
These days, it’s not a matter of if your password will be breached but when. Major websites experience massive data breaches at an alarming rate. Have I Been Pwned currently has records from 705 sites comprising 12.6 billion accounts. This includes well-known names like Wattpad, Verifications.io, and Facebook. This is a 30% increase in the number of sites and a 10% increase in the number of accounts from when I published these numbers in 2021 and 139% and 138% respectively since the first version of this article in 2018.
Password breaches are a cause for embarrassment. They are talked about in hushed tones just like finding mice in your home or having your credit card declined. They don’t need to be though because they are part of the online experience associated with a modern cyber life.
Instead of being embarrassed, take steps to minimize the impact that a data breach has on your life. One of the best ways to do this is to enable multi-factor (or two-factor) authentication on the accounts that you use on a regular basis. Adding a second form of authentication (typically in the fashion of a code generated by or sent to a device you own), can ensure that no one accesses your accounts, even if they have your passwords.
When talking about MFA, we’ll discuss apps like Google Authenticate (and similar apps) that implement One-Time Password (OTP) support as well as delivery mechanisms such as Push or SMS. In previous versions of this article, I’ve mentioned that text messages (SMS) are an acceptable fallback method if you are unable to utilize any of the better approaches. Friends and colleagues have pointed to various articles, like this piece from Vice, as examples of why SMS should not be utilized for MFA.
I completely agree that SMS is not a great secondary service if you are a high-profile individual or you are protecting a critical service. However, those of us in the industry sometimes forget that best effort is better than no effort. While there are risks to SMS-based MFA, it is important to remember that the attacker already has your username and password at the point where MFA matters. Without SMS, they already have access to your account if no other MFA methods are available. With SMS, however, they need to decide if they want to invest time and money in order to gain access to your account. That additional layer of security is better than nothing.
One recent change that I’m not a fan of with MFA is password managers with OTP support. It took me a while to come around to password managers in general, and I’m still not fully sold on them. There are certain accounts that I will never store in a password manager. The idea, however, of attending OTP support to password managers is very self-defeating in my eyes. Multi-Factor Authentication implies that there are multiple authentication methods in use. If your password manager houses both your passwords and your one-time passwords, then a breach of your password manager eliminates the value in multi-factor authentication. Yes, in terms of a breach on the service side, you are still protected by OTP, but I’d prefer to keep my passwords and my one-time passwords stored separately. Of course, this may simply be because, as I said, I still don’t have full confidence in password managers.
Here you will find step-by-step instructions on how to configure multi-factor authentication on some of the world’s most popular websites.
Links to Instructions
Google (Gmail, YouTube, etc)
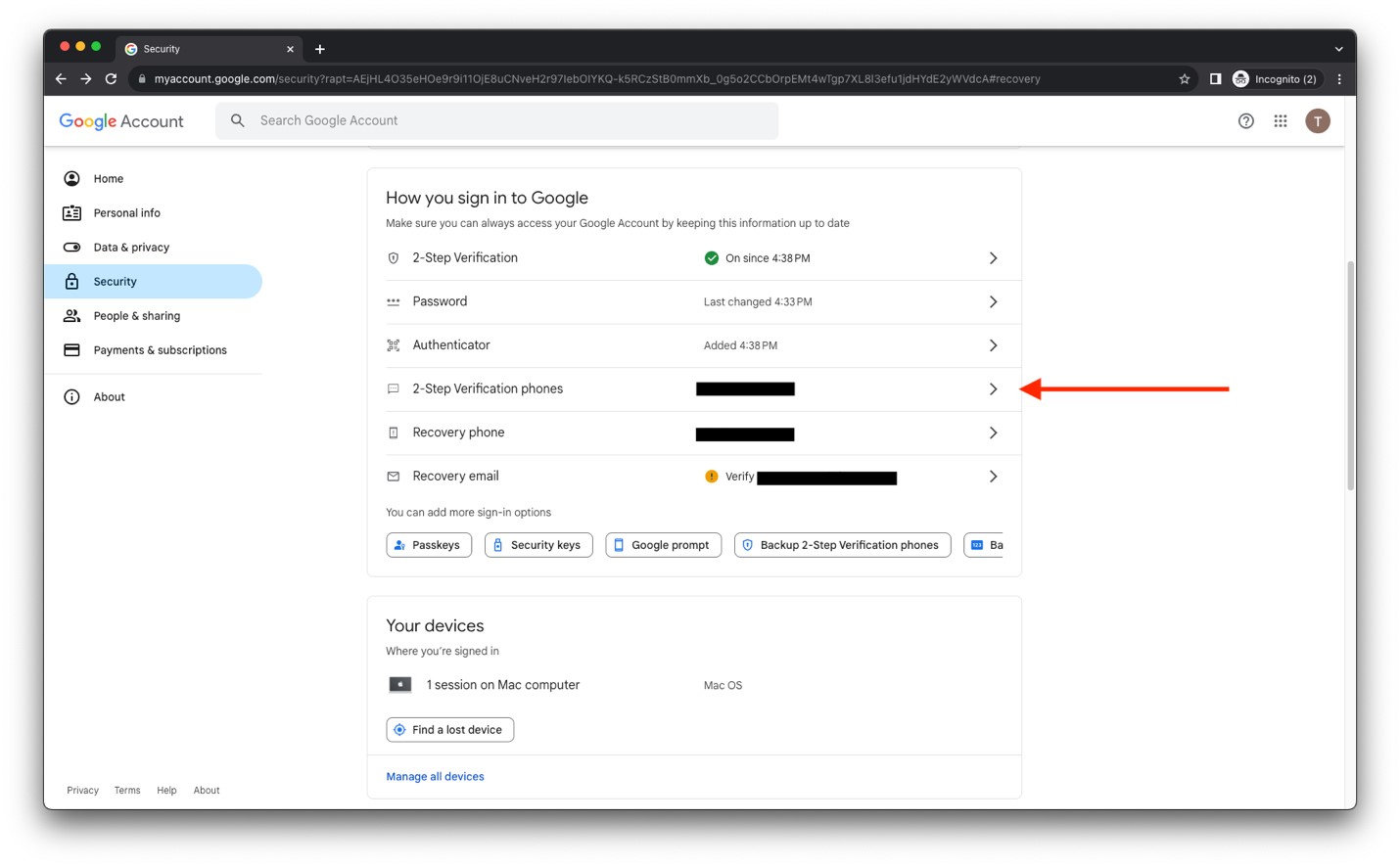
- Browse to https://myaccount.google.com and log into your Google account. Click on Security.
Image
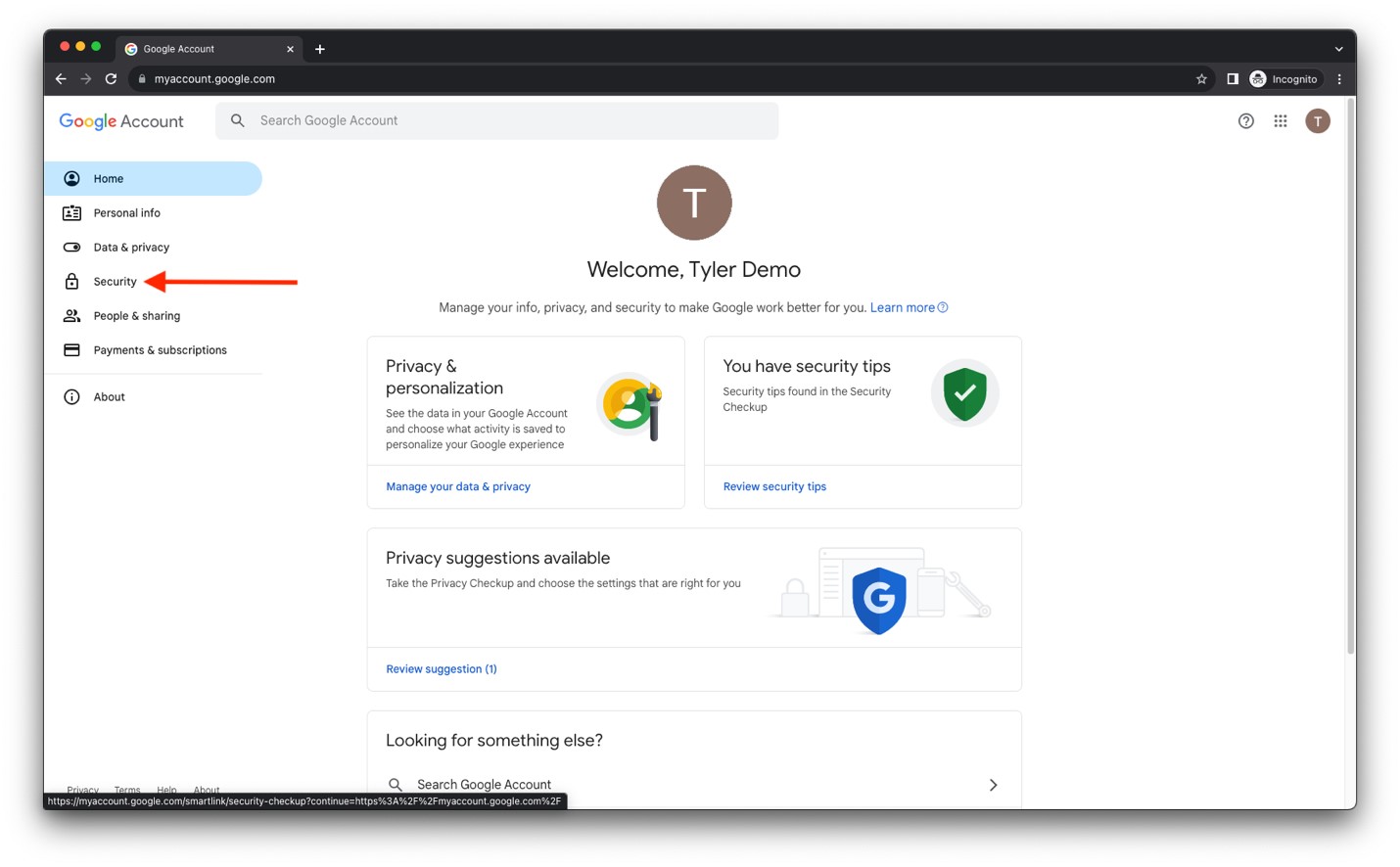
- Near the bottom of the Security screen, you’ll find 2-Step Verification. Click to turn it on.
Image
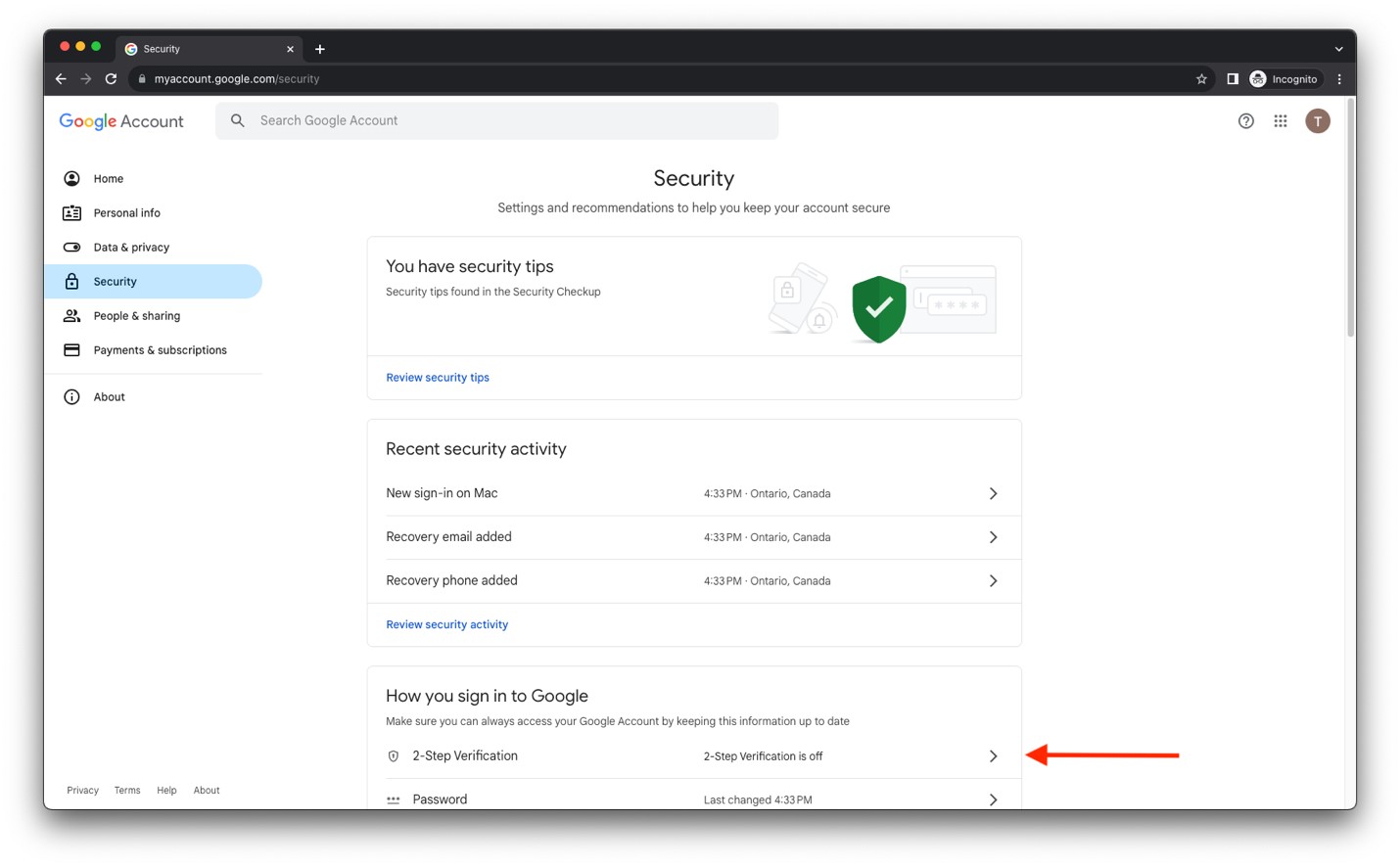
- At this point, you’ll enter the process to enable 2-Step Verification and can click Get Started.
