As our interactions with the digital world grow, connections will be established within seconds, leading to more online attacks. One type of attack we may be exposed to is known as a Man-in-the-Middle (MitM) — a technique cyber attackers use to take over our online communications.
The best way to stay safe online is with a better understanding of the problems caused by these digital attacks and identification of the dangers and consequences they entail.
Understanding MitM Attacks
This form of attack happens when an adversary intercepts a communication process. The attacker positions himself between the legitimate participants—the sender and the receiver. Their motives dictate their actions; they might passively eavesdrop on communication channels, steal information from users, actively tamper with and modify data, or even masquerade as authorized users.
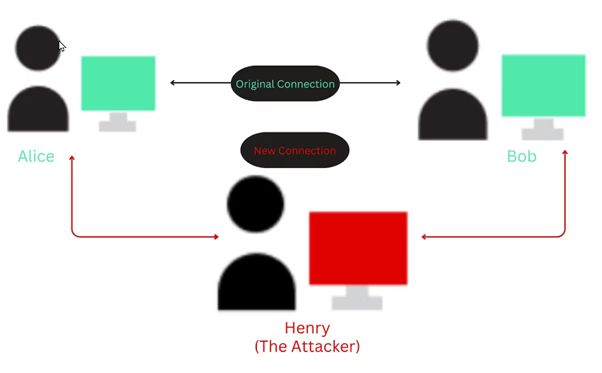
Consider this scenario featuring three individuals: Alice, Bob, and Henry (the attacker).
1. Henry covertly monitors the communication line connecting Alice and Bob.
2. Alice sends a message to Bob.
3. Henry covertly intercepts and reads Alice's communication, unknown to Alice or Bob.
4. Henry manipulates the message between Alice and Bob, yielding an unexpected response.
Picture yourself as either Alice or Bob in this narrative. How would you go about detecting a MitM attack? The task requires a blend of vigilant observation and the use of specialized yet easy-to-use tools.
Detecting MitM Attacks
Frequent Disconnections: The attacker forcefully disconnects you from a public or compromised network, aiming to intercept your login credentials as you attempt to reconnect.
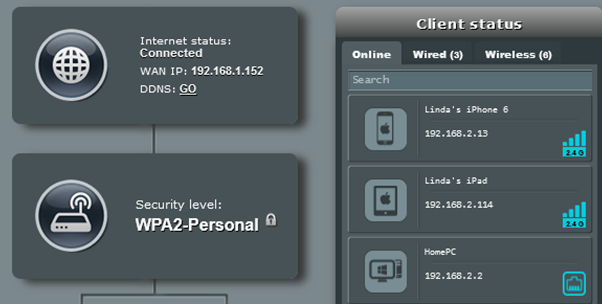
Unrecognized Network Device: Check the devices connected to your network. Most home routers offer the ability to easily see all of the connected devices. They also enable you to give your permitted devices a common name for easy identification. If you identify an unauthorized device, an attacker may be on your network.
SSL Certificate Errors: Exercise caution if your web browser issues warnings about invalid SSL certificates from supposedly trusted sites. Such warnings could indicate an attacker's endeavor to intercept your HTTPS traffic through techniques like SSL stripping.
Employ Security Software: Keep your anti-malware software updated. This can identify MitM attacks and other suspicious activities.
Periodic Account Checks: Regularly check your accounts for any signs of unauthorized logins or transactions, and take swift action if detected.
MitM Attack Prevention Measures
Secure Connections: Opt for websites employing HTTPS, identifiable by the padlock icon in the address bar. Implementing HTTP Strict Transport Security (HSTS) policies fortifies security by blocking insecure connections and thwarting attacks.
Exercise Caution with Emails and Links: Exercise caution when interacting with email or message links, particularly if they solicit sensitive data. Validate a link’s legitimacy by hovering your mouse pointer over links, which will reveal the destination URL and steer clear if doubts arise.
Cautious Use of Public Wi-Fi: Do not access sensitive information or conduct online transactions over public Wi-Fi networks. If necessity dictates public Wi-Fi usage, safeguard your data through the use of a Virtual Private Network (VPN). As always, it is best to pay for a reliable VPN rather than using a free one, as free products can also include malicious software.
Activate Multi-Factor Authentication (MFA): Fortify your online accounts by enabling MFA on any site that offers it. This supplementary layer of security bolsters defenses.
Continual Self-Education: Stay abreast of prevalent online threats and best practices in cybersecurity. Many free sites, as well as law enforcement agencies are available to make the job easy. Enhanced awareness empowers you to improve your self-protection.
Risks and Consequences of MitM Attacks
Data Theft and Privacy Intrusion: MitM attackers can intercept sensitive data, including login credentials, credit card details, and confidential communications shared between parties. Such information may fuel identity theft, financial scams, and malicious exploits.
Monetary Losses: Attackers with access to financial information could manipulate payments or redirect funds, inflicting financial losses on you and your organization. Unauthorized entry into online banking could result in account drainage and illicit transactions.
Intellectual Property Theft: Businesses face the danger of intellectual property, trade secrets, or confidential data being stolen through MitM attacks. Competitors or cybercriminals could exploit stolen data to their advantage.
Legal and Regulatory Consequences: Data breaches due to MitM attacks could render you or your organization liable to legal action and regulatory penalties, especially if customer data is compromised.
Conclusion
It’s reasonable to assume that MitM attacks are going to increase. Recognizing the need to safeguard oneself online is essential. Detection entails vigilant account monitoring, security software deployment, and vigilance towards frequent irregularities. Prevention hinges on secure connections, cautiousness with emails and links, evasion of public Wi-Fi risks, MFA implementation, and continuous self-education.
The consequences of MitM attacks are significant, spanning from data theft to financial setbacks. With this knowledge, you can strengthen your digital security, prioritize cybersecurity, and stay safe online.
About the Author: Chinemerem Nwosu is a self-taught cybersecurity content writer based in Nigeria. With a passion for technology and a keen interest in cybersecurity, Chinemerem has honed his writing skills through extensive research and practical experience.
In addition to writing, Chinemerem enjoys staying up-to-date with the latest trends and developments in cyber security and sharing his knowledge with others. Chinemerem is committed to providing clear, concise, and informative content that helps readers stay safe online. When not writing about cyber security, Chinemerem can be found exploring the great outdoors or spending time with his family. @thecybergeneral
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor and do not necessarily reflect those of Tripwire.

