
Zero Trust is a network security model that dictates that no one or no system should be trusted by default and that every attempt to access a network or application is a threat.
For those who are naturally trusting of others, this concept is difficult to accept. However, distrusting every entity on a network until it has been verified is imperative today.
Security Configuration in Zero Trust
When you have a multitude of platforms from a variety of vendors with different asset models, it becomes a challenge to ensure consistency across these assets. Therefore, it is crucial to ensure not only that the configuration of these devices is “what is expected” but also that they are in line with best practices for security guidelines. The addition of zero trust makes the task even harder.
Challenges in Implementing Zero Trust
There are many tools out there that can address these challenges, but are there tools that can help address all the challenges? Couple that with the ability to reduce costs, time, effort, and labor to help achieve this, and that’s where Fortra’s Tripwire Enterprise with compliance excels.
With Tripwire Enterprise, the monitoring of these assets is continuous. Therefore, any failures or lapses in security are highlighted immediately rather than after a breach event. This means that critical security flaws can be addressed and remediated to ensure your environments are secured. The best bit of this is that Tripwire Enterprise is not just for Windows or Linux platforms, but over coverage extends into your wider infrastructure.
The biggest challenge is not a technical requirement or constraint that needs to be overcome but rather one of reassurance to your users, staff, and colleagues. Since zero trust is implemented against systems and users, this in itself can present many challenges.
- Legacy Systems - Organizations still use systems that do not cater to or support a zero trust approach, which creates gaps in their security policy.
- Cost - Always a consideration for any IT project, but more so when looking to secure and harden any infrastructure. Organizations always have to ensure they address their most important concerns first, and this may not always include zero trust.
- All in one, but none for all – Buying a solution that is part of an “all in one” offering does not always address the specific needs of an organization. It is important to buy the right solution for your needs, not a solution that addresses a need.
- Time and effort – Implementing a zero trust approach will inevitably require additional intervention from a human in its initial outset, but as things settle, this process will become the “norm” for both users and administrators.
Best Practices for Leveraging Your SCM
Total confidence in your zero trust implementation is a crucial aspect of any cybersecurity strategy. Fortra’s Security Configuration Management (SCM) system enables superior monitoring of the zero trust approach. It ensures the settings are meeting your minimum best practice guidelines without deviation. It also helps by ensuring the zero trust infrastructure is monitored for any change and configuration drift.
Get a Baseline Configuration
With any SCM project, the first task is to establish a baseline configuration. This is done by identifying critical services and infrastructure. This enables you to define the security standards to meet your organization’s needs.
Aim for Continuous Monitoring and Remediation
By using configuration tools, you can automate the configuration and compliance checks on your infrastructure. Having Tripwire Enterprise helps monitor deviations and enforce compliance. The chart below illustrates an audit readiness methodology without an SCM, which is like a roller-coaster.
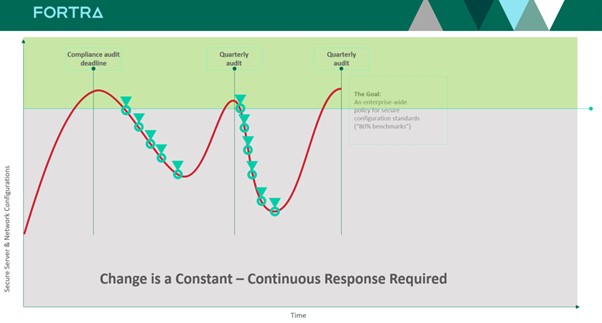
When it comes to zero trust, you want to be in a state of readiness, especially because the failure to notice, address, or remediate a misconfigured or changed setting is the difference between a secure environment and an insecure environment. The following chart illustrates how Tripwire takes the approach to continuous monitoring and remediation.

Automate Configuration Changes
In order to achieve continuous monitoring and remediation, you want to be able to implement an approach that applies the ability to ensure that the defined configuration is maintained on your assets. A key point is to ensure that the automation is implemented by a single configuration management system, otherwise there is a danger that the hardened settings could be undone by a secondary system.
Apply Zero Trust Principles
At its heart, you need to ensure that you apply the principle of least privilege, which ensures that systems are configured to grant only the minimum necessary permissions based on an entity’s requirement to perform a task.
Where possible, leverage micro-segmentation to create isolated environments within your network, bearing in mind that remote working and remote offices provide new challenges. Additionally, implement continuous authentication, which requires the ongoing verification of users and device identities as well as leveraging technologies such as MFA and passkeys.
Conclusion
In today’s world of work, where offices are remote, meetings are taken in coffee shops and gyms, zero trust is a requirement for all organizations. SCM ensures that the applications, systems, and devices are adhering to the best practice guidelines outlined for a more secure, hardened environment.
SCM is a cornerstone of achieving robust zero trust architectures. It plays a vital role in ensuring that systems are configured correctly and consistently, which helps to reduce vulnerabilities and mitigate risks.
Tripwire Enterprise: Security Configuration Management (SCM) Software
Enhance your organization's cybersecurity with Tripwire Enterprise! Explore our advanced security and compliance management solution now to protect your valuable assets and data.
