to the design, operations, and oversight of electric utilities, mainly focusing on grid integrity and safety including North American Electric Reliability Corporation (NERC) compliance program development and implementation. He has participated on the NERC Distributive Generation Resources Standards Drafting Team tasked with the development of several NERC standards and requirements. He is also the author and designer of relevant Internal Controls, Compliance and Critical Infrastructure Protection (CIP) software.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
Achieving Resilience with NERC CIP
Explore the critical role of cybersecurity in protecting national Bulk Electric Systems. Tripwire's NERC CIP Solution Suite offers advanced tools for continuous monitoring and automation solutions, ensuring compliance with evolving standards and enhancing overall security resilience.