Image
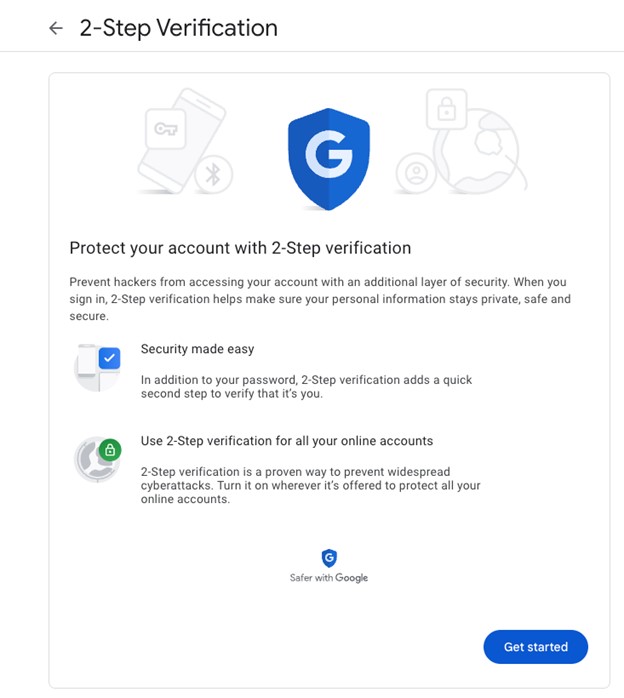
- Google does not allow you to setup Authenticator immediately, so we’ll first enable text-based MFA. Enter your phone number and click Next.
Image
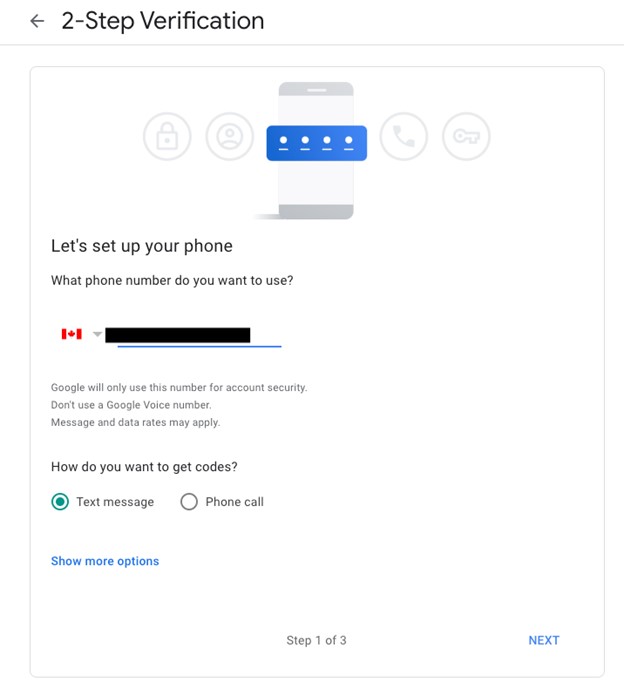
- Enter the Google Verification Code that you are sent (G-######) and click Next.
Image
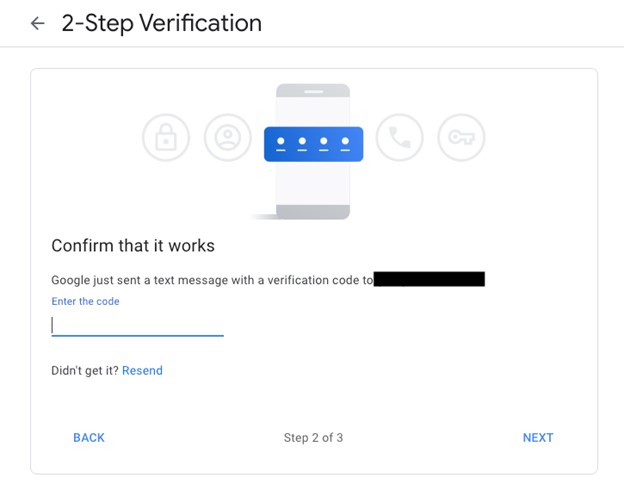
- Click Turn On to successfully enable SMS-based MFA.
Image
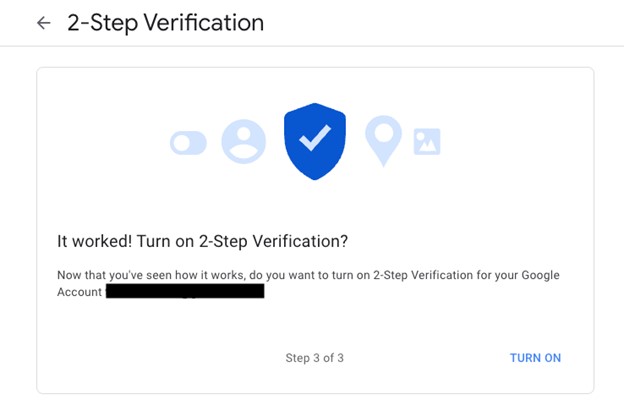
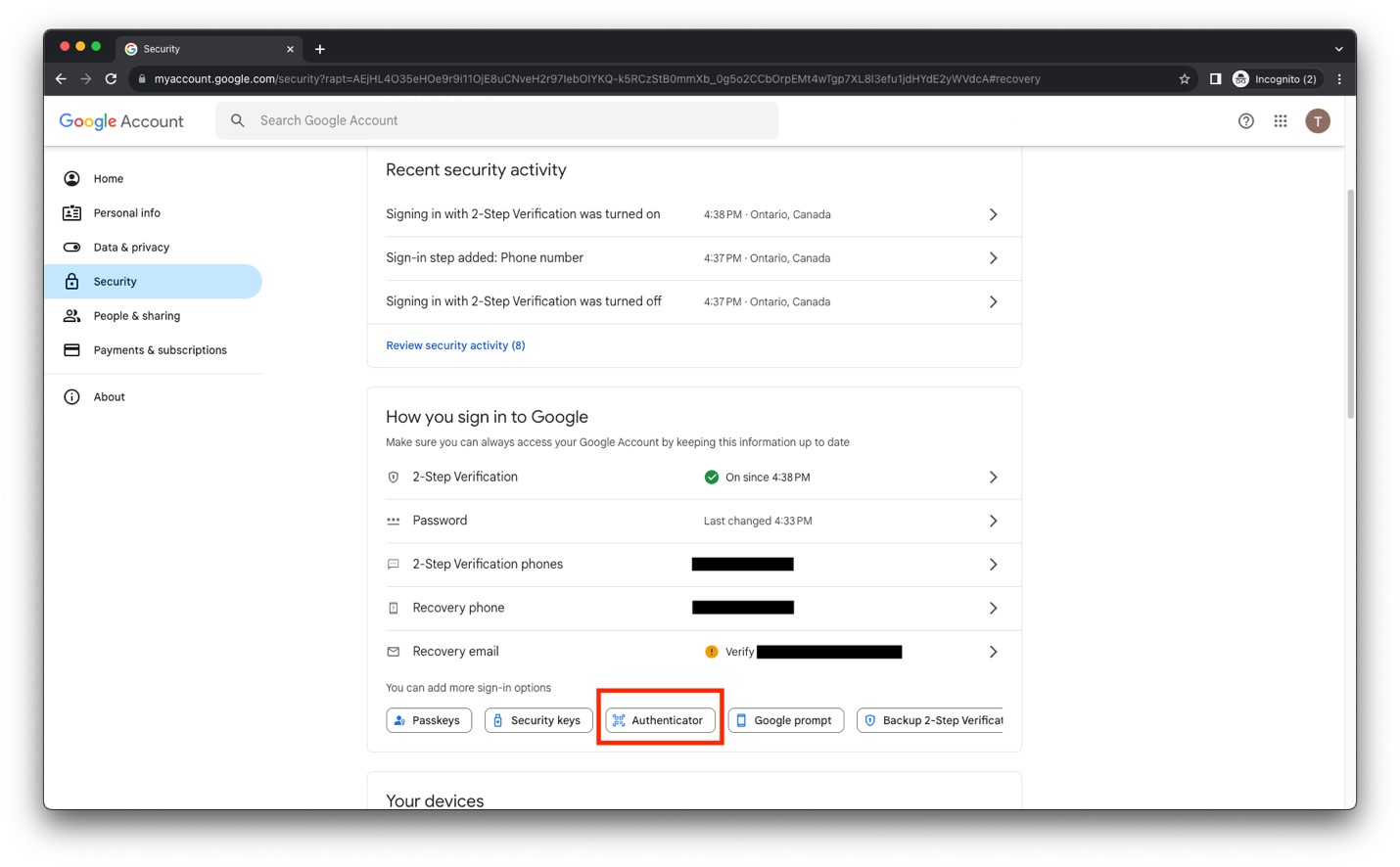
- We now want to add Authenticator as a valid MFA method. Click on Authenticator in order to continue with that process.
Image
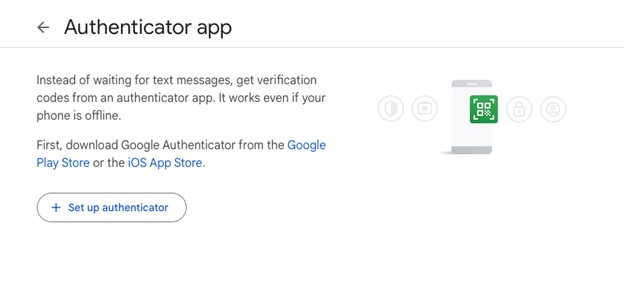
- Within the Authenticator app screen click Set up authenticator.
Image
- Follow the on-screen devices, which means opening Authenticator and scanning the displayed QR Code. Once the code is scanned, click Next.
Image
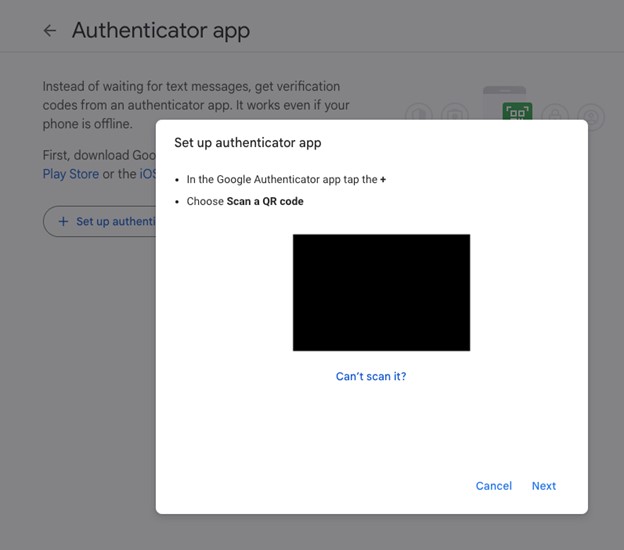
- To confirm that you scanned the QR Code properly, enter the 6-digit code displayed within the app and click Verify.
Image
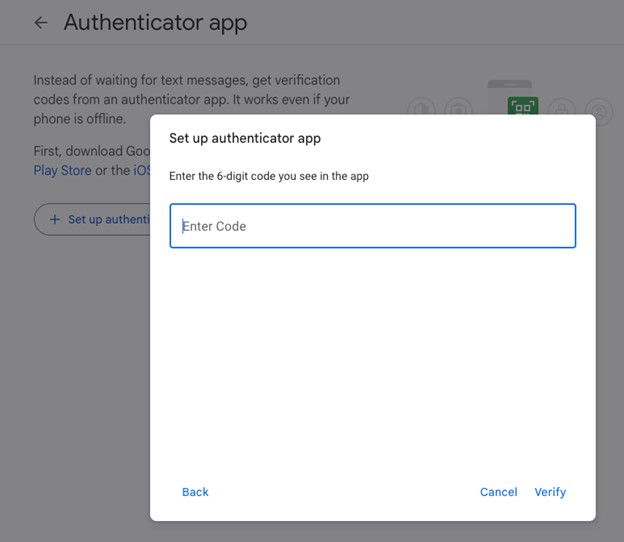
- You can now confirm that the Authenticator app is setup and click the arrow to back out to the previous screen.
Image
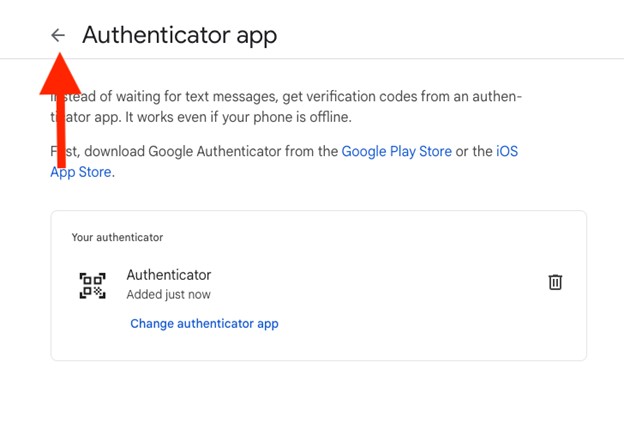
- You’ll notice that you still have 2-Step Verification phones listed. You now get to decide if you want to keep the SMS backup or remove it. If you want to remove it, click into 2-Step Verification phones.
Image
- Click the Trash Can icon followed by Remove in order to remove the SMS MFA method.
Image
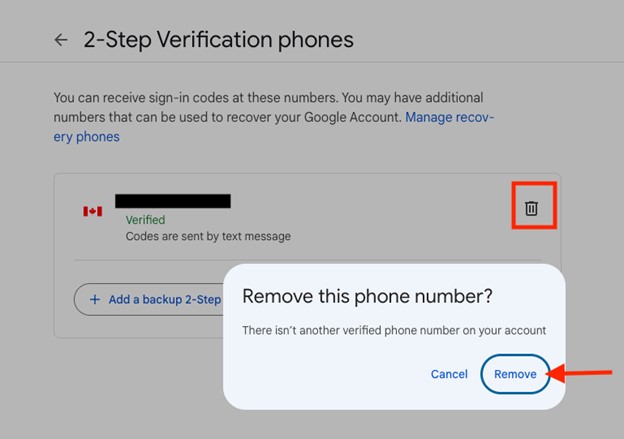
- You can now confirm that the 2-Step Verification phone number has been removed and click the arrow to back out to the previous screen.
