
The supply chain is a complex environment that goes deep inside a business and involves the majority of its infrastructure, operations, personnel, and outer relations: vendors, partners, and customers. To protect that matrix is extremely difficult, as there are numerous sensitive nodes, lines, and processes that a security team has to take care of: software and hardware resources, cloud, hybrid and local environments, platforms, and web apps.
The complexity of the supply chains is also their weakness and the reason why they are so attractive to cybercriminals. We have already experienced supply chain attacks in the recent past and statistics show that most likely are going to witness an upward trend in the future. This blog focuses on the software supply chain attacks and what best practices security teams need to employ, in order to protect them and keep their security posture clean.
Supply chain attack fundamentals
The supply chain attack focuses on two or more targets, the intermediary ones and the final. After successful network infiltration of an intermediary target, like a small vendor, cyber criminals employ malicious code to compromise vendors’ software and use them as a gateway for their final target: the software of high-value suppliers, customers, and enterprises.
Unlike physical systems, the software is constantly revised through updates and patches after leaving its manufacturer and is prone to numerous unintentional and malevolent flaws. As the supply chain fits within the greater information and communications technology (ICT) supply chain framework, it is crucial for security teams to realise that cybercriminals can lurk and attack every phase of the ICT Supply Chain Lifecycle.
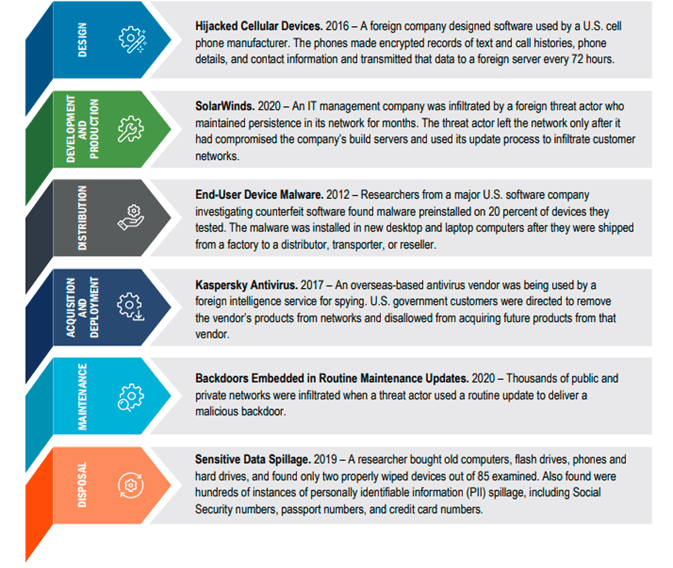
Figure 1. ICT Supply Chain Lifecycle and Examples of Threats (www.cisa.gov)
The supply chain attack walkthrough has three major stages. Firstly, the attacker finds and infects his intermediary target. Secondly, the malware spreads and the cybercriminal waits for the results of his efforts. The last stage is the actual attack, where the final target has been attacked and usually negotiations for ransoms begin. The time distance between infection and attack makes supply chain attacks popular amongst threat actors, as it helps them remain undetected for a long time.
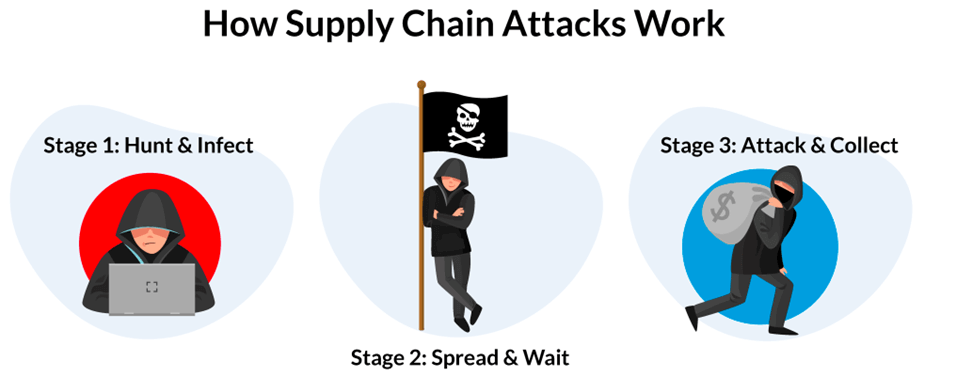
Figure 2. The three stages of a supply chain attack (www.xorlab.com)
The techniques
The majority of supply chain attacks follow patterns that fall into one of the following techniques, which can be executed simultaneously:
- Hijacking updates
- Undermining code signing
- Compromising open-source code
- App Store Attacks
Hijacking updates
Nowadays, modern software receives updates as a distribution process, part of product maintenance from centralised servers to customers, to address security issues. Capable and highly skilled threat actors hijack updates by entering the business’ network and inserting malicious code into the update, to gain software’s functionality control. The infected updates are further spread along hardware and networks.
These sophisticated attacks usually encrypt data, target physical systems, or extract sensitive information. Examples of hijacking updates technique proved extremely disastrous causing big global disruptions in critical industries.
