
Whilst working for a management consultancy, I learned a lot more about industrial control systems (ICS) than I ever imagined I would. In many cases, this wasn’t from working on them directly; it was from simply speaking to the technicians and reading documentation. Oftentimes, we have the false belief that our systems are safe from compromise because no one really knows how they work. It’s like security through obscurity. However, what I have also learned over time is that humans are the architects of these solutions. Whilst they may vary slightly, these solutions are not so innovative that one can’t uncover their nuances in a bit of time. Therefore, relying on obscurity to keep things safe is one of the poorest excuses to not take action.
Common Threat Types to Consider
As noted in the Verizon 2019 Data Breach Investigations Report (DBIR 2019), a majority of attacks against ICS involve phishing and the use of stolen credentials. Over in IT, we recognize this as having almost always been an issue, one that continues to get worse as phishing increases in sophistication. Further still, as the report states, 68% of incidents and breaches were financially motivated - which is the number one motivation for all malicious attacks across any industry. Due to this, it’s not hard to understand why malicious actors were able to create custom malware to target systems, as see in the Ukraine power grid hack of 2015. One way to describe a breach as someone sticking their hand into a box, not being able to see directly, but feeling their way around in it to find the best prizes. Essentially, even in a targeted attack, unless you have insider information and know exactly what to look for, usually you’re on the system attempting to map it out, understand where things are, and realize the highest return or the best ‘prize;’ also known as ‘dwell time.’ When IT and OT (operational technology) are combined but the security program isn’t mature, it’s nigh on impossible to detect a malicious actor on your system, especially if the malicious actor is quietly gathering data for later. Potentially, when many systems, processes, and data are interrupted, you may detect that a required service didn’t come back online; if the malicious actor is careful, they should be able to go undetected for some time. During that time, they can create, distribute, and eventually activate malicious code. Another possibility is they just spend their time gathering confidential data. It’s thus no wonder that espionage registered as the second highest rated motivation in the DBIR 2019 at 27%. https://twitter.com/rosesecops/status/1201875630599614464
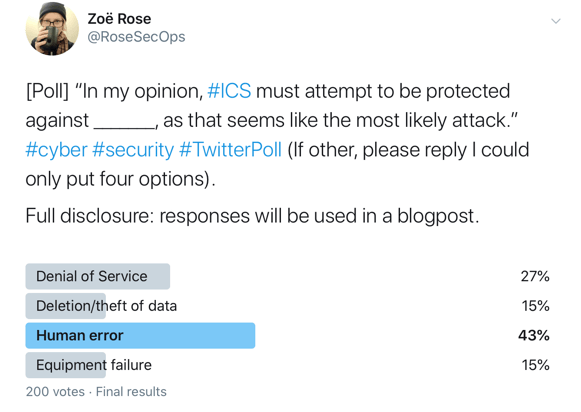
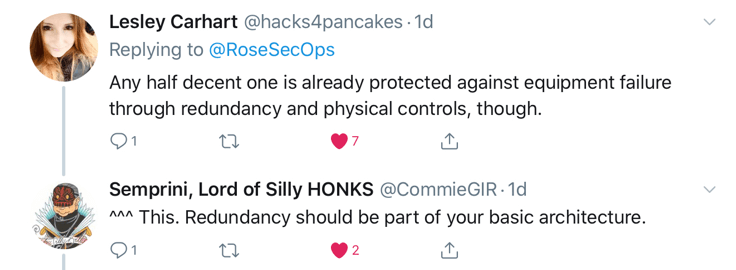
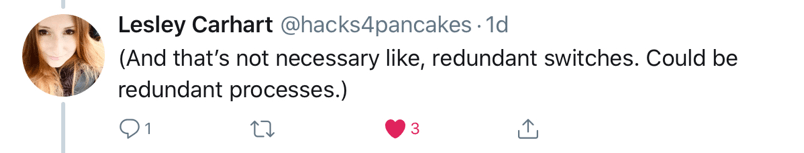
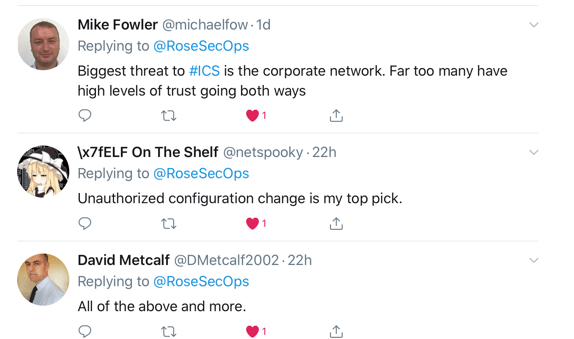
As any proper security program goes, understanding the likely attacks is vital to building effective protections against. Organizations with ICS should be wary of the common types of cyber attacks such as destruction, manipulation, loss of integrity, or theft of data. Furthermore, denial of service is not only common but also there’s so many forms that it’s impossible for me to label them all. You may be familiar with DDoS, or distributed denial of service, such as in 2018 when Github was hit with “...incoming traffic at a rate of 1.3 terabytes per second (Tbps), sending packets at a rate of 126.9 million per second.” However, let’s be honest, it doesn’t have to be distributed. Systems that are purpose built, ca be taken offline from updates, too much network traffic, and more.
Staying Protected from ICS Security Threats
In protecting against these threats, it’s useful to keep in mind the following three examples of separation:
- Limiting access to these systems: Whilst it seems like common sense, it takes more than a bit of thought when connecting a network. Consider the number of flat networks you come across in your day. A flat network is something you can think of as one pool where all connected devices are within one broadcast domain. Simply put, they can all speak together. In a properly configured and layered environment, there should be logical separation along with physical divides.
- Following the principle of least privilege: This way, we can reduce the likelihood of human error when someone needs access but shouldn’t be making massive changes.
- Defence in depth and setting a baseline: As mentioned above, adding logical and physical layers to your network is going to go a long way to keeping things quiet for fragile systems. When a malicious actor gains access to a network, if we have multiple virtual LANs that they are unable to traverse across, (Or if they do find a way, it sets off alarms due to anomalous activities.) that’s still a success. Being able to limit but also quickly detect what is going is a help to any environment.
We must realize that whilst many threats to ICS Security are similar to multiple other industries, it’s what’s at stake that makes the difference. This is why we have financially motivated and organized crime, even nation state actors targeting these systems with custom malware. In order to protect against these threats, we must bridge the IT and OT divide. Organizations and teams need to understand and effectively address the different roles and responsibilities of IT and OT. Who’s responsible for the variety of security challenges? The final piece to the puzzle is to invest time and resources in building a robust culture of security, to identify, detect, respond, to and protect against incidents in the event of control failures. Interested in reading more about ICS and cybersecurity? Check out the latest Tripwire ebook Navigating Industrial Cybersecurity A Field Guide here: https://www.tripwire.com/solutions/industrial-control-systems/guide-to-industrial-cybersecurity/
Further Reading:
Navigating Industrial Cybersecurity: Knowing the Basics Navigating ICS Security: The Value of Frameworks Navigating ICS Security: Best Practices for ICS Decision-Makers Navigating ICS Security: Having your Action Plan Ready
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.