Image
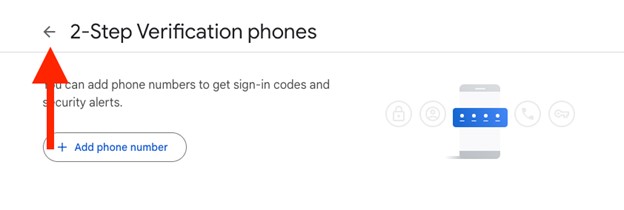
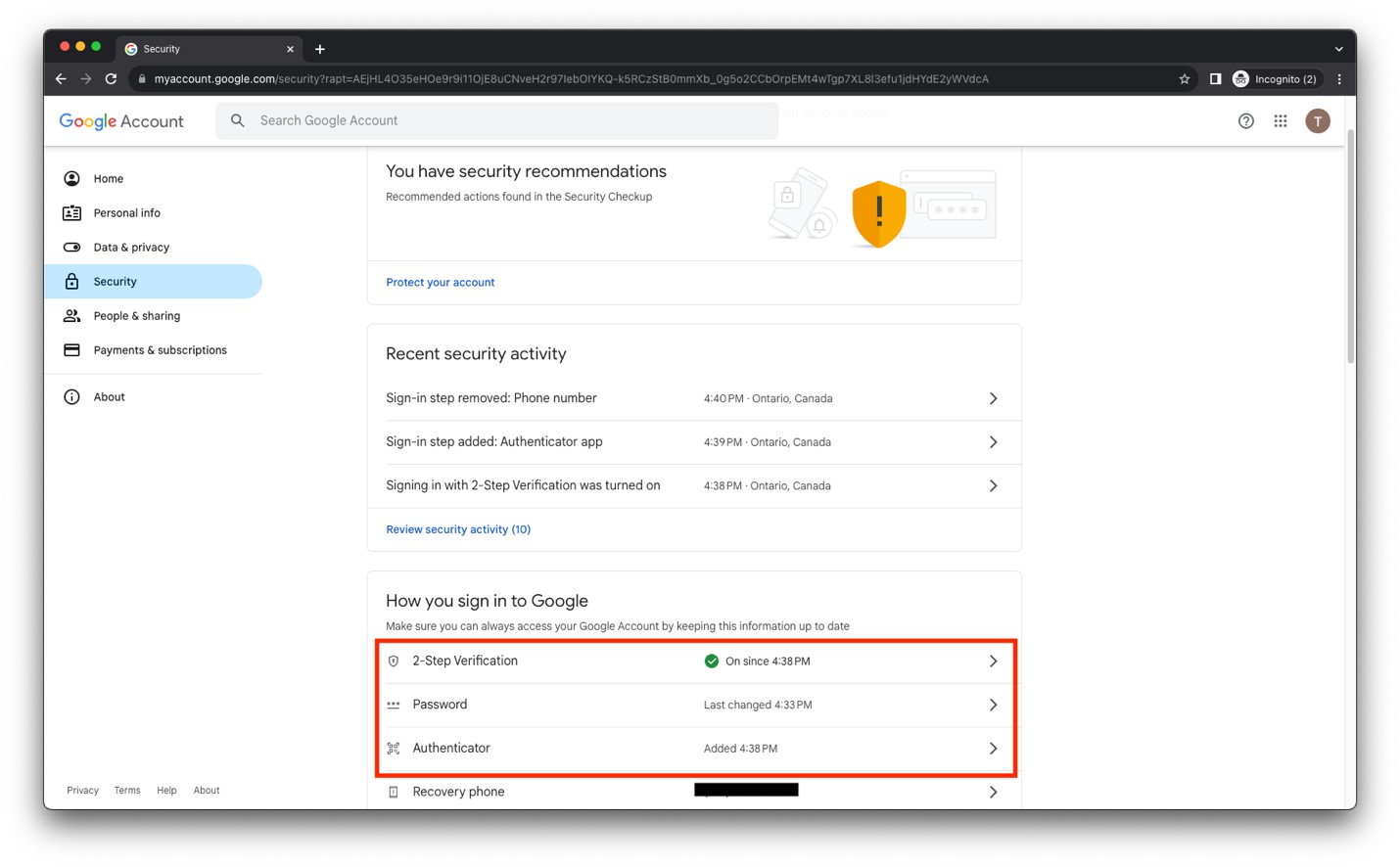
- At this point, you have 2-Step Verification enabled with Authenticator as your second authentication method.
Image
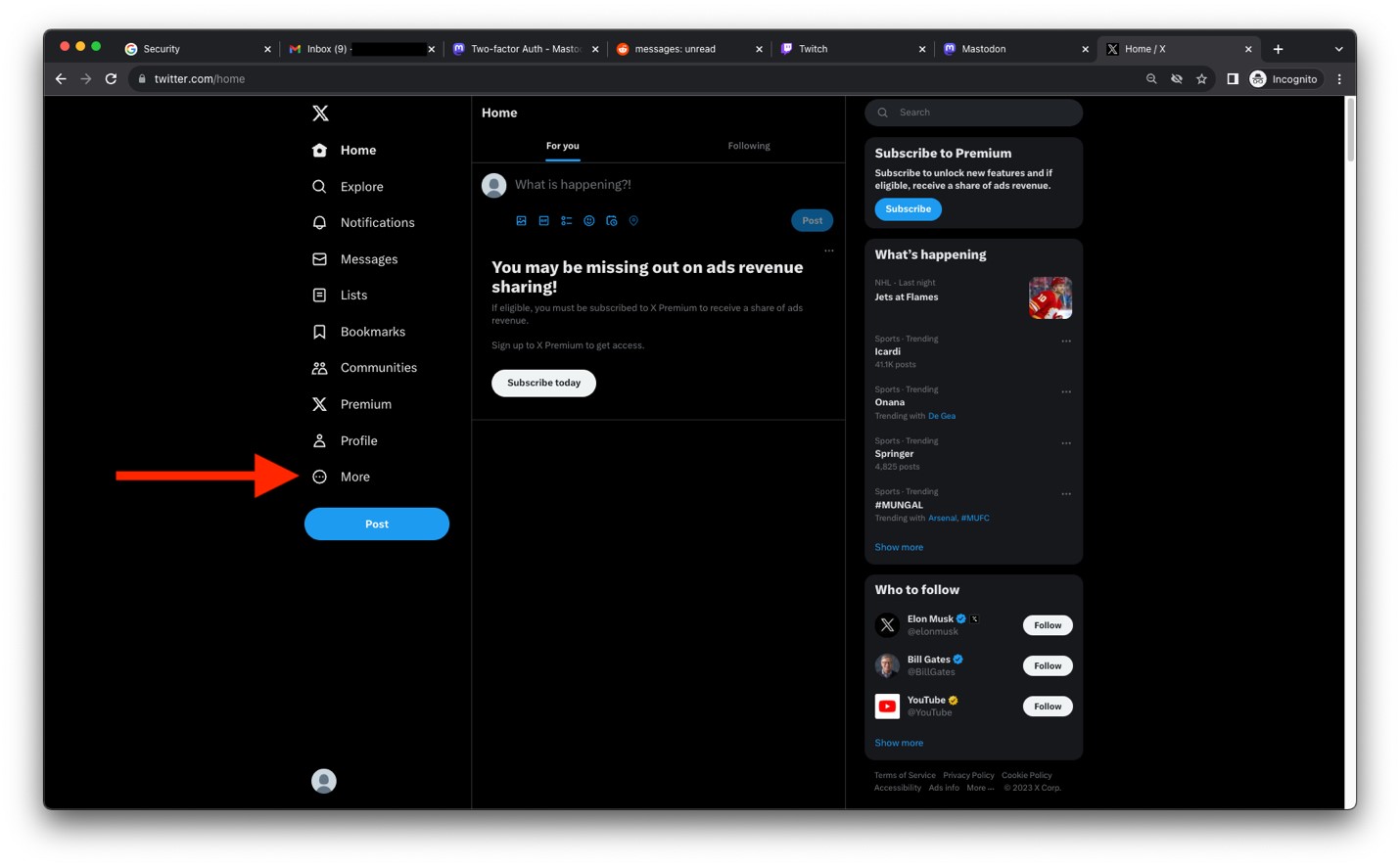
X (Formerly Twitter)
- After you have logged into your account, click on More.
Image
- Click on Settings and Support.
Image
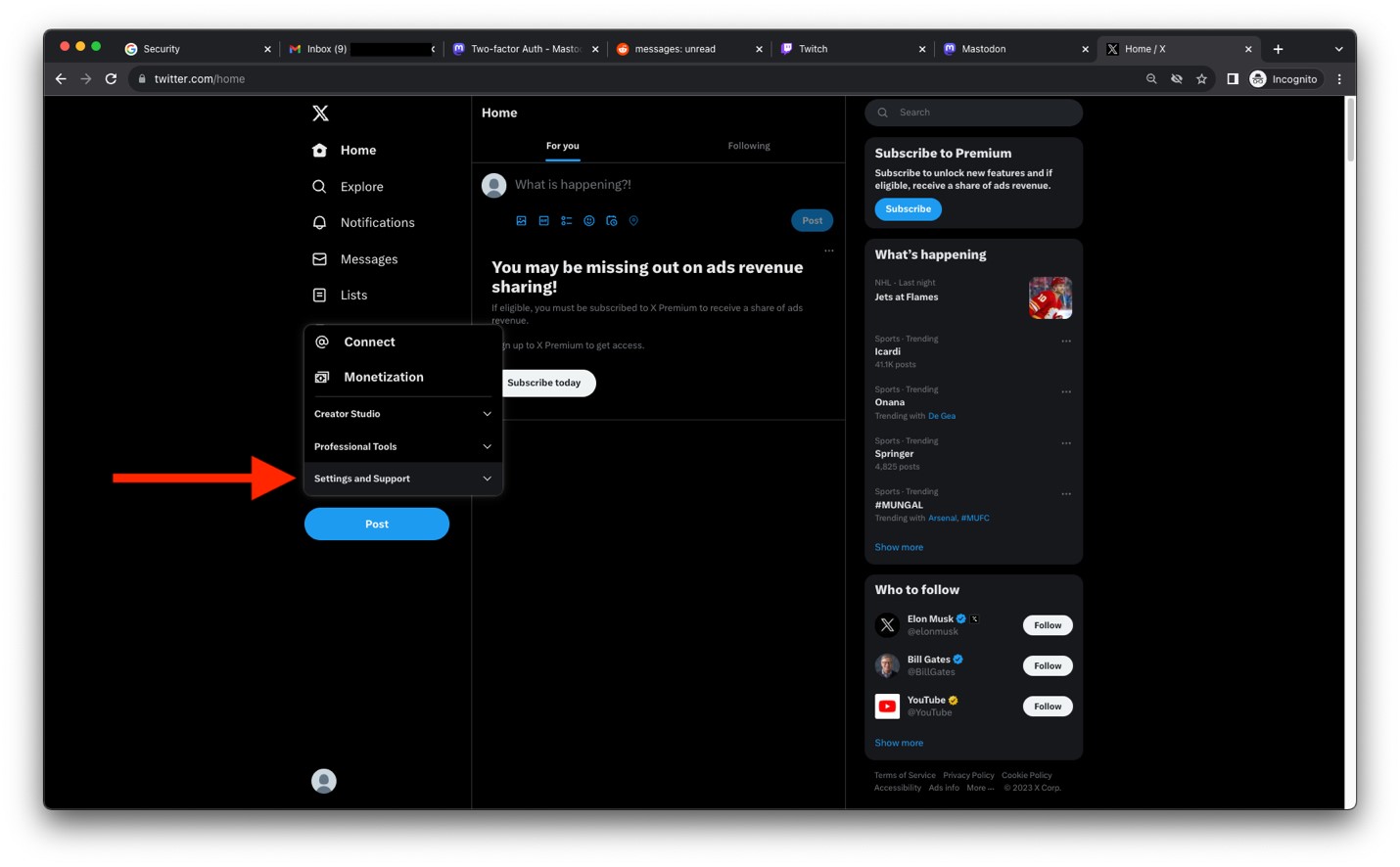
- Click on Settings and privacy.
Image
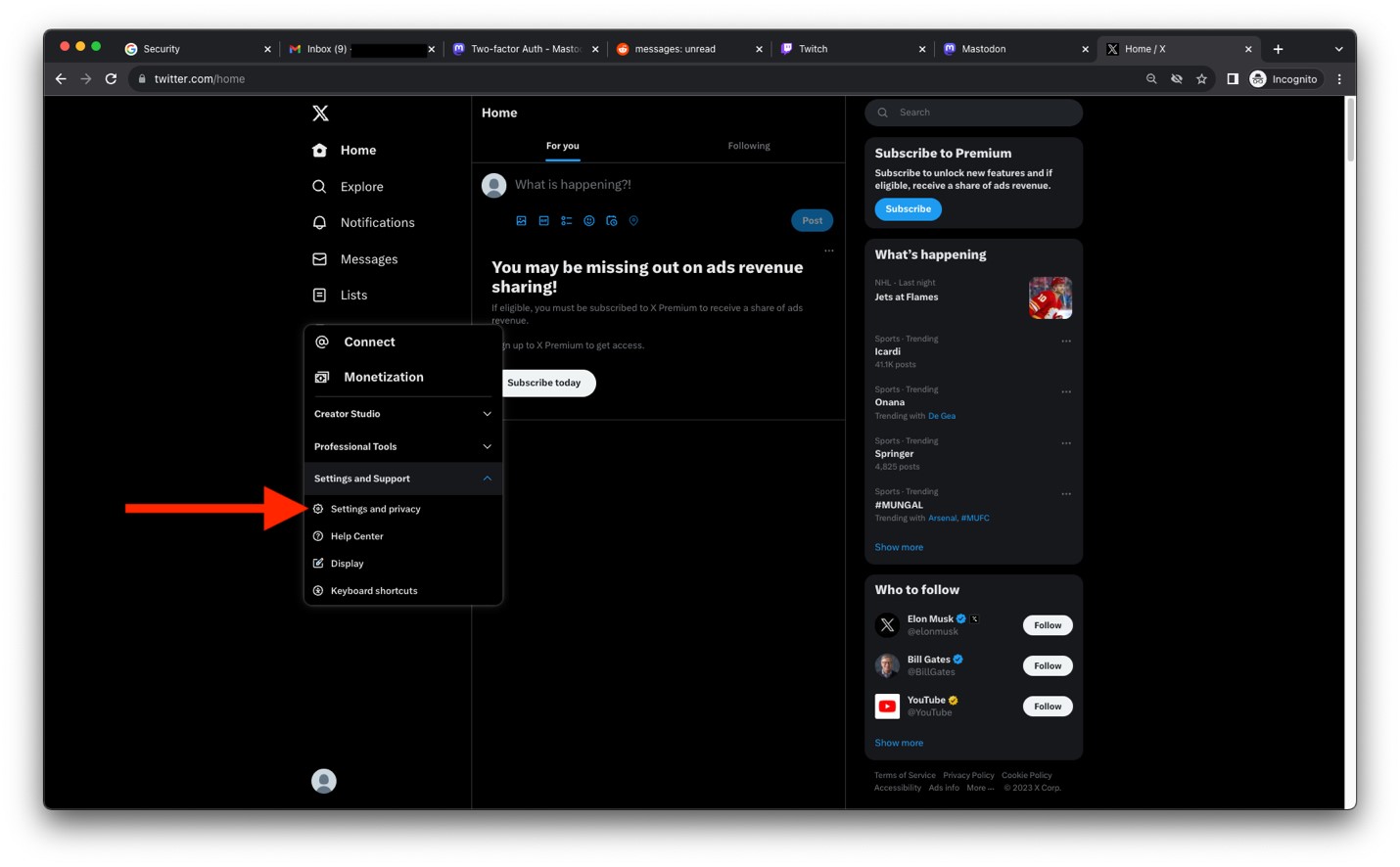
- Click on Security and account access.
