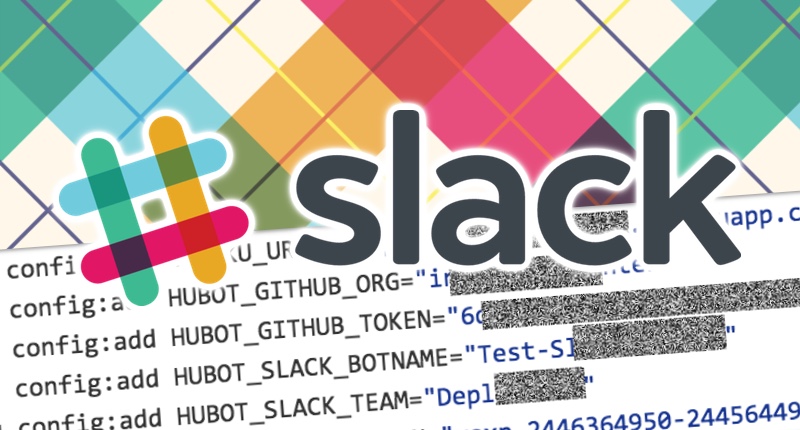
Business secrets could be at risk, after researchers discovered a worrying number of developers were posting access credentials for the Slack chat system on GitHub, embedded inside code repositories and public gists. Detectify Labs blew the whistle on the problem, reporting that it had uncovered thousands of Slack access tokens by simply searching GitHub - and new tokens are being made publicly available on the slight every day. The problem occurs because developers are not separating credentials from their code properly, meaning that anyone with malicious intent could easily search GitHub and potentially exploit a token with wide access to snoop on sensitive conversations happening inside a company.
"Using the tokens it’s possible to eavesdrop on a company. Outsiders can easily gain access to internal chat conversations, shared files, direct messages and even passwords to other services if these have been shared on Slack."
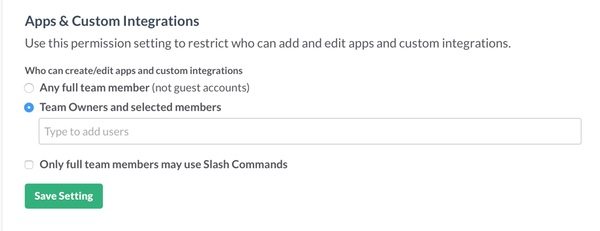
And, of course, if hackers can access your company's internal conversations that opens opportunities for them to intercept supposedly private messages including passwords and database credentials. Unfortunately, Slack credentials are trivial to find on GitHub because they are formed with the prefix xoxp or xoxb as Ars Technica reports. Detectify Labs says that it has identified tokens belonging to payment providers, ISPs, health care providers, universities, newspapers and Forbes 500 companies on GitHub. The advice for developers? Use environment variables inside a file, and do not put that file in your GitHub code repository. And check your public repositories to make sure that no-one has accidentally leaked credentials in the past. Furthermore, companies using Slack are advised to disable the ability for any users to create integrations and tokens.
In a statement given to Ars Technica, Slack reiterates the importance of keeping access tokens private, and says that it is revoking credentials which it sees being posted publicly by careless developers:
"Slack is clear and specific that tokens should be treated just like passwords. We warn developers when they generate a token never to share it with other users or applications. Our customers' security is of paramount importance to us, and we will continue to improve our documentation and communications to ensure that this message is urgently expressed." "We are monitoring for publicly posted tokens, and when we find any, we revoke the tokens and notify both the users who created them, as well as the owners of affected teams."
Sadly, human nature being what it is, I am sure we will continue to see sloppy practices by developers - carelessly leaking information in their code that could potentially be useful to hackers. Remember - the problem of leaking credentials in code isn't just one for developers working on Slack integrations. All programmers need to give proper consideration to what information they might be disclosing when they post their code online. Editor’s Note: The opinions expressed in this and other guest author articles are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.

