
A year ago, I wrote an article entitled Starting Your Career In Information Technology. As your career goes on, you may find yourself traveling down different routes than you originally planned. This article is a follow-up, designed to give an idea of what cyber security has become for me after I transitioned to it from networking. To begin, I was self-taught. I started out as a system administrator and IT manager. Later, I went to college to learn about Cisco and network architecture. Eventually, I found myself looking more and more at the following question: "Well, now that I’ve deployed that network, what happens next?"
Differences between IT & IS
There’s a huge difference in the skill sets required for the technology field, information technology (IT), and information security (IS or cyber security). Below, I’ve generalized three typical departments you may find in an office:
- Cyber Security Consultants: Their job is to remain on top of the latest technology advances, be aware of the world news in both technology and general subjects, and constantly ask "what’s next?" Often research and development also fall here.
- Internal Cyber Security: Internal cyber security is required to keep on top of news/world events just as consultants do, but additionally, they help to maintain the IT infrastructure and strengthen the human firewall.
- Technical Support: These are people who provide support to users for when technology malfunctions, standard builds and more.
The importance of separate departments
Cyber security is a vast subject, covering many different types of tasks and skills; you may know a bit of each topic, but you cannot master everything. We all have different skills and learn in different ways; we are motivated separately and enjoy different aspects of technology. This factor is what enriches cyber security.
“If you do what you love, you’ll never work a day in your life.” –Marc Anthony
I’m sure you’ve heard this quotation before. This, to me, applies greatly to cyber security and even information technology. As techs, we often are found playing around with gadgets and get excited over the next best thing. We also enjoy attending or speaking at conferences because our hobby tends to be what we do. The reality is that cyber security is a lot of hard work; it can be long hours at the office and require many spur-of-the-moment decisions. To balance these demands, you must have foundational knowledge along with an ability to adapt to each situation quickly. The best techs I know do what they do because they enjoy it. We all come into cyber security from different backgrounds. I came through network architecture while many others came from application development or web development. But what’s the best way to enter Cyber Security?
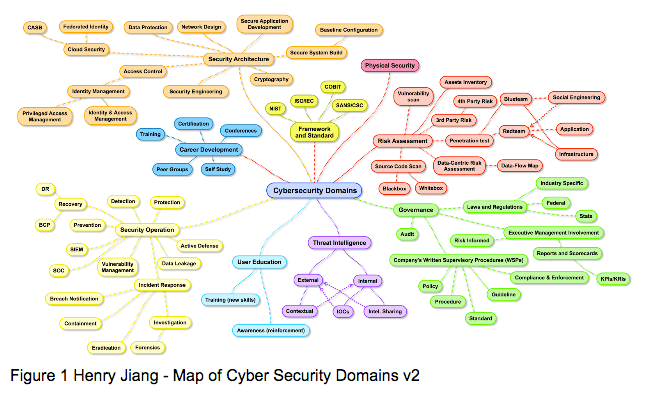
https://twitter.com/MiddleSiggy/status/836282304276414464 I agree with building foundations. You need to understand the basics to be able to create complex solutions. Please be aware that networking isn’t the only way to get into cyber security. https://twitter.com/lnxdork/status/836245821100343298 Just like in software development, you need to consider cyber security regarding how it applies to every aspect of the business, from architecture to deployment, from sustaining the infrastructure to deciding on the standard build of users experience. At my work, cyber consultants, internal cyber, IT ops, risk and compliance, and partners all work together closely when making decisions on what direction to go in. The internal cyber awareness program is designed with users in mind, focusing on their motivators and teaching skills that they can apply directly to their jobs. https://twitter.com/AndrewConway/status/836282911036956673 I love this quote. Truly, it covers what I want you to take away from every training experience; every interaction with me and my team, every part of my job. Our users are the cyber defense team. They're our human firewall, a role which our techs share. Working together, we can all make our jobs and lives better by understanding what the threats are and knowing that each of us is responsible for making our environment secure. Our job as cyber security is to be supportive to users, so they can feel safe asking questions and thereby feel motivated to learn. https://twitter.com/hardwaterhacker/status/836247088329535492 https://twitter.com/hardwaterhacker/status/836247387370745856 Learning for me is hands on; when I wanted to learn Python, I built a lab Network Configuration Management system that reads in SysLog to track all config changes on my lab environment. https://youtu.be/VwNpbRoL-MQ When I run training at my work, I use hands-on learning to teach users hacking skills on attacks that commonly are brought against them so they can better recognize when they’re being targeted. https://twitter.com/Maliciouslink/status/836286914093252610 As Jerry notes, you need to start out small. Going back to the map of cyber security domains above, you can very easily be overwhelmed with the number of things you may be expected to master starting out. The thing is it’s okay to say you don’t know. Learning is ongoing and fluid; you learn one part then focus on another. Later, go back and realize you had it all wrong. https://twitter.com/ccie5022/status/836348678470250496 Although you might laugh a bit on this, Bill makes an important point: using the right tools for the job is vital. When we learn and explore, we want to make sure we aren’t creating vulnerabilities in our environments. One reason we separate development and production environments is to push changes out to the development environment and see if it breaks anything. Our laptops are the same. When learning how to recognize phishing emails or malware analysis, make sure you’re keeping your system safe along the way. Follow guides and tutorials online, malware analysis labs, or capture the flag (CTF) exercises in virtual environments that will not affect your system. https://twitter.com/ownageinc/status/836336033373499392 https://twitter.com/pjarmstrongaz/status/836331544646070272 At the end of the day, there are many different aspects of cyber security; it is impossible for anyone to be an expert in all the different parts. And honestly, we wouldn’t want anyone to be! Cyber security is the process of layering on different technical controls and awareness training to build a strong human firewall. We need a variety of viewpoints. We need a variety of skills to build our layers of security. And we need a variety of people. Pursue your passions whatever they may be, as that will allow you to progress further. Continuously motivate yourself to learn more, and allow for more secure environments.
Certifications
Finally, certifications. Certifications tend to be a big debate on value vs cost when it comes to what you’re learning and how much that helps you with actually getting the job. From my experience, certifications look great on a CV (resume), but so do different experiences and lab environments at home. There’s a critical balance to gaining certifications vs gaining experience. If you’re in a position where the cost of a certification isn’t daunting, I would say definitely go for it. But if you’re like many who can’t afford to give out hundreds or thousands of dollars to gain a certification, then focus on what you can do on your own and gain experience that way through things, such as labs or projects. Interested in learning more? Below are some excellent references both free and paid.
- Twitter, Podcasts, Blogs, Books – as I find them, note this list isn’t exhaustive (https://docs.google.com/spreadsheets/d/1CyZVNR-jtloizDkEJqWKi0wblnEdJvQdwHcGqdgg06Y/edit?usp=sharing)
- PluralSight
- Networking Academy
- Coding Academy
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