Image
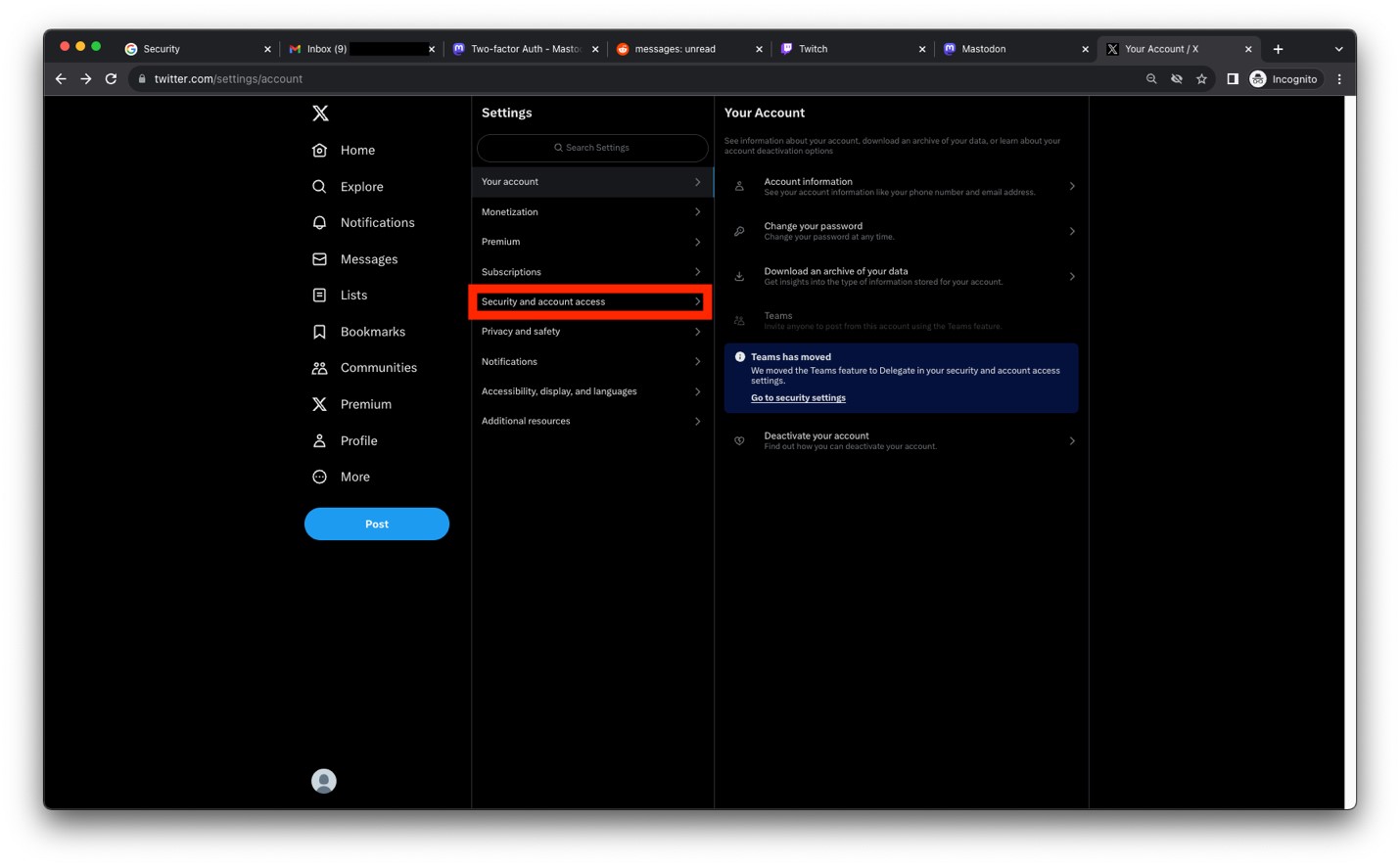
- Click on Security.
Image
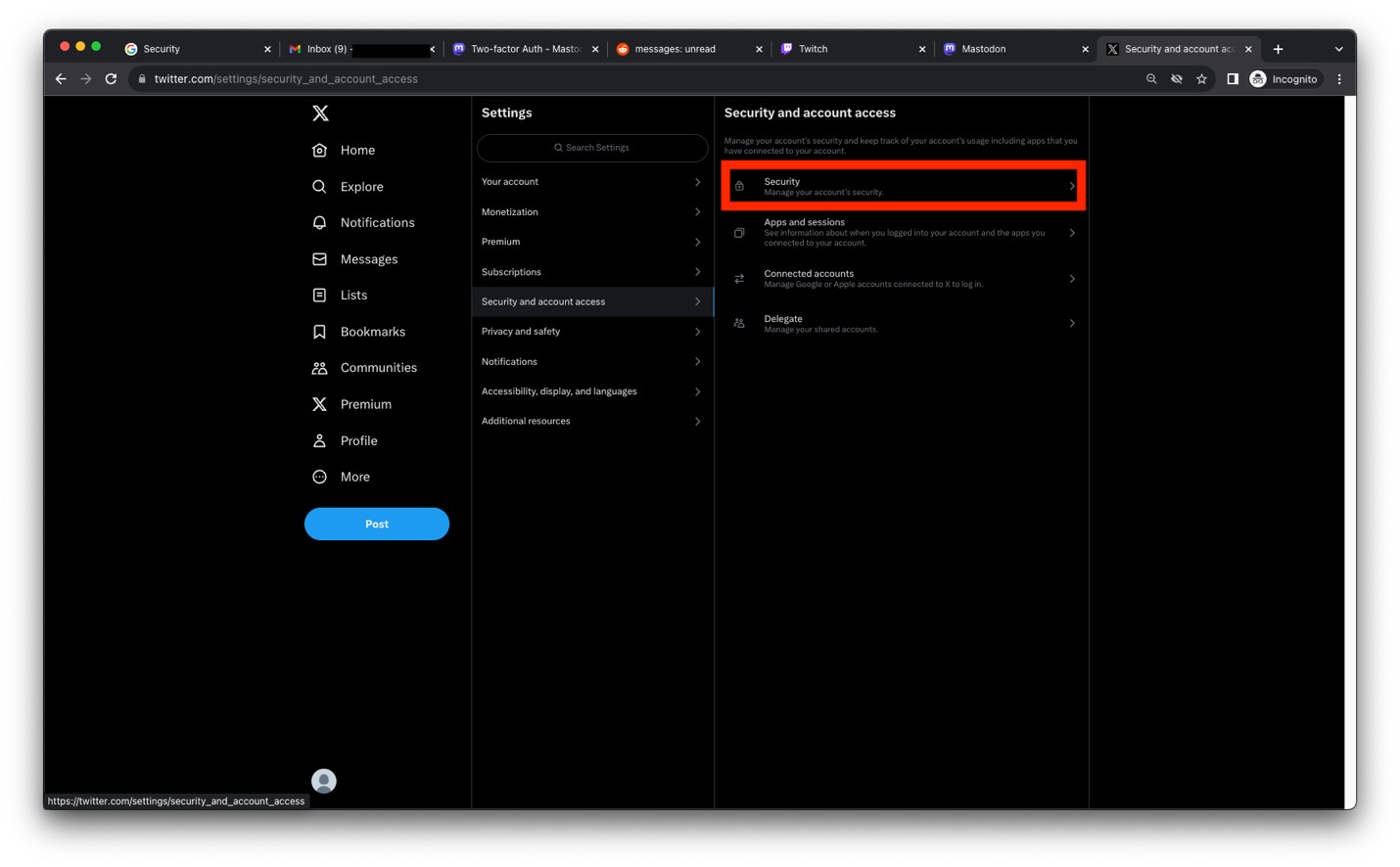
- Click on Two-factor authentication.
Image
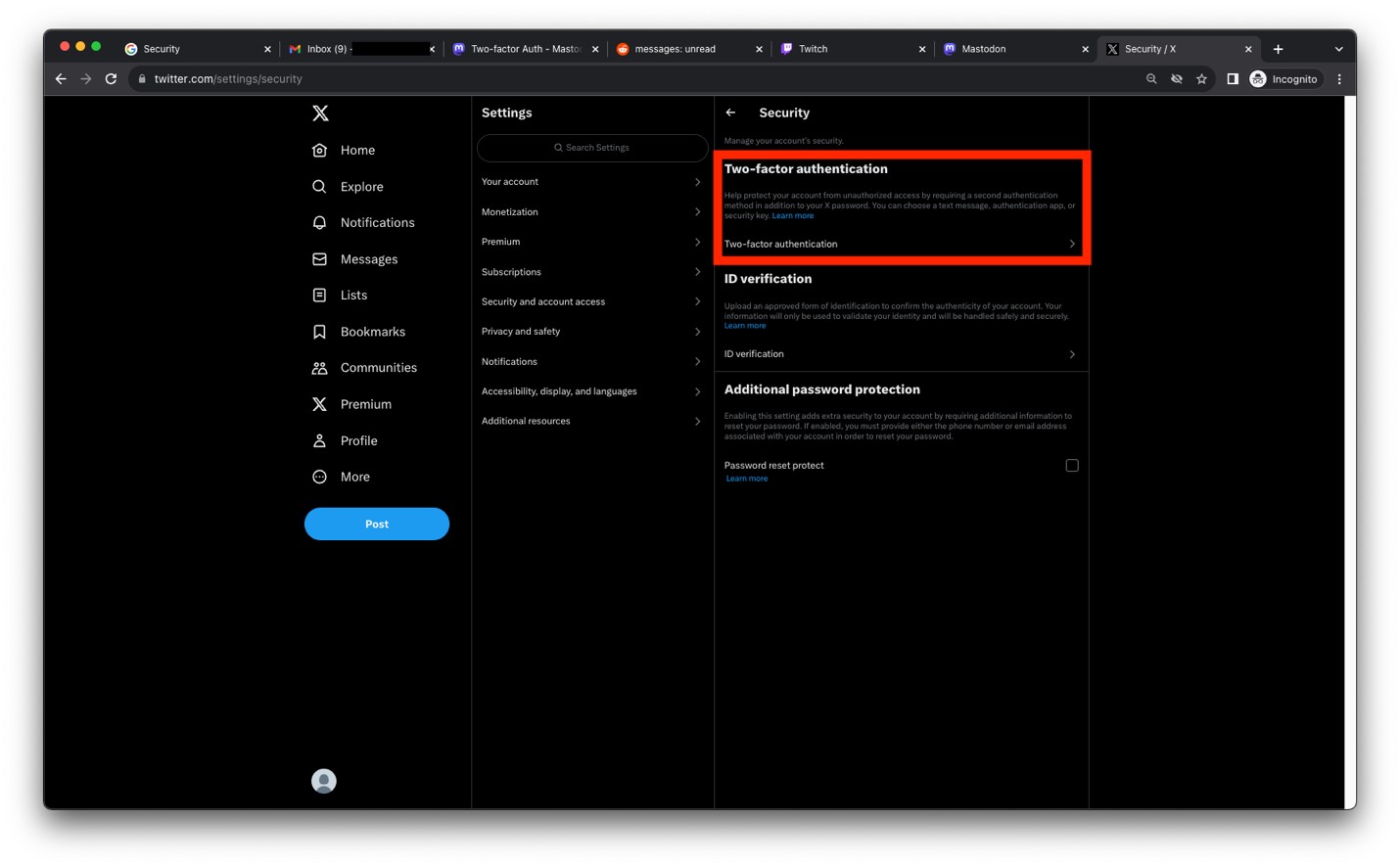
- Select Authentication app.
Image
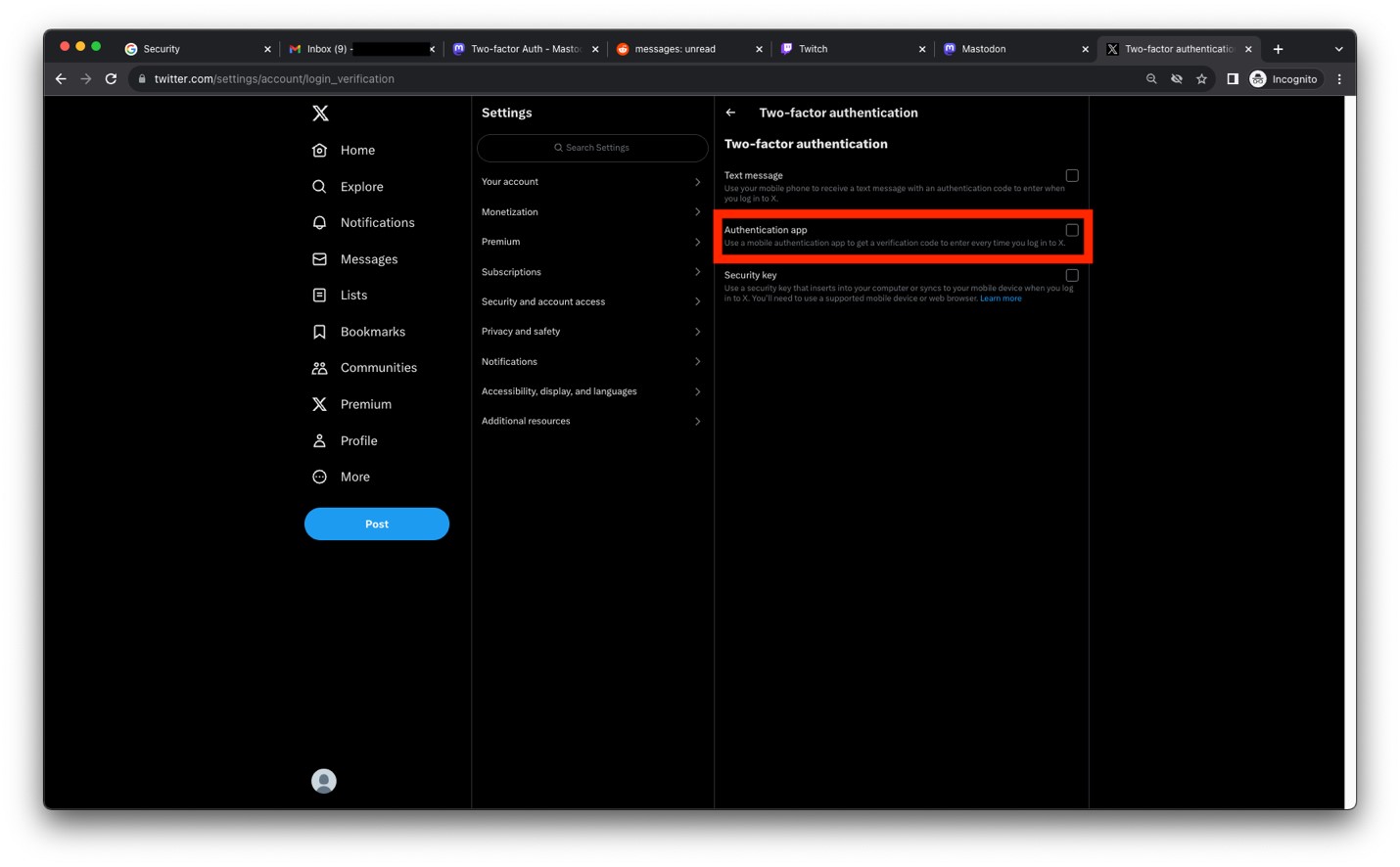
- Click Get started.
