
Businesses should patch their TP-Link routers as soon as possible, after the revelation that a legendary IoT botnet is targeting them for recruitment.
The notorious Mirai botnet, which hijacks control of vulnerable IoT devices, is now exploiting TP-Link Archer AX21 routers to launch distributed denial-of-service (DDoS) attacks.
The warning comes from security researchers and the US Government's Cybersecurity and Infrastructure Security Agency (CISA), after it was identified that a security flaw in the TP-Link Archer AX21 Wi-Fi router was being actively exploited in order to allow malicious hackers to execute malicious code remotely.
The high-severity security vulnerability was first disclosed by bug hunters in December 2022 at the Pwn2Own hacking contest in Toronto, earning them a US $5,000 prize.
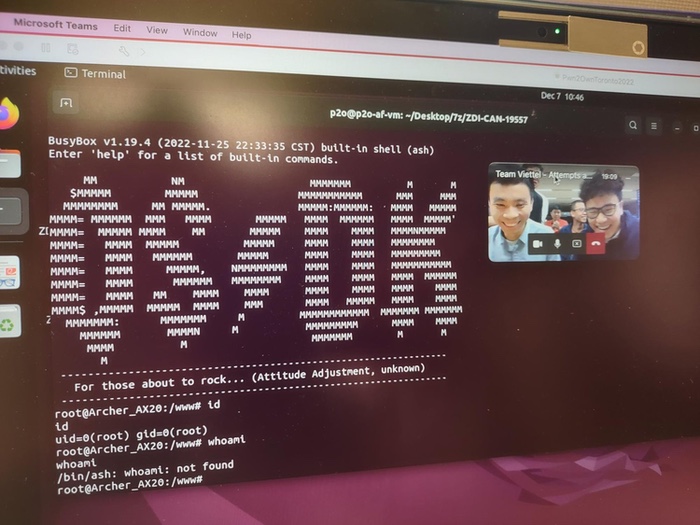
The revelation prompted TP-Link to issue a firmware update (that did not properly fix the issue) two months later, followed by another update (that did resolve the vulnerability) in March 2023.
Unfortunately, it seems that malicious hackers did not waste any time incorporating exploits of the flaw (dubbed CVE-2023-1389) into Mirai's arsenal, hence the current attacks which have been taking place since last month.
The only recommended action to prevent the exploitation of the vulnerable TP-Link routers is for them to be updated with the latest firmware update, which closes the security hole.
The Mirai botnet first came to the wider world's attention in October 2016, when it launched a massive DDoS attack on DNS service company Dyn, making it impossible for many users to reach popular sites such as Amazon, Reddit, Netflix, Twitter, Soundcloud, Spotify, Etsy and Github.
Three men were subsequently sentenced for their part in the running of the Mirai botnet.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire.
Mastering Security Configuration Management
Master Security Configuration Management with Tripwire's guide on best practices. This resource explores SCM's role in modern cybersecurity, reducing the attack surface, and achieving compliance with regulations. Gain practical insights for using SCM effectively in various environments.

