
Verizon Enterprise has once again released its annual Data Breach Investigations Report (DBIR). The publication doesn’t disappoint in providing crucial insight into today’s digital threats. On the one hand, Verizon’s 2019 report captures how many forces in the threat landscape have remained the same since its previous report. The study observed how sending data to incorrect recipients is still an issue for many organizations, for instance, and how financial gain remains the most common motive for data breaches. On the other hand, the analysis reveals how the digital threat landscape is always changing. This year’s report embodies such dynamism by adding a new subset of data related to financial attacks as well as by uncovering a reduction in card-present breaches involving point-of-sale (POS) environments and card skimming operations. We’ll examine those developments below.
Introducing FMSE
For the 2019 DBIR, Verizon Enterprise’s researchers analyzed 41,686 security incidents, 2,013 of which were confirmed data breaches. This examination uncovered 370 financially motivated incidents that in 248 cases produced either a data breach or fraudulent action. Primarily featuring web application attacks, these events featured social actions, including financially motivated phishing and pretexting, but they did not include the installation of malware or employee misuse. To properly account for these attacks, Verizon Enterprise created a new subset of data called financially-motivated social engineering (FMSE). These operations, which are also included in the report’s main corpus, focused primarily on credential theft and tricking people into transferring money into fraudulent accounts. Such FMSE incidents affected all industries, but they disproportionately targeted Professional Services, Healthcare and Finance organizations.
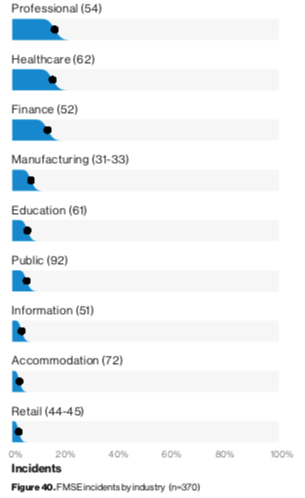
Verizon's 2019 DBIR, page 32.
The Decline of Card-Present Breaches
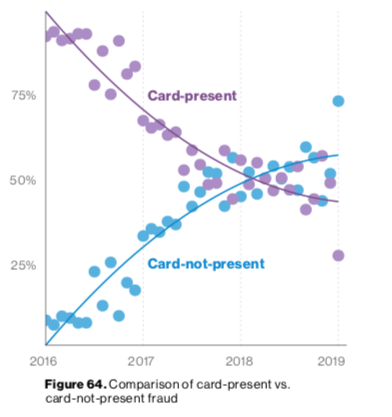
One of the most significant changes which Verizon Enterprise uncovered in its 2019 DBIR was the reduction of card-present breaches involving POS environments and card-skimming operations. Digital criminals instead shifted their efforts to target payment cards by compromising e-commerce applications. Indeed, most data breaches involving exposed payment cards involved web servers in some way. This trend was evident in a few of the industries analyzed by Verizon. Let’s examine two in particular: Accommodation and Food Services as well as Retail.
Accommodation and Food Services
The Accommodation and Food Services sector disclosed 87 incidents, 67 of which were confirmed data breaches, during Verizon Enterprise’s reporting window. Forty of those attacks targeted POS environments. That’s nearly half of the report’s total number of incidents for this industry but still significantly fewer than the 307 POS events analyzed in the 2018 DBIR. Verizon Enterprise doesn’t believe this is necessarily a shift in focus. Instead, it believes it could simply reflect how digital criminals didn’t go on an attack spree against POS environments in the past year. As it explains in this year’s report:
POS breaches are often conducted by organized criminal groups looking to breach numerous targets and there have been sprees of hundreds of victims associated with the same hacking group. Back in 2011, default credentials were used with great success evidenced by over 400 breaches, and recent sprees have been associated with POS vendors suffering breaches leading to subsequent breaches of their customer base.
The enterprise technology solutions provider also disclosed how news of a publicly disclosed POS vendor breach affecting multiple food service victims emerged after its 2019 report window closed. This reveals how POS attacks still are a threatening force confronting organizations.
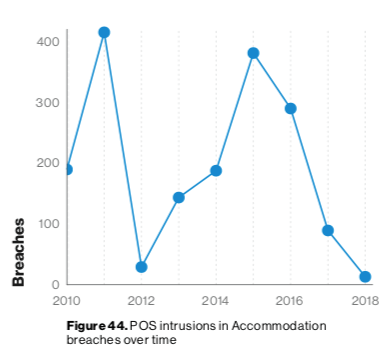
Verizon's 2019 DBIR, page 36.
Retail
Something similar happened in retail, a sector which reported 234 incidents (of which there were 139 data breaches). Indeed, web application attacks largely replaced POS intrusions, thereby reflecting the decline of POS-related breaches and payment card skimming. It’s unclear why these types of breaches have declined, but perhaps the widespread adoption of EMV helped diminish the value proposition of card-present fraud for bad actors. In response, digital attackers focused their efforts on compromising retail organizations’ web applications and installing code designed to capture their customers’ payment card data.
Verizon's 2019 DBIR, page 59.
The Breach Timeline at a Glance
Despite the new developments discussed above, Verizon’s 2019 DBIR confirmed the persistence of one disheartening trend: the time to compromise continues to dwarf the time to discover. Specifically, while digital attackers typically spend mere minutes from when they initiate their first action to the time that they compromise an asset, it can take organizations months to discover said compromise depending on the nature of the attack. Mitchell Jukanovich, vice president of federal at Tripwire, feels that organizations need to acknowledge this reality by focusing on their users:
The key to mitigating aggressive social engineering campaigns as well as malware attacks happens at the human level -- cyber training and education. It sounds elementary, but a sound cyber training and education program can reduce the risk exposure to an agency, department or branch service. This year’s DBIR reinforces the need for agencies to have a cyber response plan and to practice executing against it.
Organizations should also take their defensive measures even further with a two-pronged approach recommended by Verizon Enterprise in its 2019 DBIR. First, they need to discover what data types they possess. Second, they should use that knowledge to apply correct security controls such as vulnerability management and file integrity monitoring. For more information about how organizations can effectively defend against data breaches, download a copy of Verizon’s 2019 DBIR here.

