
A new type of ransomware is encrypting victims’ video game files in addition to targeting other documents stored on their computers. According to Bleeping Computer, the ransomware strain, dubbed “TeslaCrypt,” was first discovered by Fabian Wosar of Emsisoft earlier this year. TeslaCrypt mimics other ransomware, including CryptoLocker, in that it uses AES encryption to lock victims’ files, at which point it demands a ransom payment in exchange for providing victims with the decryption key. What distinguishes TeslaCrypt is its ability to target files that are related to at least 40 different video games, including Call of Duty, World of Tanks, and Dragon Age. This new ransomware also allegedly seeks out files that are related to tax returns and personal finance, and it has the ability to locate these files stored on network devices.
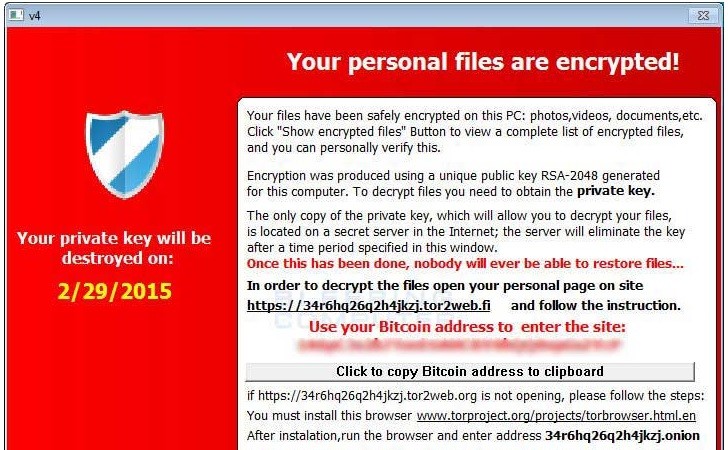
Users infected with TeslaCrypt are asked to pay a ransom of 1.5 Bitcoins, which amounts to between USD $400 and $500, depending on the BTC value. In a departure from other types of ransomware, TeslaCrypt gives victims the option to pay the ransom using two PayPal My Cash Cards. But selecting this payment option raises the ransom to USD $1,000. To facilitate the ease of ransom payments, victims are directed to install the Tor Browsing Bundle shortly after infection. They can then use Tor to access a hidden service technical support site should they have any difficulty paying the attackers. Earlier this month, Bromium Labs reported that a compromised web site is using a Flash chip to redirect users to the Angler Exploit Kit, which is distributing the TeslaCrypt ransomware. Many analysts today consider Angler the best exploit kit on the market due to its widespread and sophisticated nature, including its use of “Domain Shadowing” to evade detection. Victims who are affected by TeslaCrypt are encouraged to not pay the ransom. To learn more about how you can remove ransomware from your computer and how you can protect your computer from this type of malware, please click here.

