
Security researchers witnessed the deployment of PonyFinal ransomware at the end of extended human-operated attack campaigns. In a series of tweets, Microsoft Security Intelligence revealed it had observed human-operated campaigns laying in wait for the right moment to deploy PonyFinal ransomware as their final payload. In their operations, the attackers used brute force attacks against a targeted organization's systems management server as a means to initially gain access. They then deployed a VBScript to run a PowerShell reverse shell. This asset helped the malicious actors execute data dumps. The nefarious individuals also bypassed event logging using a deployed remote manipulator system. It's at that point that PonyFinal's handlers abused information stolen from their target's systems management server to move laterally to endpoints on which Java Runtime Environment (JRE) was installed. Sometimes, they ran JRE themselves to support this effort. For the final step of delivering their payload, the attackers turned to a MSI file containing two batch files and the ransomware payload. The first batch file created a scheduled task that subsequently called the second batch file. This resource was responsible for downloading PonyFinal ransomware. It's then that the threat got to work. https://twitter.com/MsftSecIntel/status/1265674292013920257
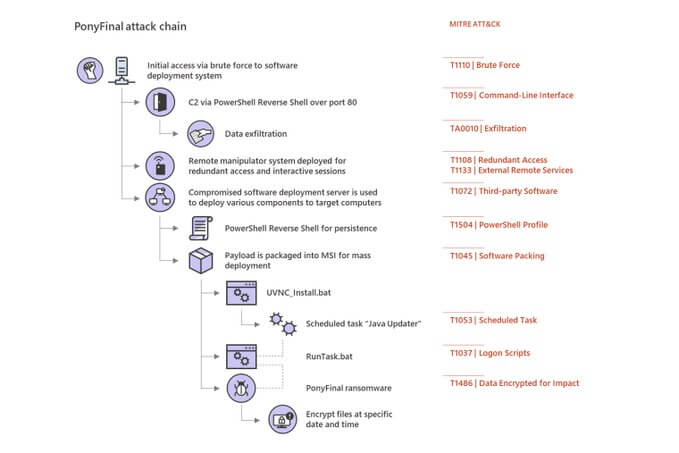
PonyFinal's attach chain (Source: Microsoft Security Intelligence) The PonyFinal samples observed by Microsoft Security Intelligence were a bit unusual in that they were Java-based. Malware authors have used Java to create other ransomware strains, but the tech giant's researchers noted that those threats far less common than families that use other file types. Even so, the security firm revealed that the PonyFinal campaigns it discovered fell into the greater trend of human-operated attacks. It therefore urged organizations to make an effort of defending themselves against these types of attacks. Specifically, it highlighted the importance of organizations hardening their web-facing assets and implementing security practices. The attacks described above also highlight the importance of organizations taking steps to prevent a ransomware attack in the first place. These steps provide organizations with an excellent starting point.

