
What's happened? An almighty furore has kicked off after it was discovered that for months Lenovo has been shipping PCs and laptops with software pre-installed that could compromise your security and privacy. What software? It's called Superfish, and it inserts adverts into webpages such as Google search results. In January, a Lenovo forum administrator responded to customer complaints about Superfish by describing its functionality like this:
"To be clear, Superfish comes with Lenovo consumer products only and is a technology that helps users find and discover products visually. The technology instantly analyzes images on the web and presents identical and similar product offers that may have lower prices, helping users search for images without knowing exactly what an item is called or how to describe it in a typical text-based search engine."
That sounds like adware? Yes, it does. At the very least it's a potentially unwanted program (PUP), but there are other concerns beyond Superfish's insertion of adverts. What concerns? Superfish installs a self-signed root certificate that can intercept HTTPS encrypted traffic for each and every website you visit. In other words, encrypted traffic is being intercepted so ads can be shown on Lenovo customers' computers. Surely no-one should be able to see my encrypted communications? Correct. The Superfish adware installed by Lenovo is effectively conducting a "man-in-the-middle attack", and can crack open your secure communications - all so they can display some irritating adverts. It does this by replacing legitimate site certificates with its own. But Lenovo wouldn't spy on my communications, would it? They're not secretly snooping at my private activity online? Almost certainly they're not interested in that. They just want to inject money-making ads in front of you. But the way in which they have done it is cack-handed, and could be exploited by a malicious hacker to intercept innocent the traffic of innocent parties. That sounds bad. You bet it's bad. If you have Superfish on your computer you really can't trust secure connections to sites anymore. For instance, take a look at the fake certificate affected Lenovo users see when they visit the Bank of America website. It is signed by Superfish, not Bank of America.
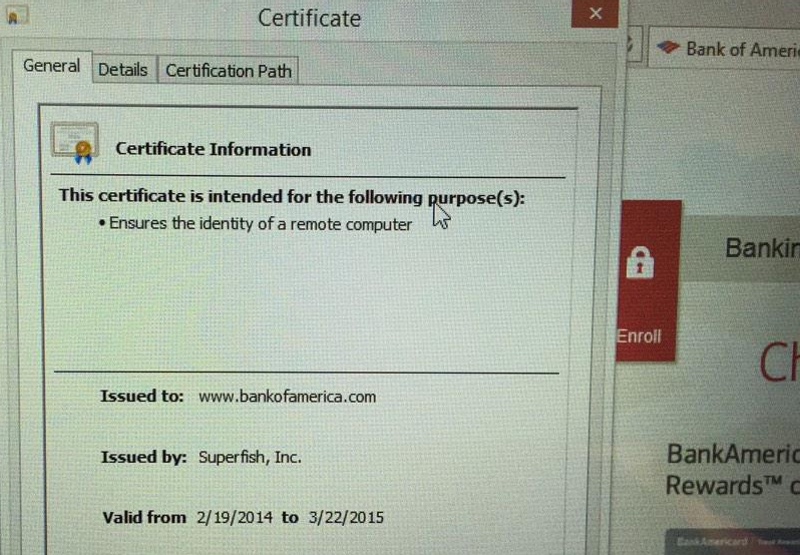
As security researcher Marc Rogers points out, users aren't told that the legitimate site certificate has been meddled with, has expired, or is bogus. Furthermore, Superfish appears to use the same certificate on all installs - making it a huge security vulnerability, and your PC utterly untrustworthy when it comes to activities such as online banking.
This presents a security nightmare for affected consumers.
- Superfish replaces legitimate site certificates with its own in order to compromise the connections so it can install its adverts. This means that anyone affected by this adware cannot trust any secure connections they make.
- Users will not be notified if the legitimate site’s certificate has been tampered with, has expired or is bogus. In fact they now have to rely on Superfish to perform that check for them. Which it does not appear to do.
- Because Superfish uses the same certificate for every site it would be easy for another hostile actor to leverage this and further compromise the user’s connections.
- Superfish uses a deprecated SHA1 certificate. SHA1 has been replaced by SHA-256 because attacks against SHA1 are now feasible with ordinary computing hardware. This is insult on top of injury. Not only are they compromising peoples SSL connections but they are doing it in the most cavalier, insecure way possible.
- Even worse, they use crackable 1024-bit RSA!
- The user has to trust that this software which has compromised their secure connections is not tampering with the content, or stealing sensitive data such as usernames and passwords.
- If this software or any of its control infrastructure is compromised, an attacker would have complete and unrestricted access to affected customers banking sites, personal data and private messages.
Okay, okay. I get the message. What is Lenovo saying about all this? At the end of January, following customer complaints on its forum, Lenovo said it had "temporarily removed" Superfish from computers it sold. It said it was doing this because of "some issues (browser pop up behavior for example)". However, that doesn't appear to help people who had already bought Lenovo PCs with the Superfish adware, or anyone who goes into a store today and buys one that has been sitting on the shelf for a month or two. Sheesh. How long has this been going on for? Since at least mid-2014. Complaints have popped up from time to time from Lenovo customers, but in the last 24 hours the story has become a hot topic in security circles. Now the story has reached the ears of the security press, we hope Lenovo will take the problem more seriously. How do I remove Superfish? Unfortunately it appears that simply removing Superfish from your computer does not also zap the associated root certificate. That means your computer remains vulnerable. Microsoft has published a step-by-step guide about how to remove and revoke root certificates that you can follow. In addition, Microsoft has published a list of the official root certificates that are needed for Windows - to make sure that you haven't had anything else sneakily added. If you're still worried then, well... you’ve got a backup of your important data, right? Maybe the simplest thing to do is wipe your hard drive and install a clean, fresh, uncompromised version of Windows (or other operating system) onto your Lenovo computer – instead of the one they gave you. It’s a brutal response, but it’s probably the only one you can completely trust right now. It took the security community over six months to notice what Lenovo was doing on its PCs, who knows if it's doing anything else a bit dodgy too...
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