Undermining Code signing
Code signing relies on public key cryptography; a digital signature that validates the integrity of the code and that of the code’s author. Cybercriminals undermine that process by self-signing certificates, breaking signing systems, or exploiting misconfigured and poorly protected account access controls.
Doing so enables them to exploit software updates by impersonating a trustworthy third party and injecting malware into an update. Then the road for them to perform a bouquet of illegal and lawless actions – from altering open source code to espionage campaigns – is wide open.
Compromising Open-Source Code
That simple-to-employ technique occurs when threat actors insert malware into open-source code that is further added by developers into their own third-party code. In many cases, attackers either modify packages by gaining account access or post their packages with names close to regularly used ones. The malicious code usually tries to access targets’ data and payment information.
An example of this technique involved malicious Python libraries that contained the same code and functionality as those they impersonated, but also additional functionality that enabled them to obtain boot persistence and open a reverse shell on remote workstations.
App Store Attacks
These attacks use web app distributors to infect mobile devices, by compromising legitimate apps or by designing malicious apps. Usually, when installed and executed these apps are trying to access and extract payment and other sensitive information, which is sent back to their originators.
The need to secure the shiny supply chains
Mike Sentonas highlights: “Frankly put, supply chains are vulnerable, and adversaries are actively researching ways to take advantage of this. We haven’t nearly seen the end of these attacks, and the implications for each one are significant for both the victims and the victims’ customers and partners up and down the chain.”
Software supply chain attacks are and will remain a popular and attractive target for cybercriminals. The key attraction is the one-to-many relationship between the chain links: infect one and you get all for free! That’s why in 2021 we have witnessed a 650% increase in supply chain attacks’ frequency and sophistication, which is expected to continue over the next coming years.
Cybercriminals take advantage of these attacks to execute large-scale extortion or gain extensive access to espionage-linked targets. They take benefit of inherent organizational seams and misuse relationships where users anticipate finding reliable code.
These attacks can also have a significant impact and significantly increase the value of a breach, as they can affect widely used open-source projects. Second, they have the potential to penetrate deep into an organization, weakening development and administration tools, and finally its cohesion. Last but not least, supply chain attacks can have strategic value for state actors and have been utilized effectively.
As the trend of supply chain attacks moves upward and paralyses critical infrastructures, policymakers, decision-makers, and cybersecurity professionals shall motivate them and take immediate actions to increase the cost and lower the impact of supply chain attacks. The President of the US Joe Biden has already signed an Executive Order to align initiatives of the public and private sectors and minimize threats to national security by reforming and modernizing cybersecurity in the United States.
Take care of the supply chains
To address the insecurity of the supply chain three top-level recommendations are suggested at the strategic level:
- Improve the baseline: communicate the best supply chain security tools to all as best practices don’t work well in isolation, align them with widely supported standards, and share relevant knowledge.
- Better protect open source: As open source exists everywhere, the community must properly secure open source projects.
- Counter systematic threats: As strength lies in unity, everybody must work collaboratively and support joint attribution more effectively to protect against the common threat.
- Create a Software Bill Of Materials (SBOM).
At the operational level, businesses can equip their security toolbox with several activities to improve security posture. Indicative but not limiting these can be:
- Activate decoys (honeytokens) to get an early threat warning.
- Secure Privileged Access Management (PAM) to protect sensitive resources; minimize access to sensitive data; protect vulnerable resources; implement the Principle of Least Privilege (PoLP).
- Assume you will experience a data breach, and Implement a Zero Trust Architecture.
- Identify potential insider threats, and try to reduce them by continuous awareness training.
- Implement strict Shadow IT rules; register all IT devices alongside strict guidelines.
- Perform regular third-party and business risk assessments.
- Monitor and review vendors’ networks for vulnerabilities and data leaks.
Keep supply chains well lubricated
Supply chain attacks, if succeeded, are extremely effective and devastating since they spread widely and affect well-secured systems. To improve their security, policymakers of the public and private sectors shall encourage the allocation of fresh funds and support to open source initiatives, while cybersecurity professionals shall refocus on implementing security best practices, revising security policies, and sharing incidents’ knowledge.

About the Author:
Christos Flessas is a Communications and Information Systems Engineer with more than 30 years of experience as an Officer of the Hellenic Air Force (HAF). He is an accredited NATO tactical evaluator in the Communication and Information Systems (CIS) area and the National Representative (NatRep) at Signal Intelligence CIS and at Navigation Warfare (NavWar) Wrking Groups. Christos holds an MSc in Guided Weapon Systems from Cranfield University, UK. He has also attended numerous online courses such as the Palo Alto Networks Academy Cybersecurity Foundation course. His experience covers a wide range of assignments including radar maintenance engineer, software developer for airborne radars, IT systems manager and Project Manager implementing major armament contracts.
Christos is intrigued by new challenges, open minded, and excited for exploring the impact of cybersecurity on industrial, critical infrastructure, telecommunications, financial, aviation, and maritime sectors.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
Zero Trust and the Seven Tenets
Understand the principles of Zero Trust in cybersecurity with Tripwire's detailed guide. Ideal for both newcomers and seasoned professionals, this resource provides a practical pathway to implementing Zero Trust, enhancing your organization's security posture in the ever-evolving digital landscape.