Image
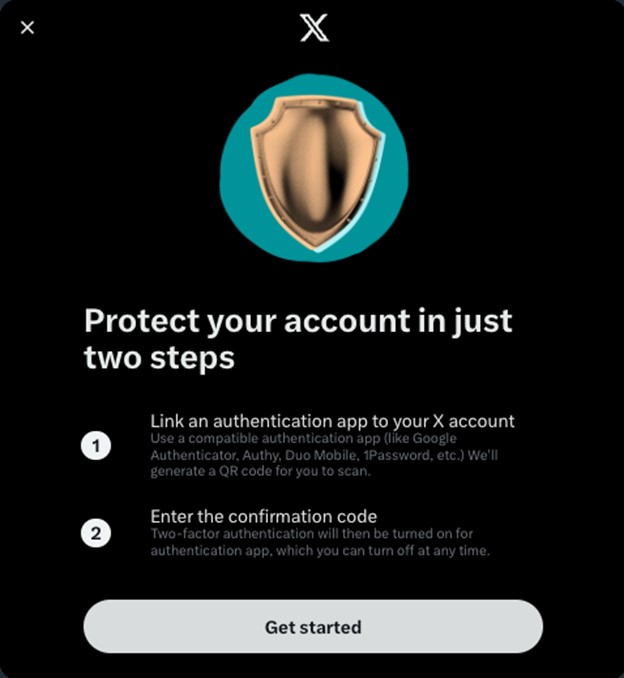
- Scan the QR code with your Authenticator app and click Next.
Image
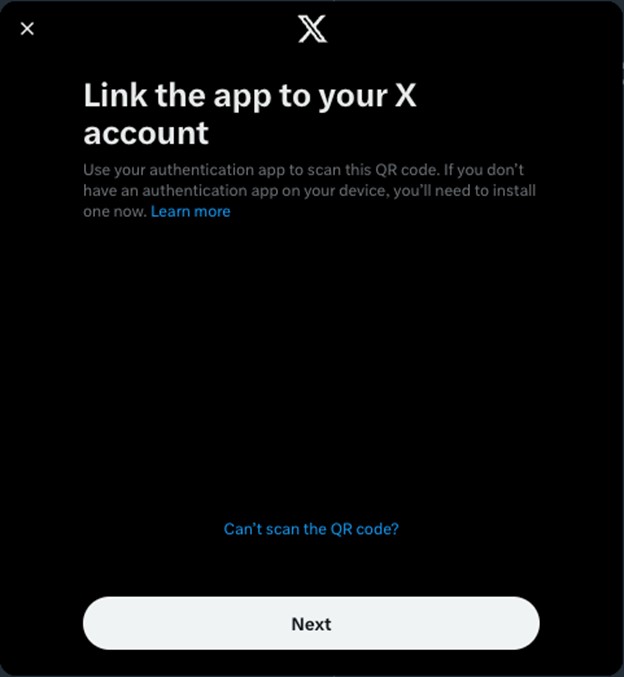
- Enter the code from your Authenticator app and click Confirm.
Image
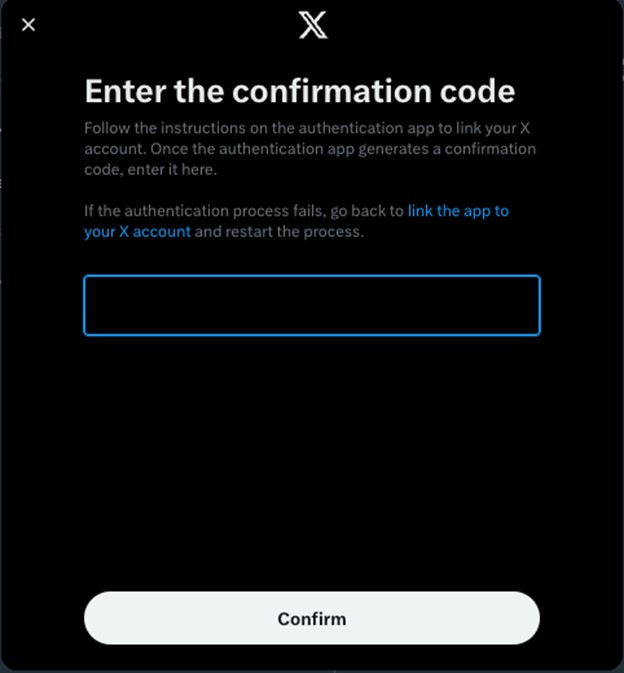
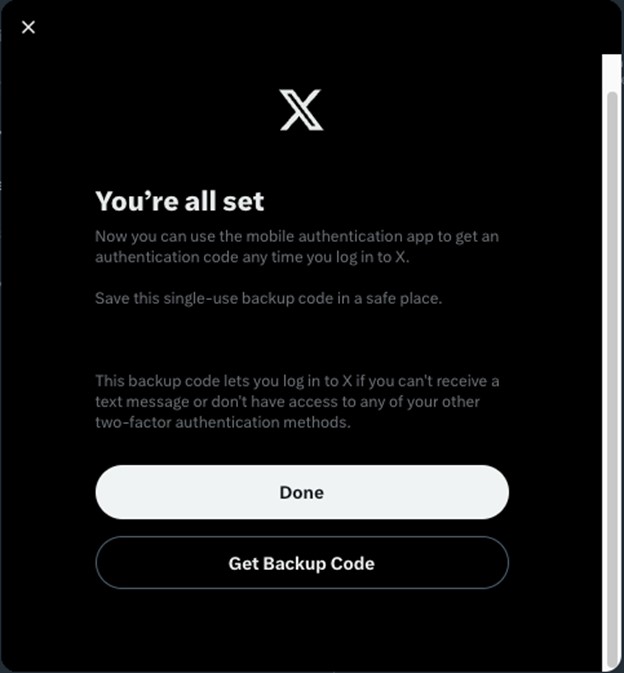
- You’ve enabled multi-factor authentication. You can save your single-use backup code and click Done.
Image
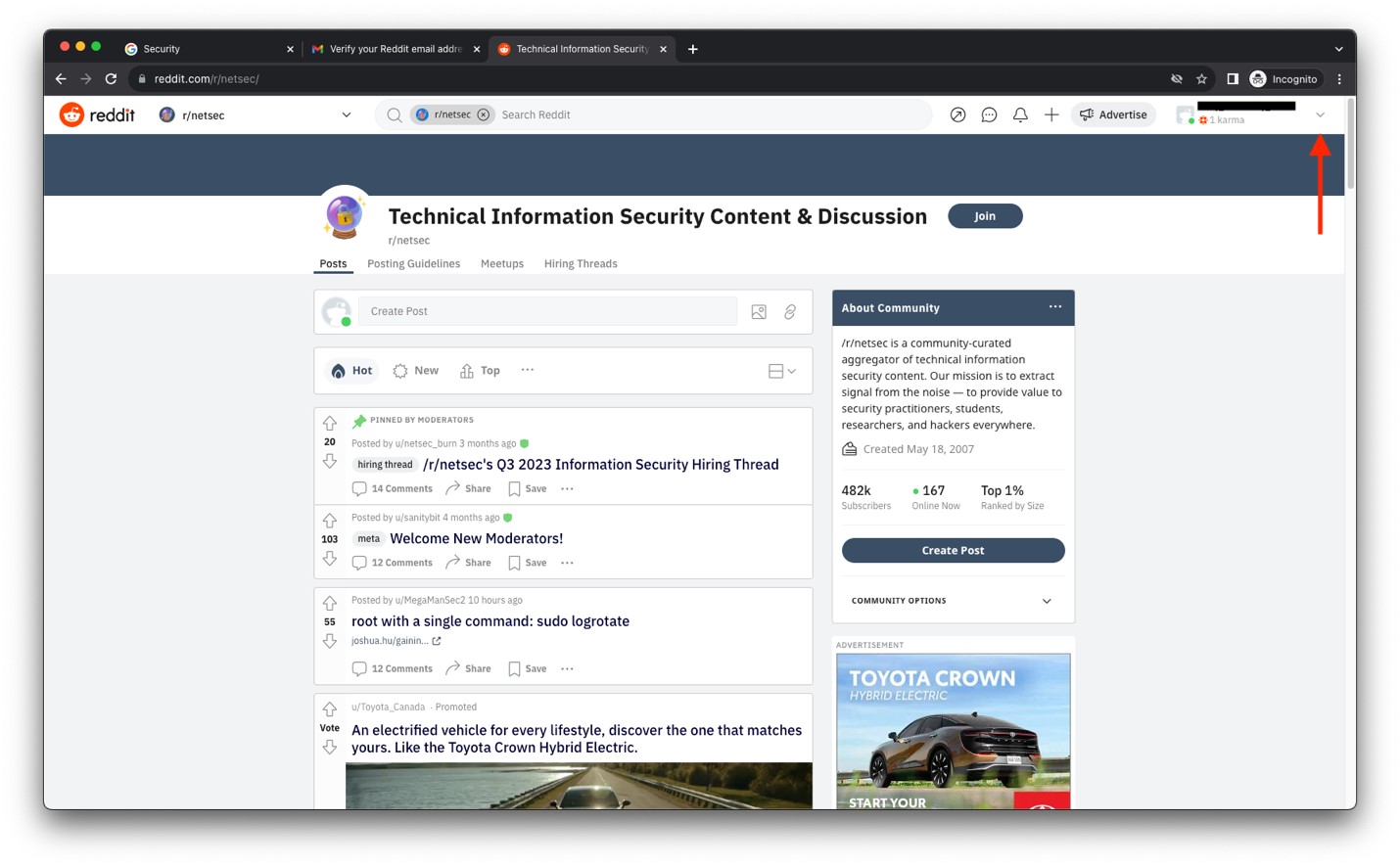
- After you’ve logged into your account, click the down arrow next to your username.
Image
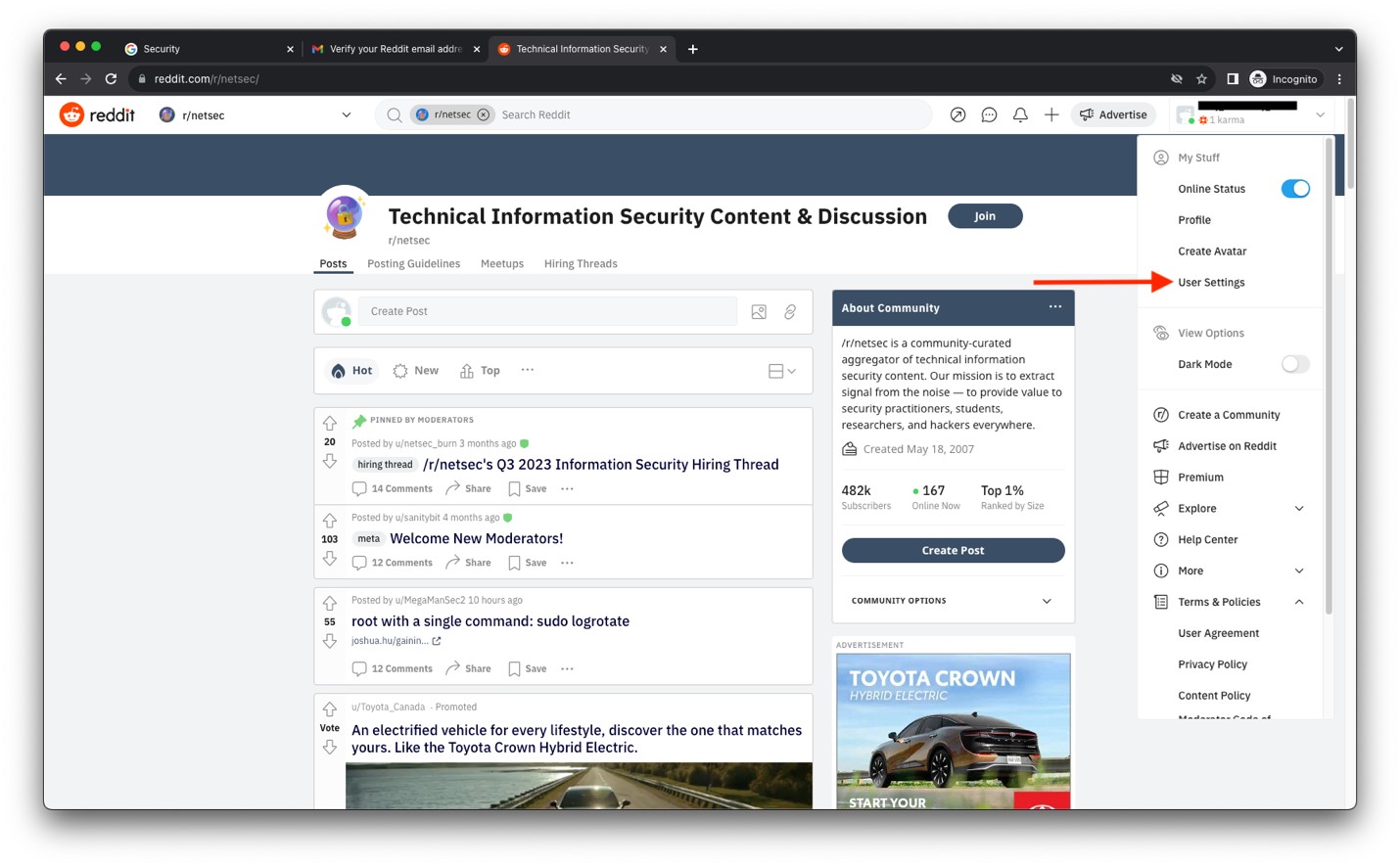
- Click User Settings.
Image
- Click Safety & Privacy.
