
Have you ever had to set up your Gmail account on a secondary device, such as your tablet, and when you tried to login, verification prompts were sent to your original device to confirm that the login attempt was done by you? You confirmed the login, and that ended it.
That is exactly what happened to an Uber employee whose account was compromised. However, the Uber employee was not setting up another device; a malicious actor was setting up another device using the Uber employee's compromised credentials. Unfortunately, that simple act was the catalyst for the recent Uber attack which led to what eventually may be the loss of millions in revenue, and the erosion of client trust.
So how exactly was the threat actor able to accomplish that? The answer is Multi Factor Authentication (MFA) prompt bombing.
What is MFA Prompt bombing?
MFA Prompt bombing is a social engineering attack vector that uses the “something you have” method of authentication (your mobile device) to play on a person’s security apathy to gain access to a network. Access is usually unwittingly granted by the target.
The traditional method of authentication is no longer effective. These days, there are tons of personal information online. Dates of birth, names of relatives, high school names; basically everything an average person may draw from to form a password. Add the availability of stolen credentials on the dark web, and password protection starts to look like a puppy in a thunderstorm.
MFA saves the day, adding one or more extra layers of security to an account to ensure that even when credentials have been compromised, only a verified user can gain access. One of the ways this is established is by sending a prompt to the user's device – the device with which the account was created – in order to verify login attempts on any other device. Threat actors take advantage of this prompt-based authentication.
How does MFA Prompt bombing work?
One need not be an elite criminal to carry out an MFA prompt bombing attack. Like most social engineering scams, most of its success relies on opportunistic timing; catching the target at the most vulnerable moment. Usually at night, when the user is tired and less alert, and with the help of a script that continually attempts to log into an account when run, threat actors are able to prompt the user's device continually, until, in frustration, the victim verifies the prompt.
Here's an example using Google's 2 factor authentication (2FA):
After obtaining a person’s credentials from the dark web, the attacker sets up an email account using that person’s information. This will trigger the 2FA notification to the victim’s device.
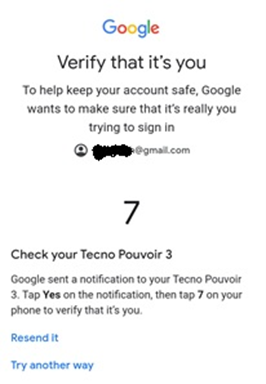
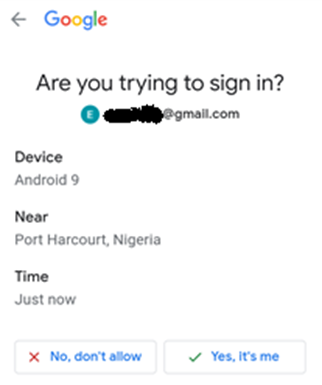
Of course, if a person is paying attention, they will notice that the location of the login is illegitimate, and they will deny the login request. However, this is why the timing of social engineering is so important. If sent at a time when the victim is unlikely to pay close attention, they may not notice the location on the prompt.
Some threat actors will go as far as to contact the account owner under the guise of an IT support staff technician to encourage them to verify the prompt.
Once the user verifies the prompt, the threat actor goes ahead to register his own device as a trusted device, which can now have access to the account at will. He may create new accounts upon access, ensuring that several backdoors are available for entry and exit of the network at will.
How you can guard against MFA Prompt bombing
Guarding against MFA prompt bombing requires a proactive approach. Doing away with the factors that encourage it – before the actual attack – goes a long way toward reducing the likelihood of an attack.
The factors that contribute to the success of prompt bombing include:
Lack of information
A tired man will do anything to get a few hours of rest. Threat actors know this, so they initiate the prompts at the most inconvenient times. Usually at night after a long day at work.
However, verifying a login that was not attempted by an employee is indicative of two things:
- Neglectfulness of the meaning of good security.
- An apathetic attitude towards security.
Organizations should take no chances with this. Investing in educating employees about MFA, how it works, and what to do in the event of an attempted login by third parties, will go a long way toward reducing the risks involved in using older and riskier types of MFA.
The method of authentication
When “something you have” is your device, then prompt bombing becomes inevitable. Though threat actors can gain access to an account by exploiting other methods of authentication, prompt bombing relies solely on prompt-based authentication.
It is advisable to steer clear of prompt-based authentication when making use of the “something you have” method of authentication, especially those that allow an unlimited number of prompts. Investing in phishing-resistant MFA is usually the best way to go for organizations. Using security keys and tokens is generally considered more phishing-resistant than using device-based authentication.
What is a Phishing-resistant MFA?
Any MFA that uses the FIDO2/WebAuthn method is usually considered Phishing-resistant. While this method is not yet available for personal Gmail accounts, it is easily deployed in corporate environments. It is only a matter of time before FIDO2 is available as part of all publicly available email clients.
How to Resist that Phish
Social engineering, especially phishing, remains the predominant attack vector employed by threat actors to gain a foothold inside organizations' networks. MFA prompt bombing has proven particularly effective for such attacks, as was seen in the Uber attack.
To combat this, organizations must not only invest in educating employees about such threats and how to avoid them; they must also prioritize investing in phishing resistant MFAs.
About the author:

Ezifeh Chinua is a B2B Tech writer in the Cybersecurity and SaaS niches. He has written for publications like Hackernoon and Future Syllabus amongst others. He's currently acquiring his CISSP certification.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

