
An ongoing targeted phishing campaign is making off with industrial companies' money and sensitive corporate information. In October 2016, Kaspersky Lab identified a spike in the number of malware infection attempts received by customers with industrial control systems (ICS) installed. The malware arrives via well crafted phishing messages that exploit a Windows vulnerability dating back to 2015. As of this writing, the Russian digital security company has traced the reach of the attack campaign to over 500 companies spread across 50 countries. The first stage of the campaign involves setting up a malware command-and-control (C&C) server. In some cases, the attackers choose domain names that mimic the domains of their targets. Kaspersky Lab ICS CERT expands on this point:
"An analysis of these domain names sheds light on the tactics used by the phishers. They try to register the same domain name as the targeted company’s legitimate resource, but in a different top-level domain. If this is impossible, the attackers register a domain with a name that looks very similar to the legitimate domain’s name (a standard technique is to replace one or more characters). We have also seen another technique used in these attacks: the domain name is made up of the legitimate site’s name and the name of its top-level domain."
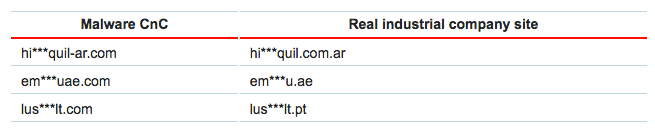
Phishing domain names mimicking legitimate domain names. (Source: Kaspersky Lab) Other times, the bad actors gain unauthorized access to industrial companies' websites and use them to host malware. Those responsible for these attacks likely steal the credentials by infecting employees' computers with a malicious program like a keylogger or spyware. Most cases involve the attackers going after their targets' suppliers, customers, commercial organizations and delivery services. They do so via business email compromise (BEC) attacks, a type of scam which cost Southern Oregon University $1.9 million in late April. After compromising employees' emails using trojans and backdoors, the nefarious individuals set up domain names that are similar to the seller companies, create hidden message redirects to email accounts under their control, and look for pending business transactions. They then carry out a man-in-the-middle attack where they intercept an invoice to the seller, change the transaction details to include one of their accounts as the seller's bank account, and send the message to the buyer. A successful attack tricks the buyer into sending payment to the attackers' bank account.
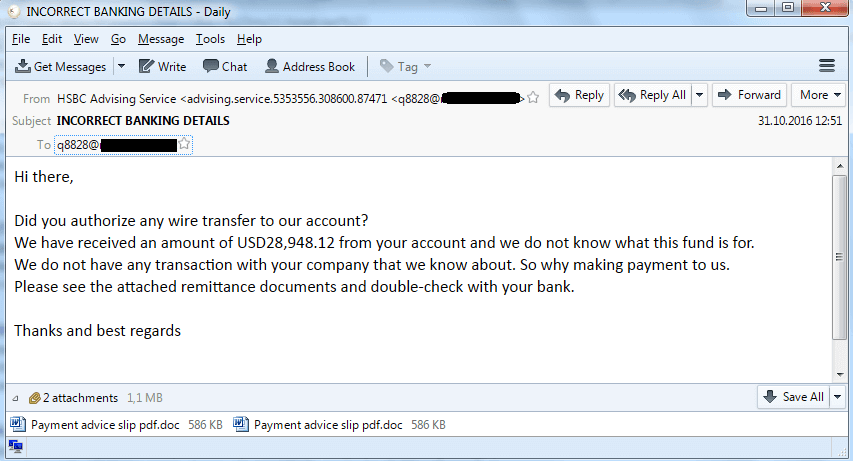
One of the phishing messages. (Source: Kaspersky Lab) The bad actors don't stop there, though. Kaspersky explains:
"All the emails had malicious attachments: RTF files with an exploit for the CVE-2015-1641 vulnerability, archives of different formats containing malicious executable files, as well as documents with macros and OLE objects designed to download malicious executable files."
These resources download one of eight trojan-spy or backdoor families, programs which conduct reconnaissance of a machine, collect information, and send data back to their C&Cs. Kaspersky's researchers confirmed this when they found snapshots of sensitive information like technical drawings, floor plans, and project proposals stored on the servers. Such data loss poses an even greater threat to industrial organizations than misdirected funds or an unpaid contract. To protect against attack campaigns such as the one described above, industrial organizations should create policies by which a seller or third-party must confirm a change in payment either via phone or in-person. They should also examine the security of their supply chain to make sure associated service providers conduct ongoing security awareness training with their employees.

