When most people think of penetration testing, they think of a simulated external attack where the tester tries to break into a network remotely. Companies focus most of the security spending and policies on keeping hackers out remotely, from firewalls and other security hardening appliances, software and tools. However, given the proliferation of mobile devices in the workplace and use of Wi-Fi networks inside of an office, attacking from inside the network provides some unique opportunities.
Mobile devices have accelerated productivity as they move to replace many of the other devices we used to carry in a small package. Most phones have Wi-Fi capability, cameras, mass storage capability and a persistent internet connection via 3G and 4G and allow a wide number of applications and if rooted provide many of the same tools as a computer, but with more hardware and network capabilities. These conveniences also carry over to make them an very powerful tool to use in penetration tests, more powerful I would argue than a laptop, as a mobile device can be easily hidden on your person, or inside of an office building.
Disclaimer: The information in this article is for research and testing purposes only, the tools and techniques outlined here should only be used on test networks you own and/or have permission to run them on. Some of these tools can cause damage to both your phone as well as target networks, DO NOT USE THESE TOOLS ON WORK NETWORKS OR NETWORKS YOU DO NOT HAVE PERMISSION TO TEST THEM ON.
The Phone Setup
As my weapon of choice I am using an Android phone, a rooted Samsung Galaxy S to be specific. I highly recommend rooting the phone and installing a ROM such as Cyanogen, for my tests I used Cyanogen 7. Many of the apps I will mention here require a rooted device and require root privileges. Rooting a phone can break it and make it more vulnerable to malicious applications, I would recommend you do not use your main actual phone for this purpose.
You can install most Linux distros on an Android phone including Backtrack 5 using Gitbrew. However using a Linux distro on an Android phone, even on a tablet is quite kludgy and you would be better served using a netbook. For this article I will stick with Android specific tools that take advantage of the portability and hardware available to smartphones. If have had good experiences running tools on other platforms please share in the comments.
Network & Vulnerability Scanners
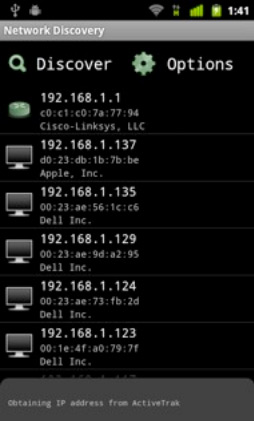
The first mobile application I used in my tests were for network mapping and enumeration, there are quite a few available in the Android Marketplace. Network Discovery, is a great one that is free and does not require your device to be rooted. The user interface is really well designed and provides you with a clear view of the network and devices at a glance, not easy to do with the limited screen real-estate on a mobile device. The application identifies the OS and manufacturer of the device as well as identifies the type of device. The Network Discovery app works well when connected to a Wi-Fi network that you know is open or have the password to access and provides great visibility of the target network.
Mapping a network is one thing, but being able to scan for open Wi-Fi, scan device ports, find vulnerabilities and other acts take a lot more time and usually a lot more tools. An Israeli security firm called Zimperium has made this easier for you, with their Android Network Toolkit named Anti, there is also a great open source project called dSploit, which I have not fully tested yet due to some bugs I ran into on my phone, but once I get it working will do a follow up post.
Anti and dSploit provide automated tools to carry out penetration testing tasks. Once activate the apps run scans to find open networks, locate devices on the network and determine vulnerabilities on the devices. Once vulnerabilities are discovered the Anit can run some exploits from Metasploit and ExploitDB to gain access at which point you can then trigger various actions remotely taking a screen shot to ejecting the disc drive to prove you have control of the target machine.
The first version of Anti only had a few exploits, however the developer provided me with an early version of the newer release which has a larger library of potential exploits. In addition the suite provides additional tools including a brute force password cracking tool along with different types of dictionaries to load for the attack, some of which are provided at a premium.
The “Cracker” feature runs well and hits all open ports it finds on devices within the network. This can take some time depending on the number of ports and the type dictionary used in the attack. I was able to locate several vulnerabilities on a test network, mostly Windows file shares and a router that still had the manufacturer’s default password settings.
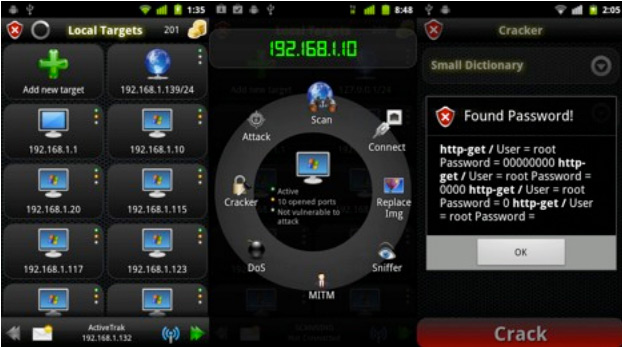
The in-app Wi-Fi monitor feature provides a listing of all Wi-Fi networks, their signal strengths and whether or not they are open via an easy to read icon, along with the device’s MAC address. The network scanning is quite fast and I was able to map a decent sized network in about 30 seconds. When you run the scan it then asks you if you want to initiate an intrusive scan which gathers more information regarding potential vulnerabilities.
Anti and dSploit are great tools that make mobile penetration testing as easy as one click, allowing you to run quick tests for unsecured Wi-Fi networks and gather information in an automated fashion. The fact you can initiate a scan and put the phone in your pocket makes it a powerful tool.
Read the Guide
Climbing Vulnerability Management Mountain
How to Build a Strong Vulnerability Management Program
