
A spam campaign leveraged malicious RTF documents to distribute notorious infostealers including Agent Tesla and Lokibot. While digging through a few other spam campaigns, Lastline observed unusual use of the C# compiler from the command line in some samples. Its researchers performed additional analysis and found that the samples belonged to the same malicious spam campaign. Lastline's telemetry data revealed that the campaign had begun in mid-October 2019, peaked on October 17 and then taken a three-week break before finally returning. In total, the security firm tracked 79 unique hashes out of the 138 samples, a fact which indicates that many of the samples played an active role only once. Some of those samples used generic email subjects, while some leveraged subjects that targeted specific events and organizations. They also struck a variety of customers, although education organizations in the APAC region were predominantly affected. Researchers at Lastline also decided to analyze one of the campaign's RTF samples. They found that the document leveraged a social engineering technique to trick the user into doing what they wanted. As quoted in their research:
Manually running the decoy RTF document in a VM launches Microsoft Excel, which then repeatedly pops up a window... asking for the activation of macros. This is probably an attempt to wear down a user’s patience to maximize the activation rate.
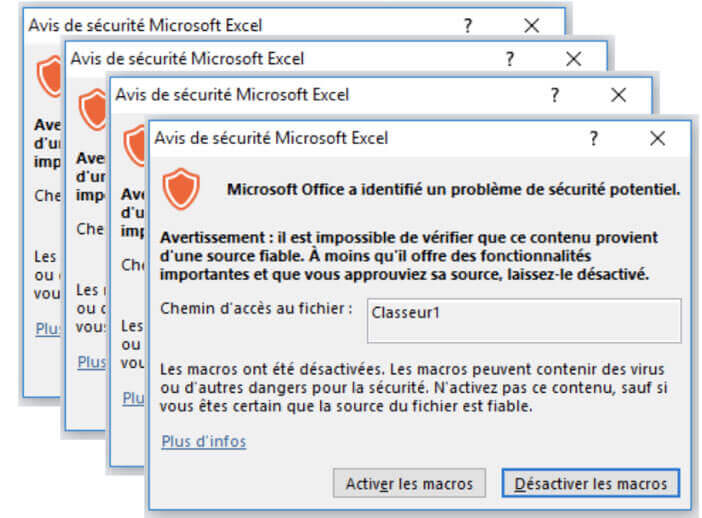
Activate macro pop-up windows. (Source: Lastline) In its research, Lastline found that the payloads employed by the campaign dated back to March 2018. This payload began as a resilient downloader that used PowerShell. But as time wore on, the payload incorporated new obfuscation and anti-detection tactics. They also eventually switched from PowerShell to C# in early 2019. In particular, the attacks began using the Add-Type cmdlet in their PowerShell payloads to compile C# programs. This tactic, in turn, enabled attackers to bypass AMSI-related detection for the purpose of downloading additional malware. The campaign described above highlights the need for organizations to defend themselves against spam campaigns. They can do so by educating their users about some of the most common phishing attacks in circulation today.