Image
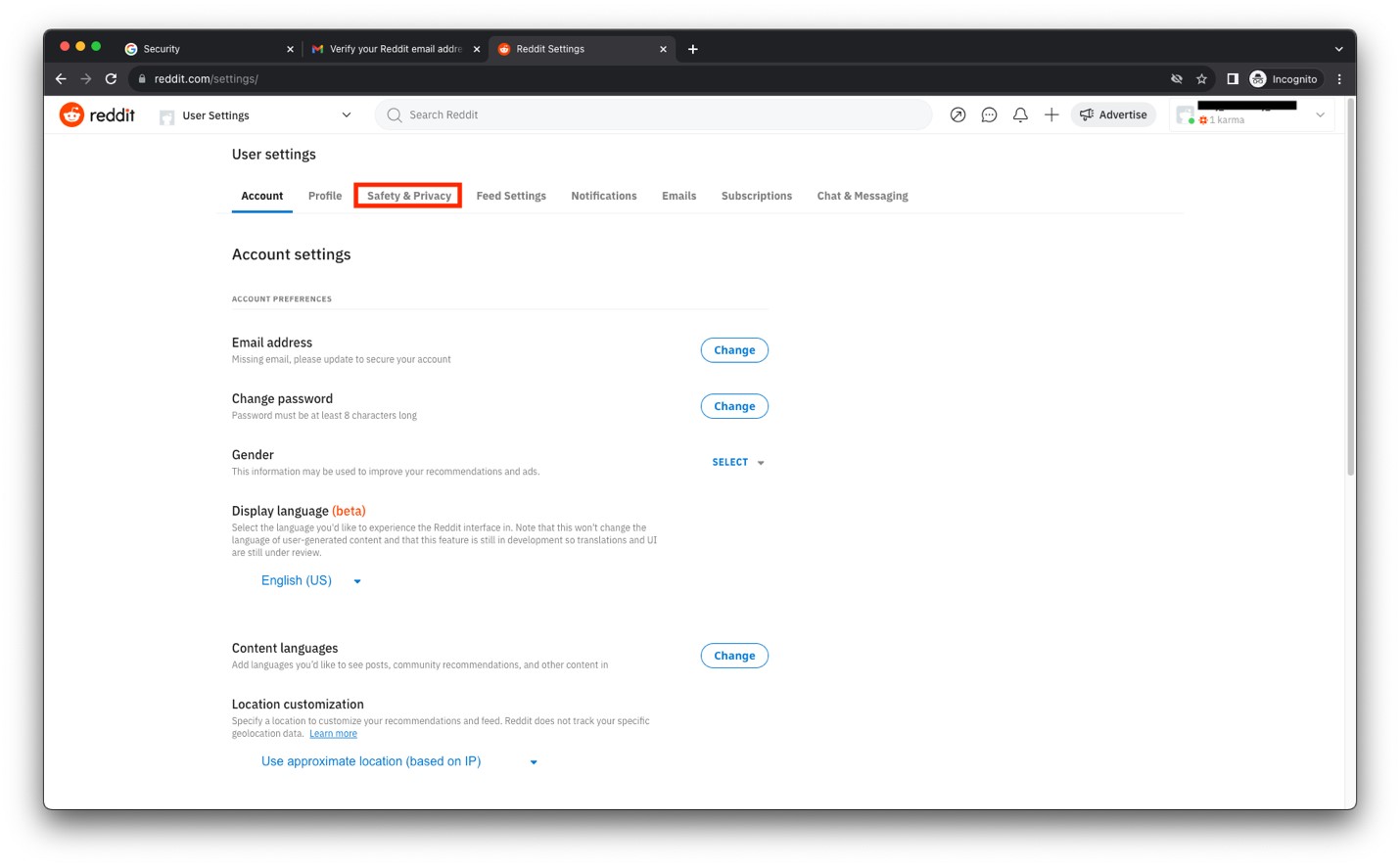
- Scroll down under the Safety & Privacy settings.
Image
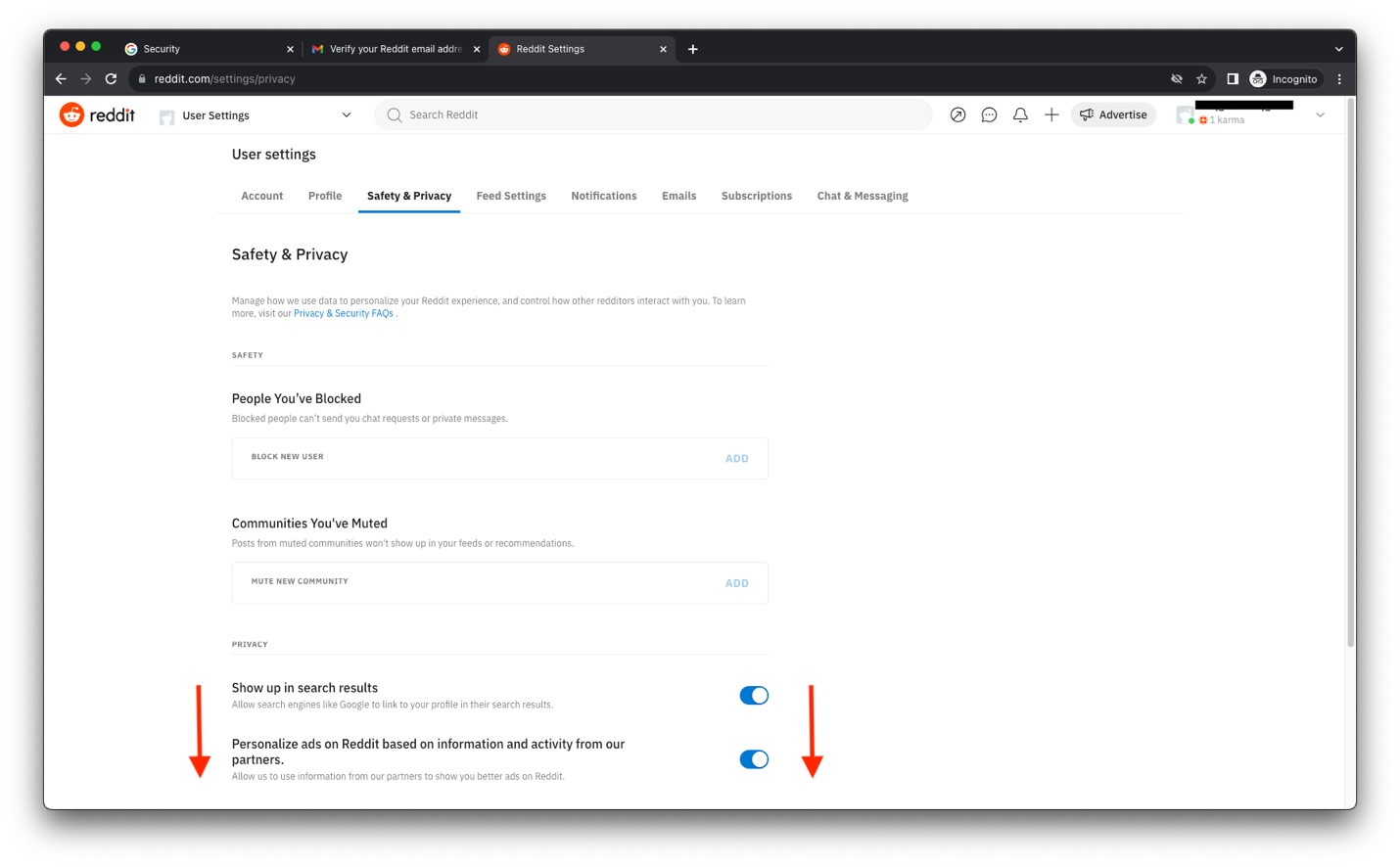
- Click the switch to enable Use two-factor authentication.
Image
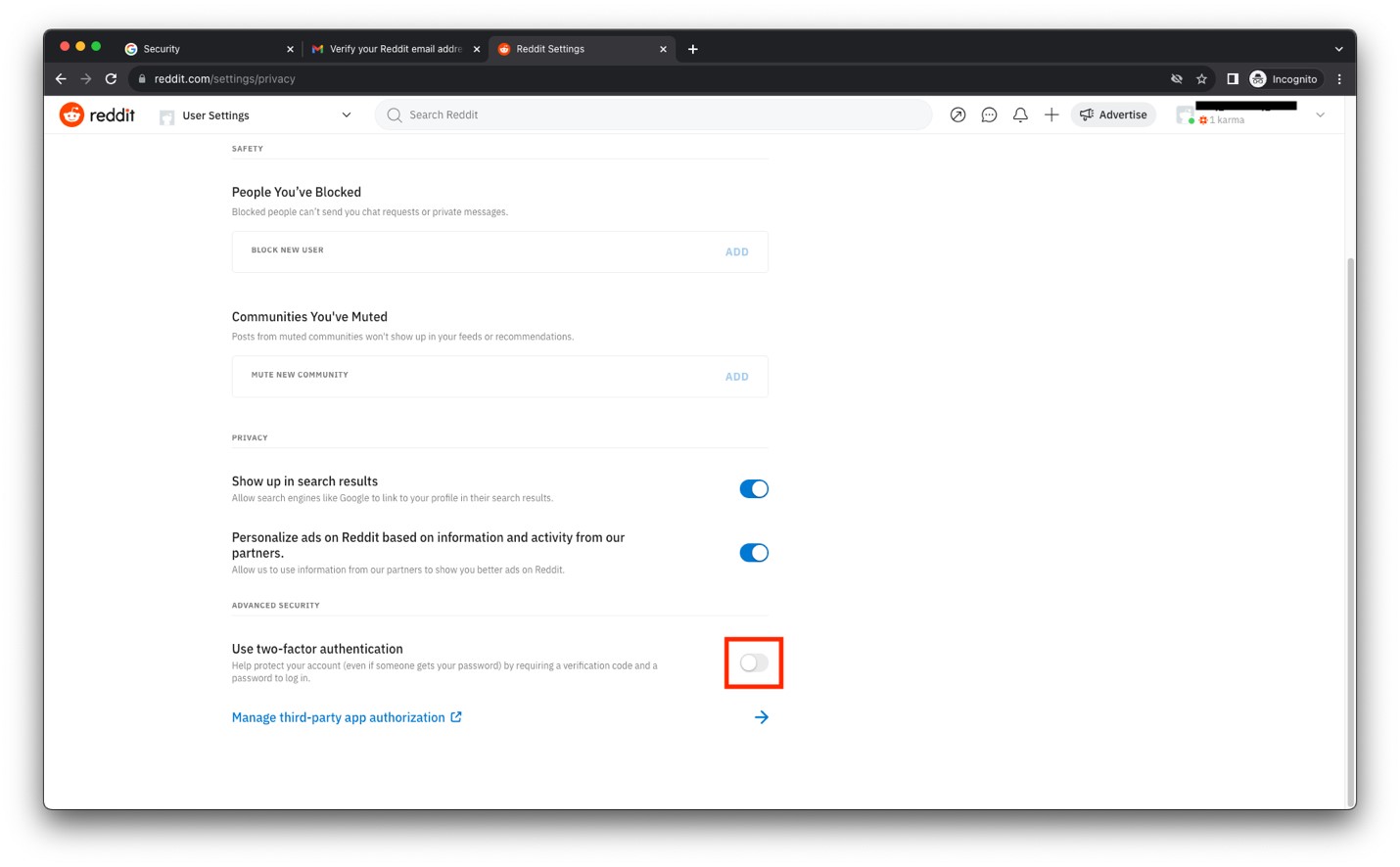
- Enter your password and click Confirm.
Image
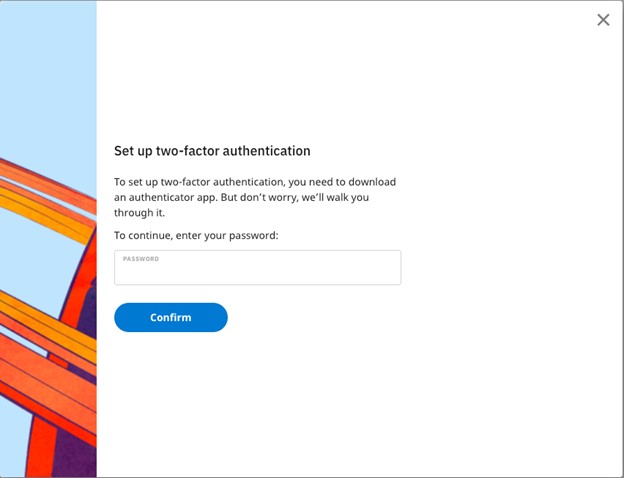
- Scan your QR code with your Authenticator app and enter the generated code into the 6-digit verification code box before pressing Complete setup.
Image
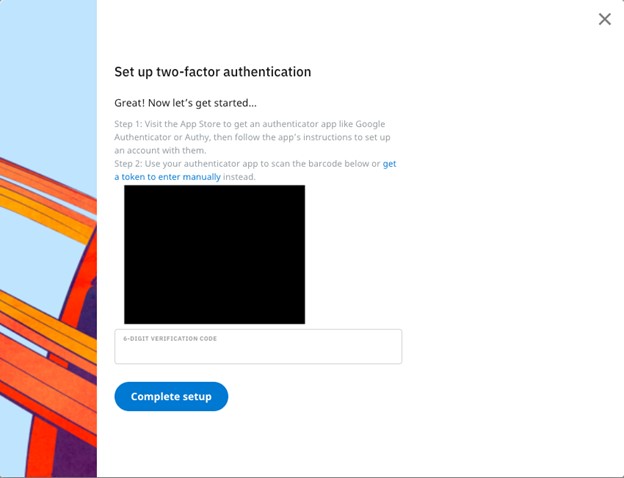
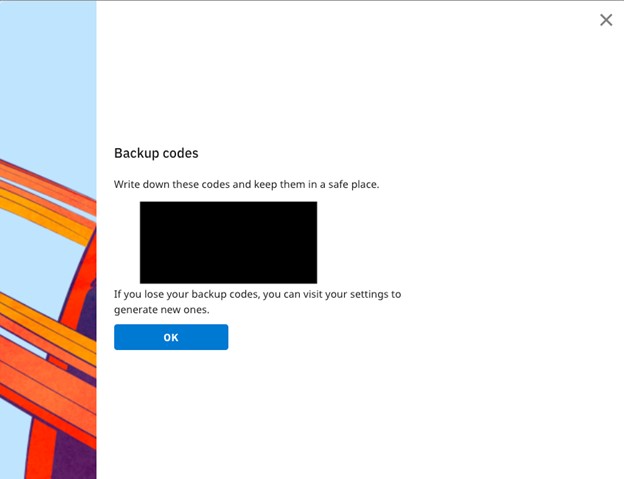
- Click the link to access your Backup codes.
Image
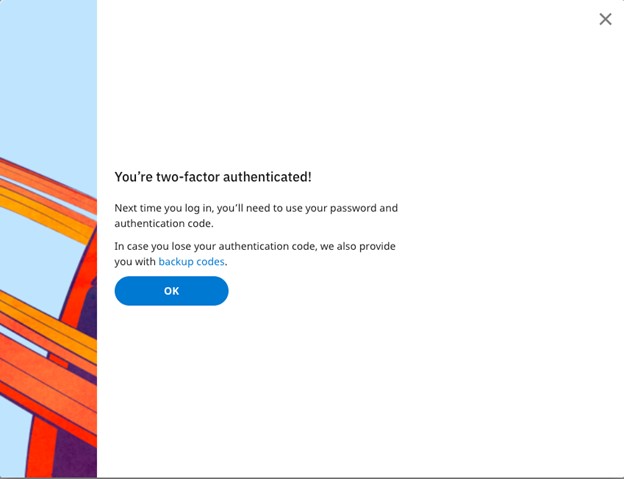
- Save your backup codes and click Ok.
