
The Medusa ransomware gang continues to present a major threat to the critical infrastructure sector, according to a newly-released joint advisory from the FBI, Cybersecurity and Infrastructure Security Agency (CISA) and the Multi-State Information Sharing and Analysis Center (MS-ISAC).
As of February 2025, the Medusa ransomware operation, which we have previously detailed on the Tripwire State of Security blog, had hit over 300 organisations from a variety of critical infrastructure sectors with affected industries including education, health, legal, insurance, technology, and manufacturing.
Once hit by a Medusa ransomware attack, victims are told that they must pay a ransom to decrypt their files and to prevent them from being released onto the internet. This is known as a "double-extortion" attack - and means that even if the victim organisation has backups and can recover the files that have been encrypted, they still face the threat of having their sensitive data leaked if they refuse to pay the ransom.
If the victim refuses to pay, the stolen data may be leaked on Medusa's dark web forum or sold to others, potentially causing reputational damage, legal consequences, and financial losses.
However, in the advisory the FBI notes that at least one victim of a Medusa ransomware attack found itself contacted by a separate Medusa ransomware affiliate who claimed that a negotiator had stolen a ransom which had already been paid, and requested half of the payment be made again in order to receive the "true decryptor."
The advisory notes that this potentially indicates a "triple extortion" scheme.
In the joint cybersecurity advisory, organisations are advised to take action today to mitigate against the Medusa ransomware threat.
That advice includes:
- Mitigating known vulnerabilities by ensuring operating systems, software, and firmware are patched and up to date within a risk-informed span of time.
- Segmenting networks to restrict lateral movement from initial infected devices and other devices in the same organisation.
- Filtering network traffic by preventing unknown or untrusted origins from accessing remote services on internal systems.
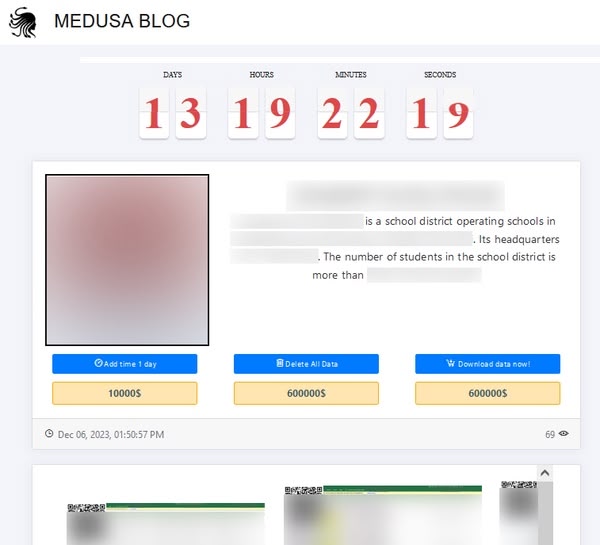
Past victims of the Medusa ransomware have included Minneapolis Public Schools (MPS) district, which refused to pay a million-dollar ransom and saw approximately 92 GB of its stolen data released to the public.
Other Medusa ransomware victims have included cancer centres, and British high schools.
The Medusa ransomware group has also boasted about stealing Microsoft source code.
Editor’s Note: The opinions expressed in this and other guest author articles are solely those of the contributor and do not necessarily reflect those of Tripwire.
