
Scammers designed a phishing website and encrypted it with the Advanced Encrypted Standard (AES) in their attempts to steal unsuspecting users' Apple IDs. Researchers at Trend Micro came across the phishing campaign on 30 April. It all began when they received an email designed to look like it came from Apple. The email warned recipients that Apple had restricted their account access due to "unusual activity," and it required them to update their payment information to fix the issue.
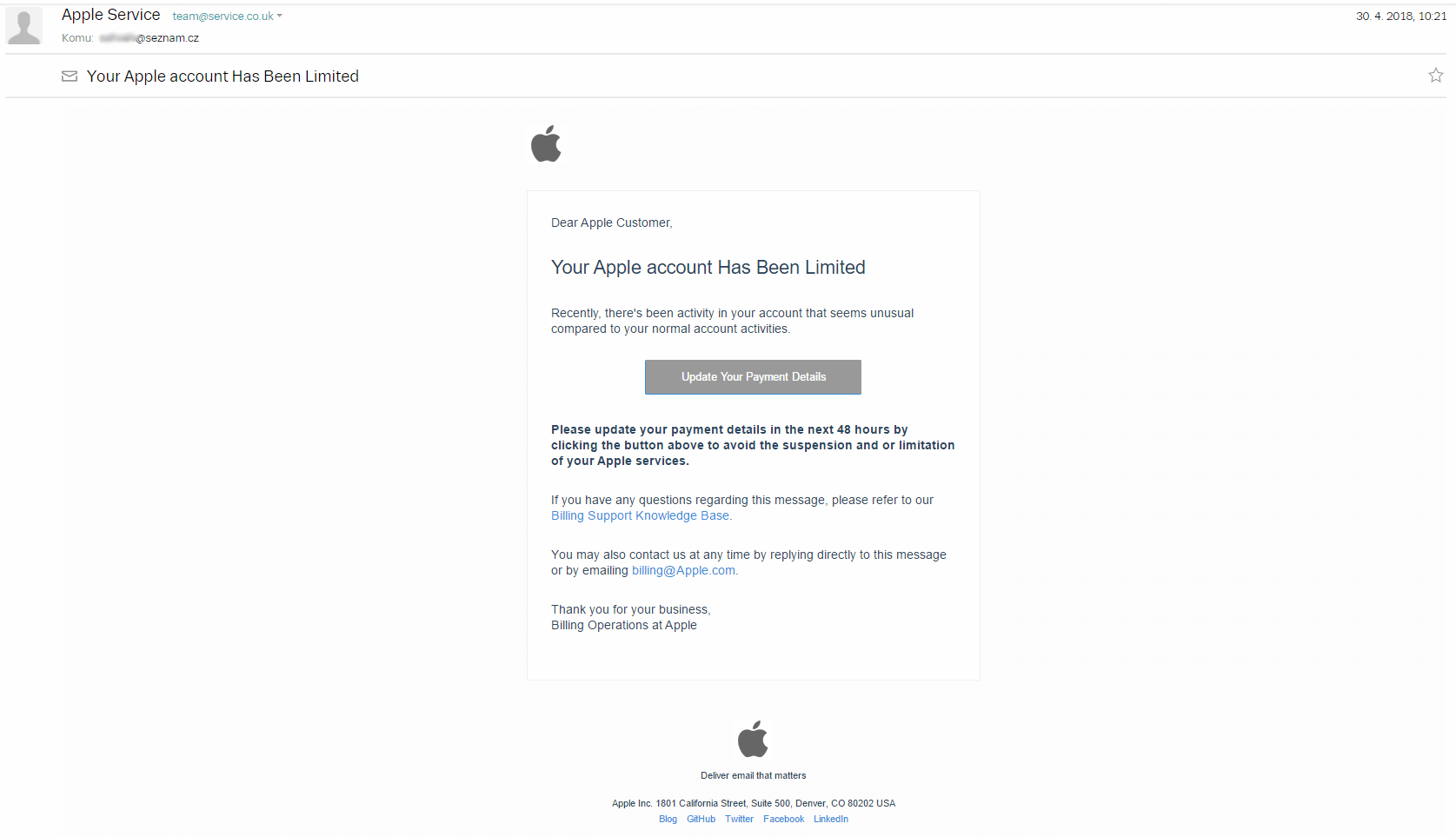
The phishing email received from what appears to be Apple. (Source: Trend Micro) Of course, the email was a fake. Its "Update Your Payment Details" button led users to a site that looked like Apple's sign-in page. Before going offline, the website was located at the following sanitized link: hxxp://avtive1s[.]beget[.]tech/limited/apple-couzin/apple%20couzin/Uu4gX/login.php?sslmode=true&access_token=1SGMm8LG43m4qPGE7D8Q00qCRZ2hwIVyBBkYK6FP91UzQBeYemPenfQeeTwLCrjd3EcNKRDUTxuJ8IIm. After they attempted to sign in, the phishing website informed users that Apple had suspended their accounts due to suspicious activity. It then directed them to a sophisticated webpage designed to collect unsuspecting users' personal and payment card information. After acquiring all of this data, the site "logged out" its victims and redirected them to Apple's actual homepage. This campaign wasn't the first scheme aimed at stealing users' Apple IDs. But what made it unique was its incorporation of code in “login.php,” “process.php” and “verified.php” to invoke JavaScript-based AES obfuscation with custom variables.
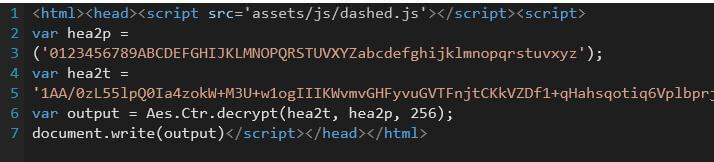
AES encryption implementation designed to conceal the malicious payload. (Source: Trend Micro) Trend Micro researcher Jindrich Karasek elaborates on what this implementation of AES encryption meant for the phishing campaign:
Network packet inspection would not identify this as malicious because the payload is hidden thanks to the encryption. The only way to spot this threat is via reputation services that identify the sender as malicious. The unique way that this phishing scam used AES makes it difficult to detect malicious activity. The phishing site was able to bypass some anti-phishing tools incorporated in antivirus solutions for home and business from various vendors.
AES-protected websites can certainly help phishers evade automated email security solutions, but it won't make much difference against informed users. With that said, users should familiarize themselves with some of the most common types of phishing attacks. This knowledge can help them be on the lookout for emails that leverage a sense of urgency and faulty logic to direct recipients to suspicious domains.