Image
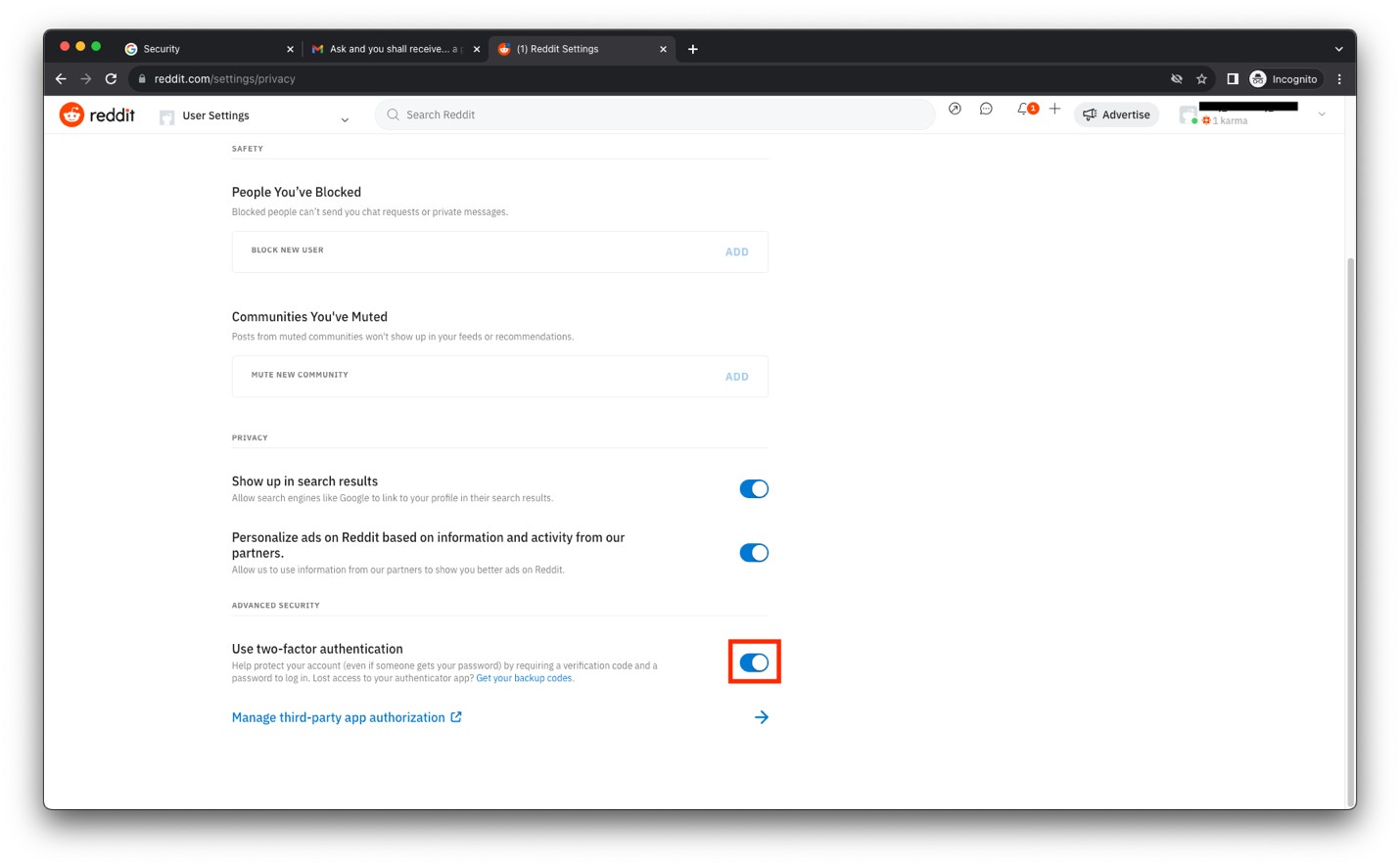
- You should now see the Use two-factor authentication switch enabled.
Image
- You’ll notice that you have a message from /u/reddit letting you know that two-factor authentication has been enabled.
Image
Twitch
- After you’ve logged into your account, click your user icon.
Image
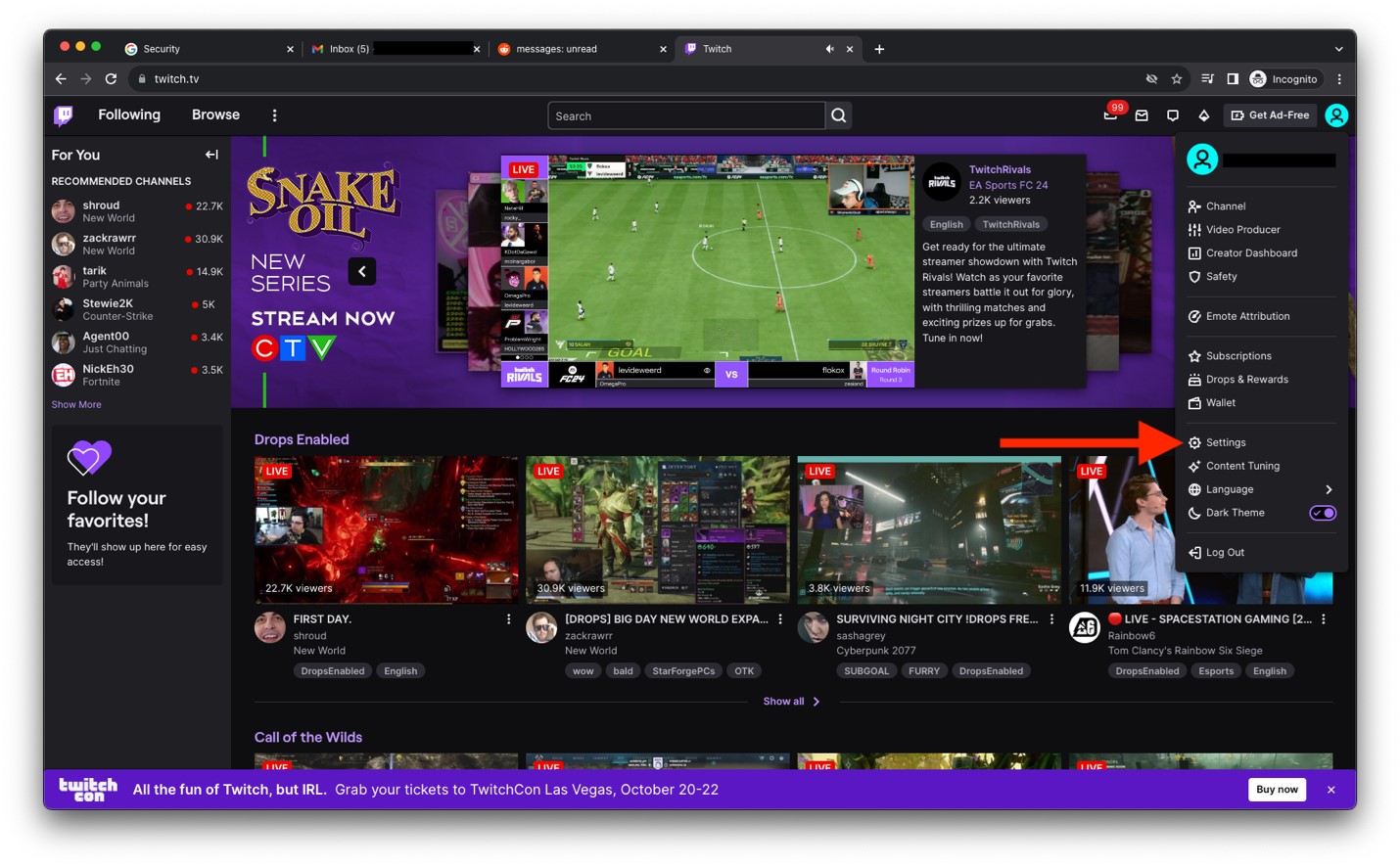
- Click Settings.
Image
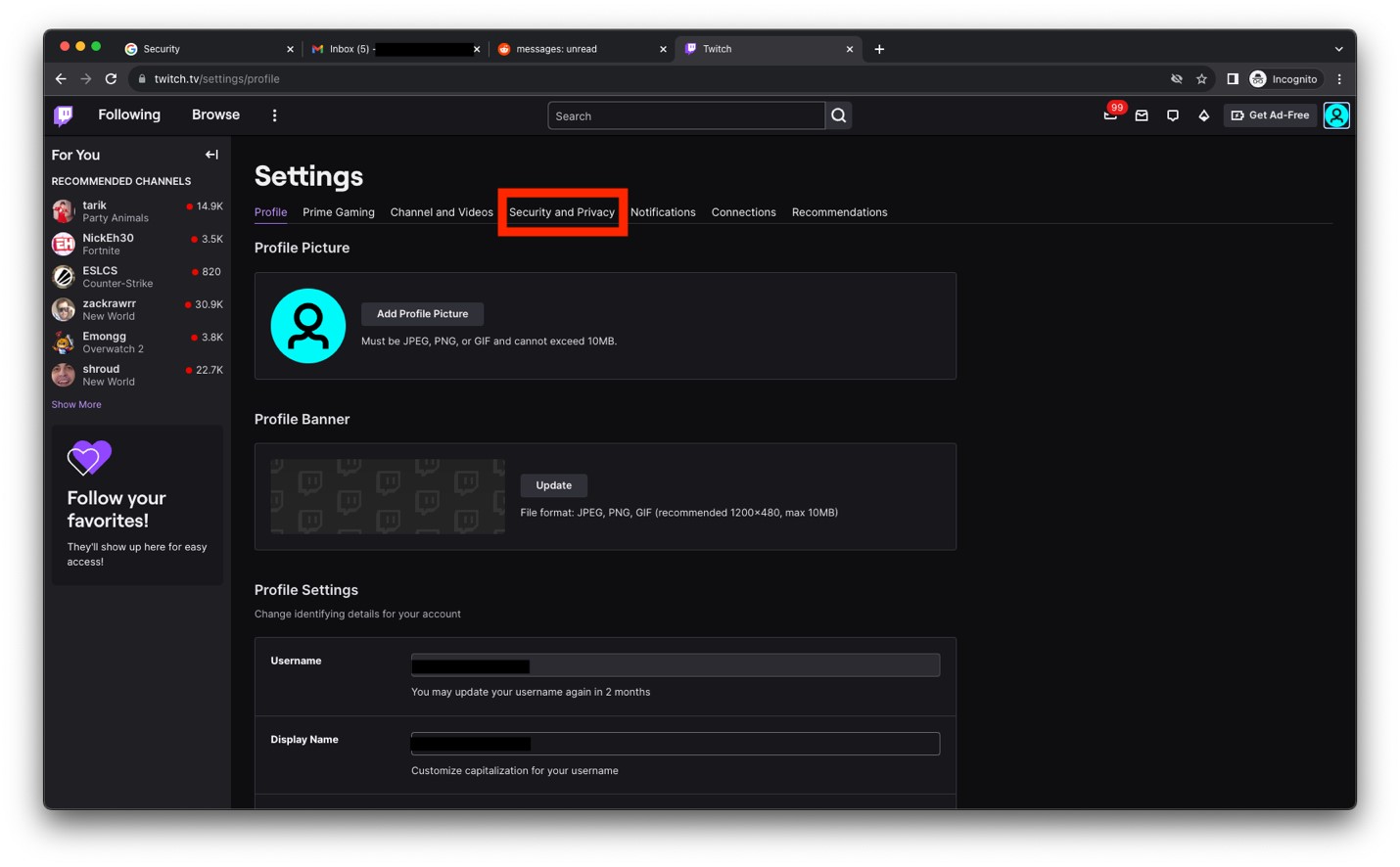
- Click Security and Privacy.
Image
- Click Set Up Two-Factor Authentication.
Image
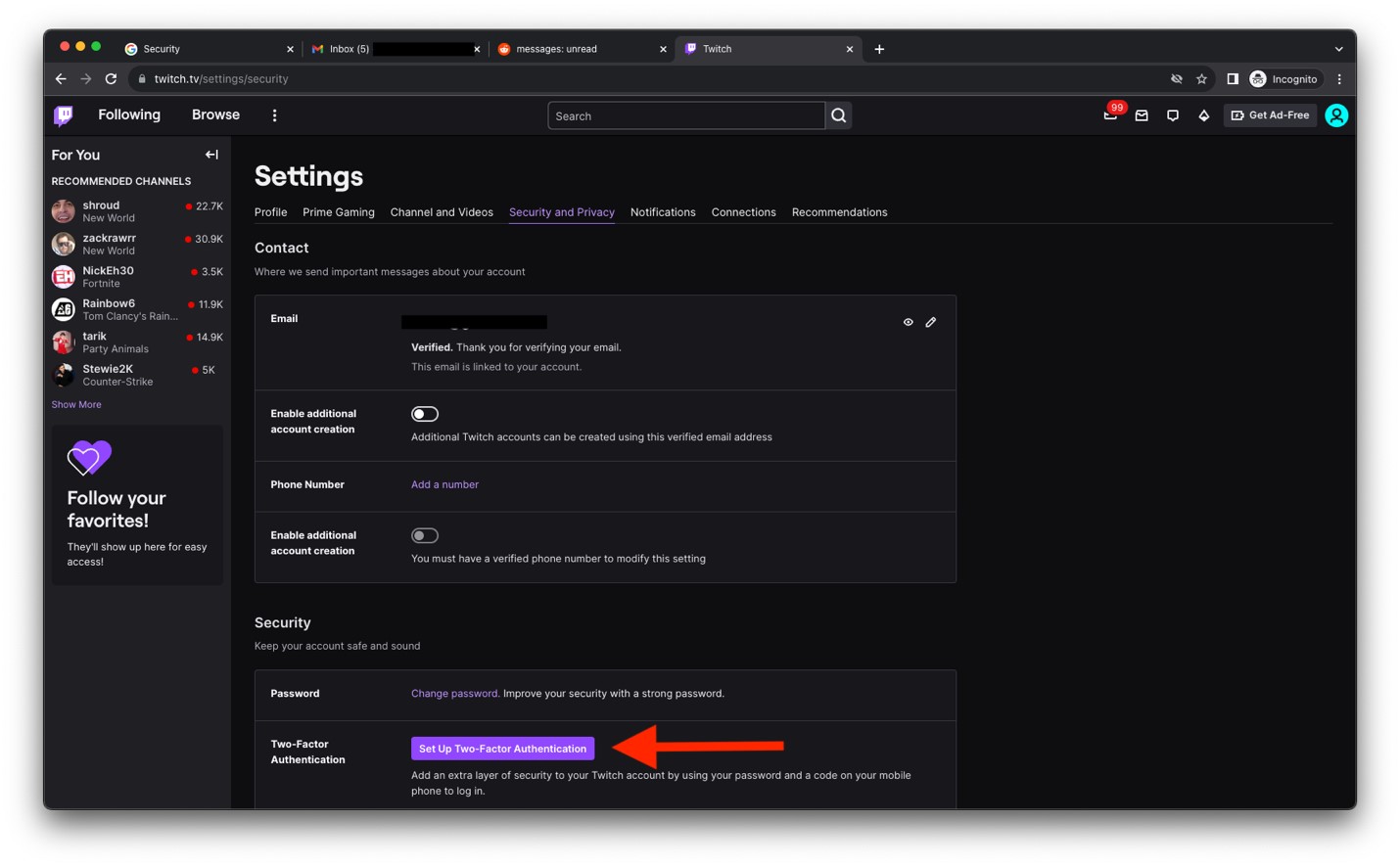
- Click Enable 2FA.
