
The world of technology is never in stasis, but as frantic as the field is, information security moves even faster. Those of us who work to stay aware of the latest trends in cyber security sometimes lose sight of the sobering reality that most people don't have the time or drive to do this--especially if it's not paying the bills. The combination of something as important as security and something as ubiquitous as computers creates fertile ground for bad information from charlatans and good intentioned folks with very bad advice. For example, there is a very persistent rumor that antivirus is good protection from malware and viruses. Don't get me wrong, it has a place in the information security tool belt. Unfortunately, many consumers rely on it too heavily and fail to adopt more effective security measures. We've all seen the signs walking into our local electronics superstore: "VIRUS REMOVAL: $150,” “PC TUNE UP: $45,” "STAY PROTECTED FROM MALWARE: $99,” and so on. So what's wrong with these services? The answer is unsettling: the ability to create viruses and malware invisible to antivirus is not restricted to state sponsored threats; this ability is in the hands of the average script kiddie who knows a little bit about Metasploit. Hackers can test their malware against the very same tools used by big box store technicians and smaller retailers. They can continue to work on their malware until it is sufficiently hard to detect. This means that while antivirus may be able to alert you to a compromise by a clumsy piece of malware, it is not capable of confirming that your device is totally clean. A far more sinister bit of malware may be able to use the same attack vector without triggering an alert or exhibiting obvious signs of infection such as additional toolbars or browser pop-ups. Because of the speed of this digital arms race, new techniques arise that may put you at even more risk by using antivirus software. There was an issue just a few months ago in which the proxy used by Avast to analyze user web traffic made all Avast users vulnerable. This feature is meant to keep you safe, but in this case, it could have allowed an attacker to execute arbitrary code on your system! Unfortunately, techniques like these are required for antivirus to remain competitive in today's market. Other times, companies release software that is so bad it's hard to not assume malicious intent. Google disclosed an issue to Comodo for their "Chromodo" browser that disabled even the most basic web security; in this case it was the same origin policy. Disabling the same origin policy allows websites to steal any of your session cookies! It gives an attacker the opportunity to passively gain the ability to log in to any account using cookie-based sessions (most websites). When a user installs Comodo Internet Security, this browser is installed and designated the default browser (thereby putting the user at risk) automatically. This doesn't just happen to smaller or less reputable vendors. Recently, McAfee issued an update for their Enterprise Security Manager because hardcoded credentials allowed anyone to gain NGCP (master user) access by simply entering the username “NGCP|NGCP|NGCP;” and any password! This can be a very scary situation. At best, the tools you rely on to keep you safe give you a false sense of security, and at worst, they increase your risk. Fortunately, there are a few simple steps you can take to dramatically improve your security posture. Google summed up the current landscape with this excellent infographic:
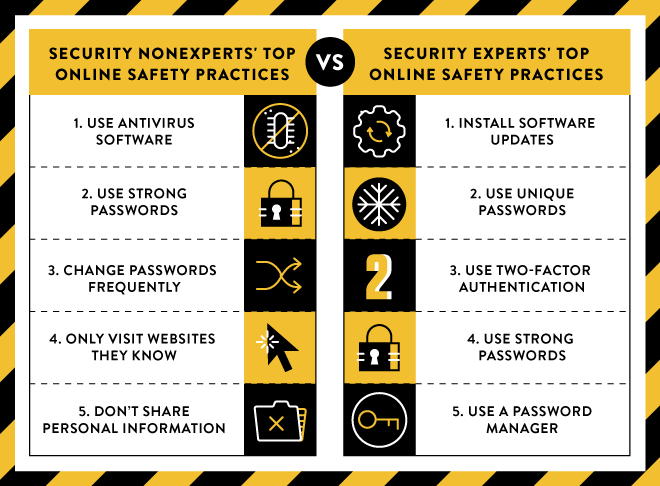
While average users consider antivirus to be a critical part of their security regiment, it is not nearly as important as keeping all software up-to-date. Having unique passwords managed by a password manager is a very close second. Ideally, software updates will patch discovered vulnerabilities and a password manager facilitates the use of unique, strong passwords for each account. In addition to taking these steps, it is important to understand and take steps to minimize exposure to other common attack vectors. The big three are piracy, ad networks, and unknown e-mail attachments or unsolicited links. I've known people who sincerely believe that pirates have a brand to protect, so they won't put malware in their uploads. Unfortunately, it's just not true. At the end of 2015, gamers were excited to play a brand new Fallout game. Some gamers felt justified in pirating the game, so they rolled the metaphorical dice and lost big. It turns out one of the popular uploads of Fallout 4 contained a piece of malware designed to steal Bitcoins from the pirate! While this attack was specific to Bitcoin, remember that when you pirate a piece of software, you allow an unknown and untrusted party to execute arbitrary code on your computer. Considering the aforementioned shortfalls of antivirus, it should be clear why this is so dangerous. In fact, it's a common tactic of pirates to "prove" the applications you're downloading are clean by linking to antivirus suites they know will miss the malicious software they've added. Ad networks are also quite dangerous; huge numbers of users can become infected by just viewing ads. In December of 2014, the Yahoo! ad network began unknowingly serving malicious ads that redirected users to exploit kits. What's really scary about these “drive by downloads” is you don't have to click or actively download anything to get infected. Simply visiting the site hosting the malicious ad is enough. While malicious sites certainly exist, you can cut down on your exposure to drive by downloads when visiting popular sites by installing ad blocking extensions in your browser. Some popular ad blocking extensions include uBlock Origin, Ghostery and Ad Block Plus. There are plenty more out there, but these are some of the more popular and easy to use extensions. Finally, e-mail attachments, links, and other phishing scams are still hugely successful. I am going to assume most readers of this blog are pretty savvy when it comes to not clicking on suspicious looking links. Unfortunately, the bad guys continue to develop new ways to trick users--using everything from advanced social engineering toolkits to tools that can more effectively package malware in PDF and Office documents. This is especially hard to protect against because everyone must collaborate and share documents at some point. The best we can do is to be mindful of what we open and constantly ask ourselves if we requested or are expecting these documents or links. While antivirus might be a useful tool under some circumstances, it is no longer the best line of defense. Even users who know what they are doing and generally have good security practices are exposed to increased risk by the poor, borderline negligent security vulnerabilities many antivirus and other security software introduce. Keeping your software and operating system up-to-date and being smart about what you download and how you browse the internet are going to give you vastly more protection than antivirus software. Title image courtesy of ShutterStock

