
As we begin our new decade of the 2020s, we can look back at the last 30 odd years and examine the collaboration between technology and our daily lives. If you think of your day-to-day, it’s easy to see how much our society relies on technology. Consider our smart devices such as mobile phones, watches, even homes. However, what about the technology that we don’t see, that gives us clean drinking water, removes wastewater, and keeps our homes warm? Industrial Control Systems (ICS) are often considered a part of the Critical National Infrastructure (CNI). CNI is generally classified as assets needed to keep our society and economy running as we expect, our normal.
How Well Are ICSs Protected Regarding Cyber Security?
It depends on what side of the security triad you’re looking at. Is operational technology (or OT) highly available? Yes, traditionally OT was designed, purpose built even in some situations, to remain online at all costs. Confidentiality or Integrity on the other hand, these weren’t a massive part of the conception. However, in fairness, the assets on an OT network aren’t like what we have over on the IT side of things. Considering OT and IT work separately, you might think there’s little overlap in the real world, if so you would be wrong. Over the last thirty years there has been a consistent trend to connect these two worlds. You may have heard of the Purdue Model developed in 1990, which was created in an attempt to classify the different domains of management for physical processes. Businesses are formed around risks, budget, and the responsibilities of teams. Often times risks when it comes to cybersecurity aren’t well understood, and therefore the budget doesn’t effectively reflect this. There are the known challenges of defining clear roles and responsibilities when it comes to IT. Then add to this OT, which is still beginning to be classified effectively. We often end up with issues in who’s responsible for the cybersecurity side of things.
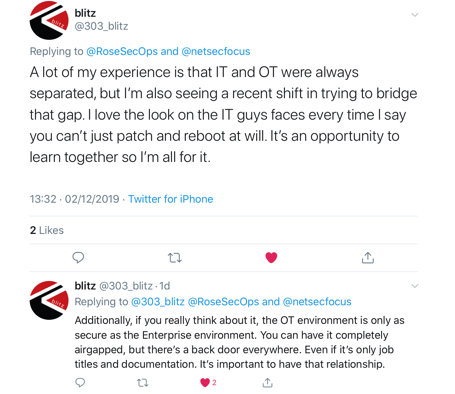
Who’s Responsible for These Security Challenges?
https://twitter.com/rosesecops/status/1201488990295248896 Over time in ICS security, we have seen a convergence between the IT and OT environments, due in part to convenience, other times cost or function, and more. However, when dealing with IT in our lives, we usually are referring to usability - smart devices providing directions for example. If they fail, we can still go back to maps. Consider when WannaCry brought the NHS almost completely offline. Whilst massively impactful, doctors and nurses still could refer to paper charts. Whereas, when our critical infrastructure goes down, such as when Ukraine power grid hack of 2015, citizens were without power to their homes in winter for 1 to 6 hours. Candles may have been used for light, but you can’t use pen and paper for clean drinking water, removal of wastewater, and never mind heat in the middle of winter. If we know our infrastructure is critical, not just business critical but society critical, who should we be bringing into the room when discussing these issues? According to Dave, it’s the DOO’s job to make the decision, but they also require access to persons able to clarify these risks. https://twitter.com/rosesecops/status/1201491473360936962 I do agree with this, but who are these people? Consider the SOC analyst who works day to day on diagnosing alerts, the technical lead who chooses what solutions to go with and why, and the manager who might not be as hands on anymore but knows the business well. All of these people (or someone from their teams) are valuable in these discussions. Whoever’s responsible for the system’s maintenance and availability will be vital to any security solutions layered on. Realize that when it comes to the collaboration of systems, it requires effective communication and collaboration of persons as well. https://twitter.com/qawedge/status/1201587714522525696 According to @QaWedge, ICS security ultimately falls to a mix of CISO, VP IT, TeamLeads and sec team. On principle, I agree with this, as well, but it’s worth being careful with this mixture of persons to make sure not only is everyone understood but also that in the end a decision is made.
Putting Industrial Control System Security into Perspective
Both of the incidents above refer to malicious actors targeting systems. For Ukraine’s power grid, it was specifically used to take them down. Where does this leave us for our increasing connection between technologies? Again, OT wasn’t designed for this; it’s often purpose built to ensure high availability, to continuously run and to provide a service. Restricting access isn’t exactly embedded into this and limiting functionality would have seemed foolish to implement. IT on the other hand, which should have gotten this right, still struggles with the foundations of security - so where does this leave us for connections between, a lot more lost in the roles and responsibilities of security against the technology. Want to understand more about Industrial Control Systems? Check out Tripwire’s ebook that covers foundations up to building an action plan: https://www.tripwire.com/solutions/industrial-control-systems/guide-to-industrial-cybersecurity/.
Further reading in this series: Navigating ICS Security: The Threat Landscape Navigating ICS Security: The Value of Frameworks Navigating ICS Security: Best Practices for ICS Decision-Makers Navigating ICS Security: Having your Action Plan Ready
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.