Image
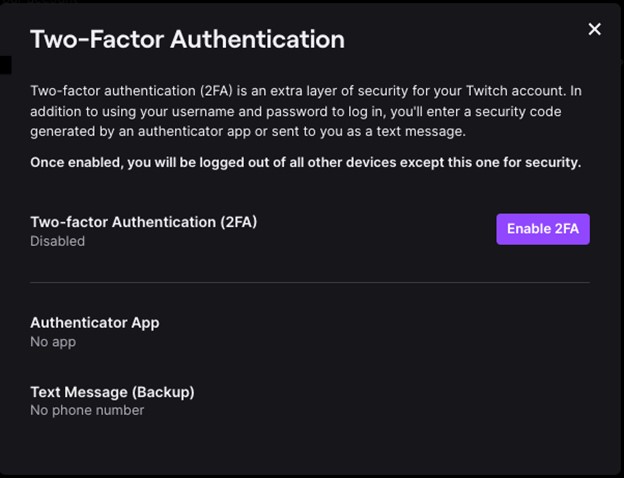
- Enter your phone number and click Continue.
Image
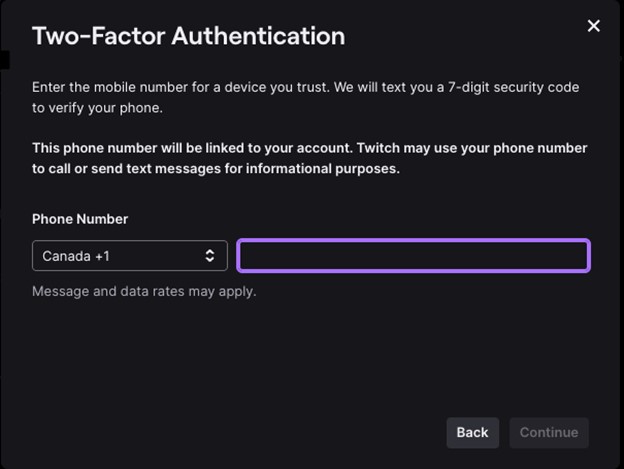
- Scan the QR Code with your Authenticator app, verify with a generated code, and click Submit.
Image
- You’ve setup multi-factor authentication, click Done.
Image
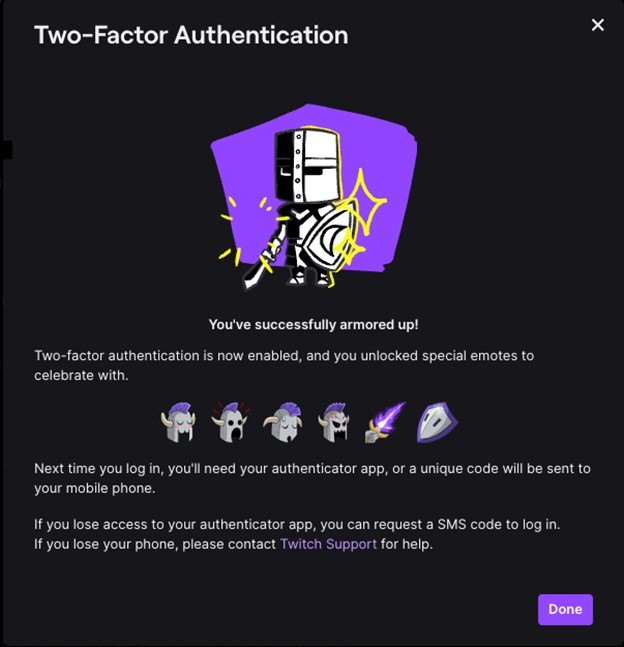
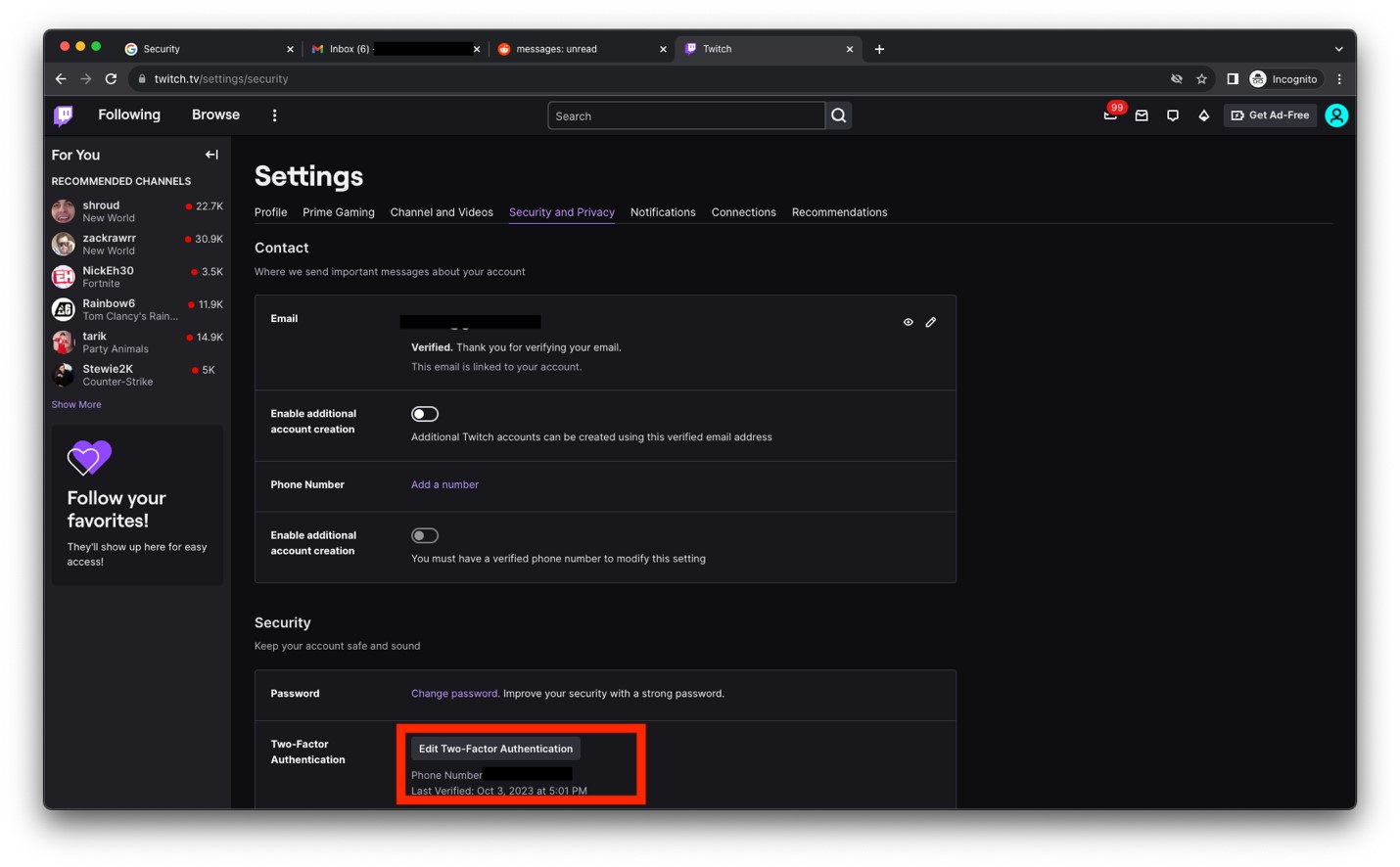
- Verify that the Security and Privacy page now says Edit Two-Factor Authentication instead of Set Up Two-Factor Authentication.
Image
Mastodon
- After you’ve logged into your account, click Preferences.
Image
- Click on Account.
Image
- Click on Two-factor Auth.
Image
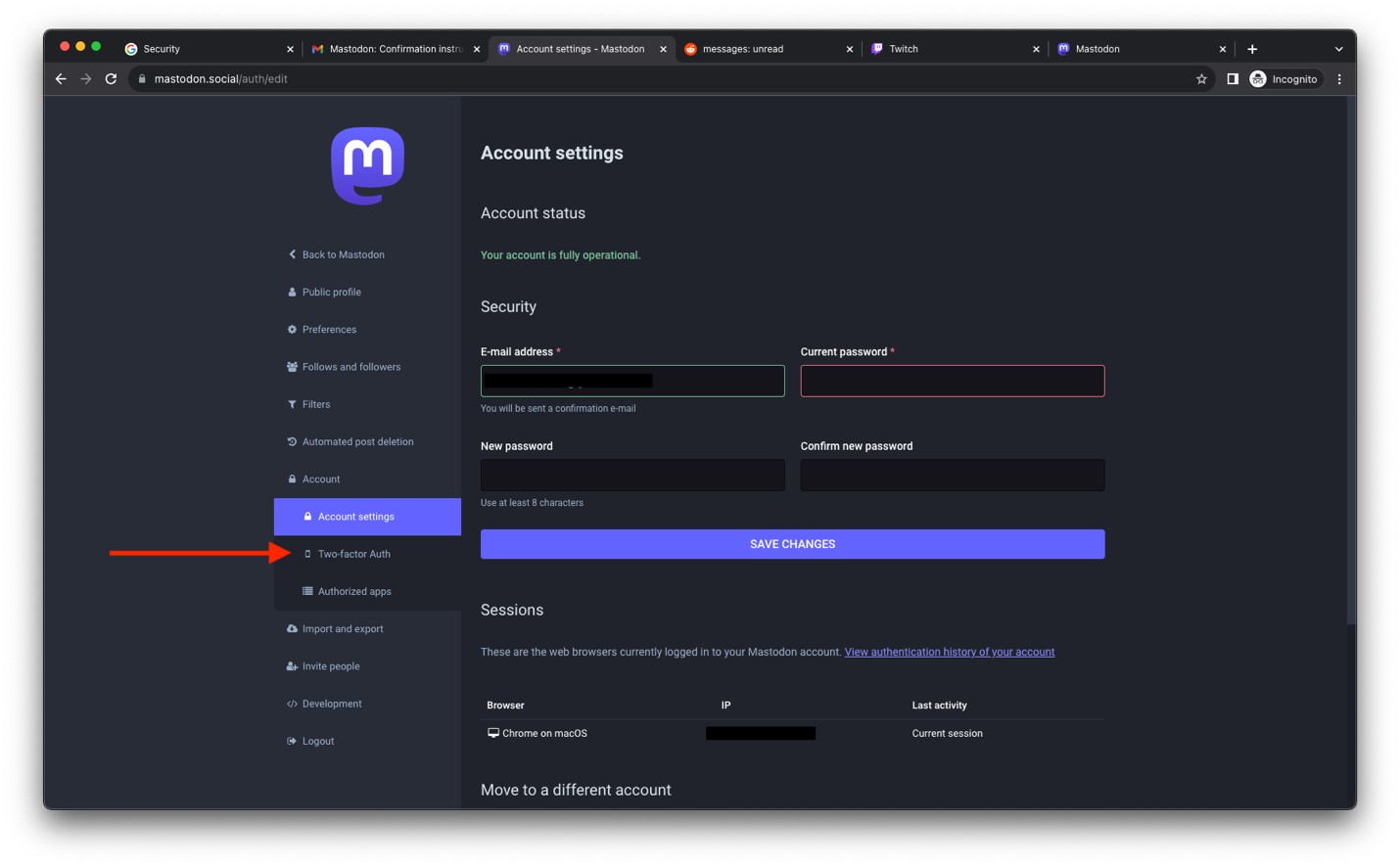
- Click SET UP.
Image
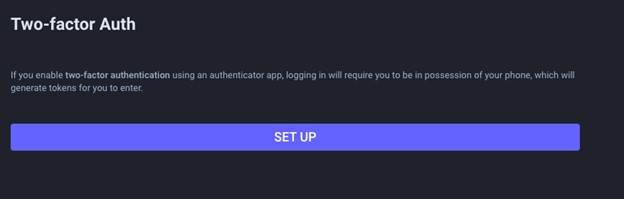
- Enter your password and click Continue.
Image
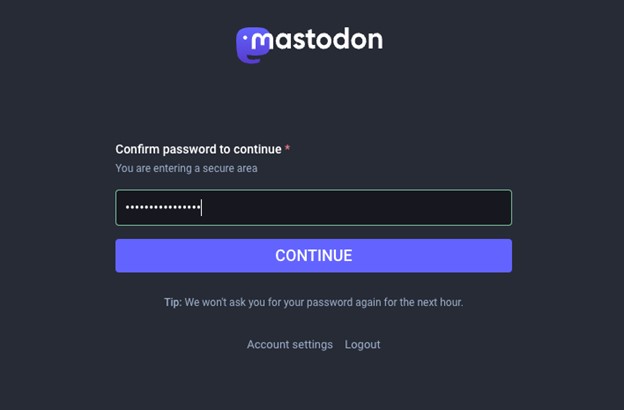
- Scan the QR code with your Authenticator app and enter in the two-factor code to verify, clicking the Enable button.
Image
- Save your backup codes, multi-factor authentication is now enabled.
Image
Enabling two-factor authentication is quick and painless in most cases, although it is recommended that you print out back-up codes from sites that support it. These codes can be a life saver when it comes to websites that use authenticator applications should you lose or damage your phone.
I’d like to leave you with one final tip. I’m a big fan of using single sign on (SSO) with websites. A lot of people question why you would want to use your Facebook, Google, or Apple account to sign into other services. I think there are three answers to that question:
- While these big tech companies may not care about you, they certainly invest more in security than little mom-and-pop websites. So, why put another password into a potentially less secure service, when you can let the credentials of the larger, likely more secure service provide value?
- Not everyone has two-factor authentication. By using SSO, you end up with free two-factor authentication assuming you have enabled it on the service you are using for all your SSO logins.
- There’s a reason enterprises use SSO. It means fewer passwords to track, fewer accounts to worry about, and an easier way to revoke the credential in the case of a breach.
Are there any websites that you’d like to enable two-factor authentication on that weren’t in the list above? Let us know.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

