
There’s usually a surge in online activities during festive periods. People place gift orders and send funds to loved ones, and organizations roll out offers that reflect the spirit of the festivity.
Threat actors will usually take advantage of this activity to sneak past your defenses. By convincingly impersonating any of these legitimate offers, they can gain access to an organization's network, and wreak havoc.
Here are simple steps that employees and organizations alike can take to avoid phishing attacks during this festive period.
Always assume there's a threat
Phishing remains the most potent attack vector for threat actors. In 2021 alone, Cisco suggests that 86% of organizations worldwide suffered phishing attacks. In the same vein, Verizon reports that email phishing accounts for almost all phishing attacks.
One may ask why phishing is so prevalent. The answer is simple: internet users have a relaxed mental posture towards cyber security; so much so that only 3% of users could correctly identify all phishing email in a survey carried out by Intel in 2015.
for employees
It is helpful to always assume the presence of a threat. A Tessian study in 2021 revealed that 14 out of all the emails you receive in a year are phishing emails. This low frequency of phishing emails creates the odd paradox of significantly reducing the probability of detection. For this reason alone, it is important to treat each email like it is a phishing attempt. If you can definitively prove that it is legitimate, then it is safe to open it.
for organizations
A threat actor only needs to fool one employee to gain access to an organization's network. While there is a need to educate employees on cyber hygiene, the more paramount need is to continually remind them of the danger, especially in the specific areas where the threat is expected.
By putting employees on a perpetually high alert about issues regarding the possibility of a cyber attack and the ways by which it is likely to occur, the event of a cyber attack will be drastically reduced.
With the help of their email service providers, organizations should provide steady prompts for all email addresses in their domain. These prompts should remind employees of the possibility of a threat, whenever they click to open an email.
Always check that the sender's address matches their claimed identity.
A threat actor will design the malicious message to look and sound the same as what you're accustomed to getting from a trusted party. This is all done in an effort to make you lower your guard. However, that is on the surface. A closer look at the sender's email address will usually reveal the full domain, which will also indicate if the sender’s name or domain is legitimate.
Some threat actors go as far as purchasing domain names similar to that of your trusted party. They count on the fact that people let their guard down when they see something familiar.
for employees
Take your time accepting the familiar. A threat actor can use anything - a style of writing, or even a logo - to trick you. Some criminals even go as far as customizing an email address similar to the one you're familiar with. Always be sure to confirm the email address of a correspondent.
By hovering the cursor over the “from” component of an e-mail, employees can view the address from which the email was received. The fraudulent address can also be viewed by expanding the header area of the message.
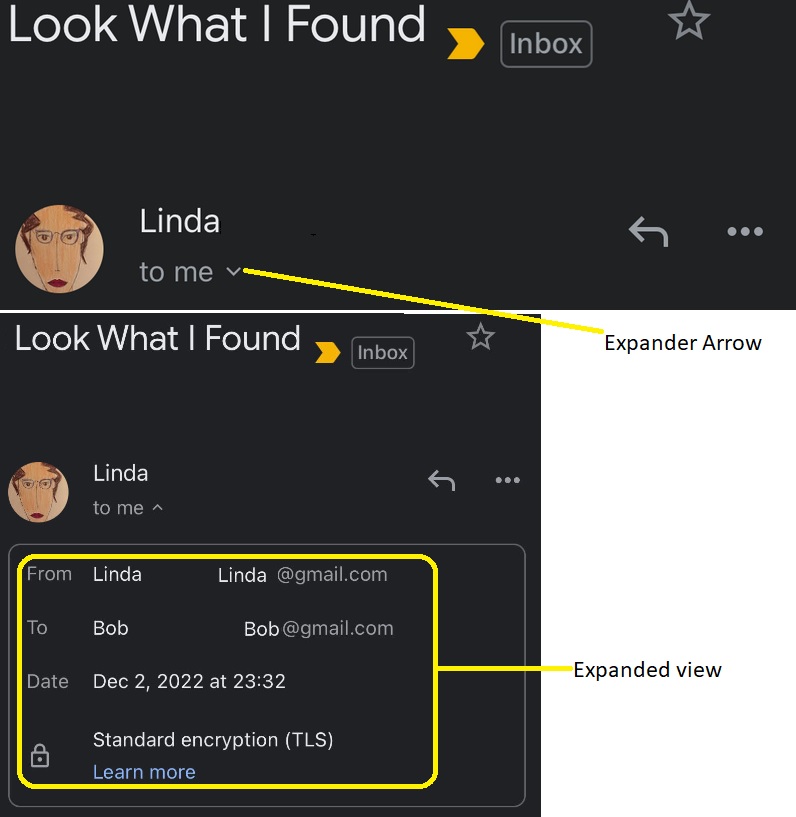
Take care to ensure that the email address corresponds to the actual email address of the trusted party, with no misspellings or extra words. It is better to pause and cross-check the email address properly with previous ones before engaging the email.
for organizations
Organizations should invest in email security. Mail administrators can set up technical methods to protect the company, such as Domain-based Message Authentication Reporting and Conformance (DMARC), Domain Keys Identified Mail (DKIM), or Sender Policy Framework (SPF). When used in a multi-factor approach to email authentication, organizations can drastically reduce the possibility of domain spoofing.
Scrutinize the body of the email
While threat actors have greatly reduced misspellings and grammatical errors in their writing by employing better writers, other kinds of errors will still give them away. Look for errors in context and brand voice.
Employees
A threat actor wants you to relax and maybe skim the content of the email once you get a sense of familiarity. Don’t relax, take your time and read your emails. An extra minute or two spent on reading your correspondences properly can save your organization millions in remediation costs.
Avoid skimming and be on the lookout for the kinds of careless errors that just don’t sound like the normal “voice” of the sender.
Be wary of generic salutations
A trusted party will definitely be privy to some of your personally identifying information, so they’ll most likely address you by name. A threat actor on the hand doesn't have your information, and therefore won't address you as pointedly they'll employ generic salutations, like 'dear customer', for the lack of customization and familiarity with you and your organization.
Always be on the lookout for such salutations. They may be the pointer you need to identify a phishing email. However, just because a person uses your name does not automatically qualify the message as a legitimate correspondence. Again, vigilance is the key to security.
Be wary of links and attachments
Threat actors usually add links to the body of an email. Clicking on these links will take the user to a malicious website where personal information and login credentials may be stolen. The worst are attachments. These may appear authentic, such as a google docs file, or a pdf file. Threat actors embed malware into such files, which are injected into the user's device when the user downloads them.
for employees
Never click a link, or download an attachment until you're absolutely sure that the email is legitimate. In the event that you clicked a link mistakenly, do not answer any requests for personal information or login credentials; and report to your IT department as soon as possible.
for organizations
Attachments, particularly zip files are almost impossible to scan for malware.
However, by investing in a suitable email security solution, organizations can limit the number of phishing emails, altogether reducing the possibility of receiving a malicious attachment.
Staying Safe From Phishing During This Festive Period
This will depend entirely on how alert you are to the dangers out there. Assuming the presence of a threat at all times will not only keep you on the lookout for threats but will also make you better at identifying them.
Have a wonderful and safe holiday ahead.
About the author:

Ezifeh Chinua is a B2B Tech writer in the Cybersecurity and SaaS niches. He has written for publications like Hackernoon and Future Syllabus amongst others. He's currently acquiring his CISSP certification.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

