
If you've got an email account or social media profile, it's likely you've come across phishing of some kind before. In a sentence, phishing is the fraudulent attempt to steal personal information by social engineering: the act of criminal deception. Verizon's latest Data Breach Investigations Report notes that "social engineering remains worryingly effective" in targeting users, with over 30 percent of phishing messages sent during 2016 opened — up from 23 percent in 2014. Considering the takeaways from Verizon's report, Tripwire editor David Bisson saliently remarks that "no locale, industry, or organisation is safe" from phishing; further analysis found that credential exfiltration and theft of trade secrets remain threat actors' primary motives. Phishing has clearly gained traction as an opportunistic vector; the frequency of this threat can be mapped to a concerning upward pattern. Corroborating this view are findings from the non-profit Anti-Phishing Working Group, who identified the retail sector as most frequently targeted, with over 40 percent of recorded attacks.
AOL, warez and the origins of phishing
Social engineering techniques have long been part of the criminal playbook; the earliest phishing cases transpired more than twenty years ago. At the dawn of the '90s, attackers targeted the once popular America Online (AOL) platform, using instant messages to trick users into divulging their passwords. It didn't take long for these threat actors to pinpoint higher value targets, pressuring unsuspecting victims to "verify their billing information" against the urgency-ridden threat of account deletion. By way of this evolution, not only could criminal groups obtain victims' AOL credentials, but also their bank account and payment card details. AOL stepped up their anti-fraud operations, implementing new measures to proactively expunge accounts involved in phishing. This was a decisive move which prompted attackers to jump ship in search of new opportunities.
Criminal campaigns
Phishing entered the mainstream with hastily fabricated emails full of typos, low-resolution images and design issues. Users were urged to pick up on these so-called "telltale signs" which became quite easy to spot. At the same time, users became accustomed to the fallacious idea that "typos equals phishing", and that any site with faultless spelling, grammar and presentation must be legitimate. Another example is the idea that "HTTPS equals 100% safe" — researchers frequently identify threat campaigns using Let's Encrypt certificates (which use Domain Validation SSL) to instill a dangerous false sense of security. If you're interested in finding out more about the bleeding edge of phishing research, check out the Malware Hunter Team on Twitter. Consisting of @JAMESWT_MHT, @techhelplistcom and @demonslay335, the team identify and dismantle campaigns targeting users of services like iCloud, PayPal and Facebook. Wombat Security Technologies hint these points in their inaugural State of the Phish report. Published in January 2016, the Wombat survey found that phishing campaigns with the highest click-through rates involved topics that people would expect to encounter during day-to-day work duties, including shipping confirmations and HR paperwork. Interestingly, employees were more cautious when opening emails with a pretext based on Get Rich Quick schemes, awards and competitions. When considering the broad takeaways that we can draw from these reports, one clear finding is that phishing remains a principal catalyst for a wide-ranging set of attacks.
Spear phishing
Some of the most infamous cybercrimes over the last ten years — taking out retail chains, universities and even banks — started with a single user opening a spear phishing email. Where conventional phishing uses wide-scope attacks predicated on chance and opportunity, spear phishing is highly targeted. Technology research firm Vanson Bourne clocked the average financial impact of a successful spear phishing attack at $1.6 million. Using gathered knowledge and open-source intelligence (OSINT) feeds, threat actors craft personalised pretexts for small, select groups of employees. Because spear phishing emails are so distinctive, traditional reputation and spam filters often fail to detect the malicious content within. A spear phishing attack can also incorporate sender forgery, polymorphic URLs and drive-by downloads to circumvent common protections.
Whaling and CEO fraud
Whaling is a term used to describe a phishing attack specifically aimed at a single, high-profile business target; CEOs, directors and executive-level staff represent the company's big phish.
