
Verizon Enterprise has named ransomware the most prevalent variety of malware in its 2018 Data Breach Investigations Report (DBIR). For the 11th edition of its report, Verizon Enterprise analyzed 53,308 incidents with 2,216 confirmed data breaches. Researchers with the American multinational telecommunications conglomerate found that three in 10 incidents included malware. Of those that did, ransomware made itself known in 39 percent of cases. Gabe Bassett, senior information security data scientist at Verizon and co-author of the DBIR, told TechRepublic he's seen ransomware grow significantly since the company first discussed the threat in its 2013 report:
Ransomware has doubled year over year again—it happened last year as well. The reason we're seeing this incredible prevalence is ransomware is a great value proposition for the attacker. They don't have to do a lot of the complex work. They just drop a piece of malware and then let it run.
Criminals don't even have to build their own crypto-malware families. Ransomware-as-a-service (RaaS) platforms like Data Keeper make it easy for affiliates with little-to-no technical skills to conduct their own attack campaigns across numerous devices including desktops and network assets. Compared to other threats, ransomware also does not impose significant costs or risks on the attacker, nor does it require adversaries to monetize victims' stolen data after a successful infection. It's self-contained and leverages its built-in cryptographic functionality to generate profits for a bad actor.
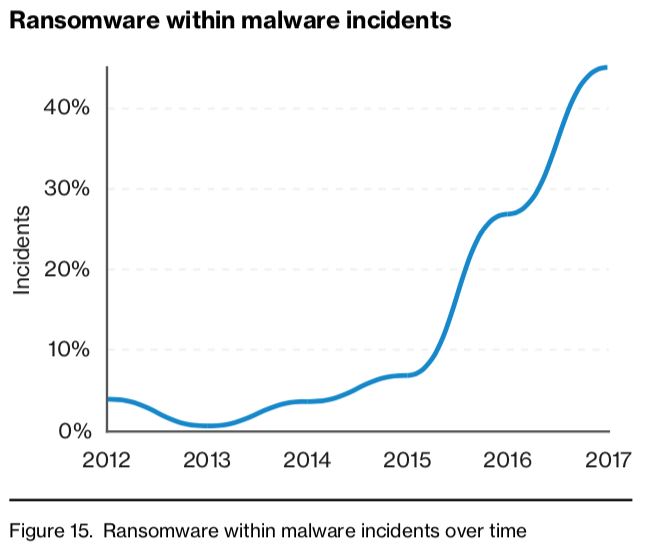
Verizon's 2018 Data Breach Investigations Report (DBIR) page 14 Another reason why ransomware is so prevalent is the fact that employees continue to fall for social attacks. Verizon detected 1,450 such incidents with 381 confirmed data breaches in its report. The vast majority of those leveraged phishing at 1,192 incidents with 236 instances of confirmed data disclosure. Pretexting, a common type of phishing, registered 170 incidents with 114 confirmed data breaches for the year. With respect to success rates, researchers with Verizon Enterprise found that 78 percent of employees didn't click on a phishing link all year. But it uncovered that four percent of targets in any campaign did and that the number of malicious employees opened by employees in the past increased their chances of clicking on an attack link in the future. To protect against these threats, Verizon recommends that organizations log files, monitor for changes and patch their systems promptly. They can do so using solutions like Tripwire Log Center, Tripwire File Integrity Manager and Tripwire IP360. Organizations should also implement measures to prevent a crypto-malware infection as well as train their employees to be the first line of defense against phishing attacks and other threats.