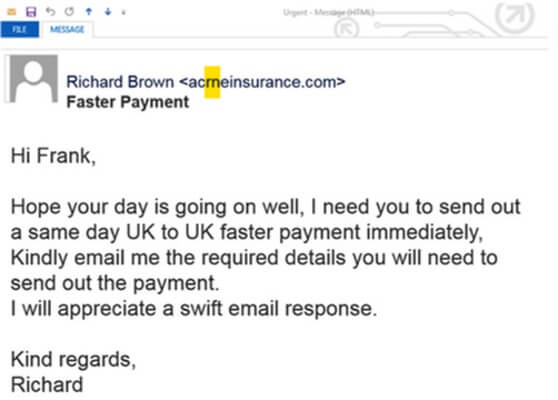
In a whaling attack, a threat actor sends an email with a meticulously crafted pretext — often built around the idea of an "urgent wire transfer" or financial transaction. For this reason, whaling is often equated with the idea of CEO fraud and Business Email Compromise (BEC) scams.
Emerging techniques
Social media spoofing Towards the end of 2016, Proofpoint reported on cybercriminals spoofing the Twitter profiles of UK banks' customer service departments. These sophisticated threat actors imitate the naming convention, visual assets and mannerisms of the bank's employees.
Cybercriminals create convincing fake customer service accounts with a handle similar to your real customer support account. Then they wait for customers to reach out to your real account with a help request. When your customer tries to contact your brand, the criminal hijacks the conversation by responding with a bogus customer support link sent from the fake support page.
Dubbed "angler" phishing (not to be confused with the Angler Exploit Kit), this attack vector is highly effective because "customers are already expecting a response" from the brand. In a recent Social Media Brand Fraud Report, Proofpoint discovered that nearly 20 percent of social media accounts associated with ten global brands are fake. Ransomware and soft targeting The PhishMe Q1 2016 Malware Review found that 92 percent of recorded all phishing emails contained a strain of cryptoransomware. By the Q3 2016 report, this figure had grown to over 97 percent. Researchers note that Locky continues to prevail as the most flexible variant, with criminal groups constantly refining the construction and means of delivery. The use of soft targeting and widely distributed attacks is also key; phishing with "soft targeted" deployment can be placed somewhere on a scale between the whaling attack and wide-scale phishing email. Rohyt Belani, CEO of PhishMe, left readers with a troubling conclusion:
The rapid awareness and attention on ransomware has forced threat actors to pivot and iterate their tactics on both payload and delivery tactics. This sustained tenacity shows that awareness of phishing and threats is not enough.
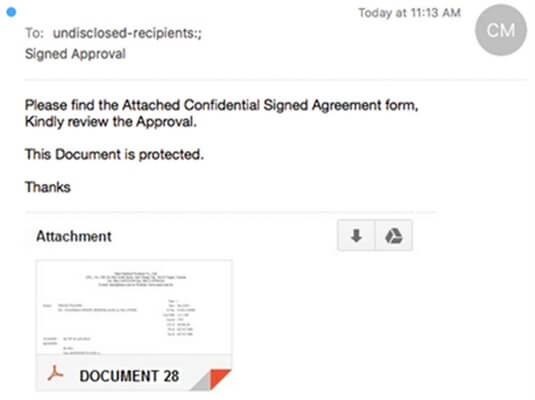
Dropbox and Google Drive Phishing campaigns based around cloud storage services like Google Drive and Dropbox have been making the rounds for quite a few years. These are usually quite conventional in form, directing victims to a fabricated login page with a link and hint of intrigue. I recently came across a case where the criminal inserted an image masquerading as a PDF attachment within Gmail, which was actually a link directing the user to a Google Account phishing site.
Six tips for staying safe
- Avoid replying to suspicious emails or engaging with senders
- Open the site yourself — don't click on embedded links or media
- Look out for pretexts laced with a sense of urgency or threat
- Verify requests and information with out-of-band communication
- Check your browser to ensure Anti-Phishing services are enabled
- Use a password manager; don't use the same password across multiple sites

About the Author: Yasin Soliman lives and breathes information security. In addition to working as an independent research analyst, Yasin writes for the award-winning site Graham Cluley Security News. You can find him on Twitter at @SecurityYasin. Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc. Save
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

