
Healthcare organisations in the United States are being warned to be on their guard once again, this time against a family of ransomware known as Venus.
An advisory from the United States Department of Health and Human Services (HHS) has warned that the cybercriminals behind the Venus ransomware have targeted at least one healthcare entity in the United States, and are known to be targeting publicly-exposed Remote Desktop Servers.
The Venus ransomware (also known as GoodGame),which is known to have been successfully attacking organisations since the middle of August 2022, encrypts data files, and changes their filenames so they are appended with a .venus extension, while deleting event logs and shadow copy volumes.
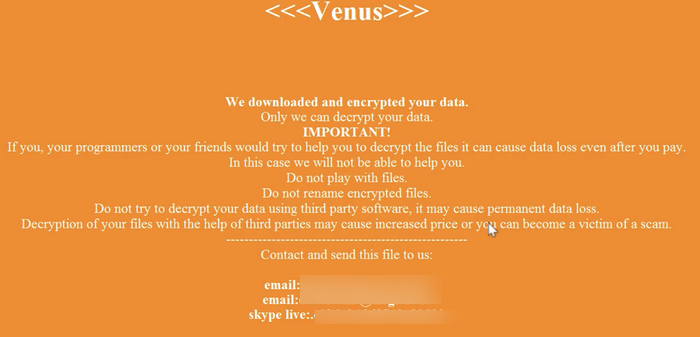
Furthermore, Venus disables Data Execution Prevention on compromised computers.
The Venus ransomware attempts to terminate 39 processes associated with database servers and Microsoft office applications:
- taskkill
- msftesql.exe
- sqlagent.exe
- sqlbrowser.exe
- sqlservr.exe
- sqlwriter.exe
- oracle.exe
- ocssd.exe
- dbsnmp.exe
- synctime.exe
- mydesktopqos.exe
- agntsvc.exe
- isqlplussvc.exe
- xfssvccon.exe
- mydesktopservice.exe
- ocautoupds.exe
- agntsvc.exe
- agntsvc.exe
- agntsvc.exe
- encsvc.exe
- firefoxconfig.exe
- tbirdconfig.exe
- ocomm.exe
- mysqld.exe
- mysqld-nt.exe
- mysqld-opt.exe
- dbeng50.exe
- sqbcoreservice.exe
- excel.exe
- infopath.exe
- msaccess.exe
- mspub.exe
- onenote.exe
- outlook.exe
- powerpnt.exe
- sqlservr.exe
- thebat64.exe
- thunderbird.exe
- winword.exe
- wordpad.exe
Initial ransom payments demanded in Venus ransomware attacks appear to currently start around 1 BTC (at initial ransom demands may start around 1 BTC (which presently is worth less than US $17,000.)
In a change from today's norm when it comes to ransomware attacks, Venus does not appear currently to run a data leak site on the dark web. It also does not appear to operate as a ransomware-as-a-service (RAAS) operation - although, of course, this could change in the future.
However, the HHS advisory says that it believes multiple threat actors are distributing the Venus ransomware, and that in-the-wild samples have been observed contacting IP addresses in various countries around the world including the United States, the United Kingdom, Denmark, France, Ireland, Japan, the Netherlands, and Russia.
The HHS's advice for health organisations (and indeed other potential victims of the Venus ransomware) is to put vulnerable publicly-exposed Remote Desktop services behind a firewall.
It makes sense for all organisations to read our tips on avoiding ransomware attacks, including:
- making secure offsite backups.
- running up-to-date security solutions and ensuring that your computers are protected with the latest security patches against vulnerabilities.
- using hard-to-crack unique passwords to protect sensitive data and accounts, as well as enabling multi-factor authentication.
- encrypting sensitive data wherever possible.
- educating and informing staff about the risks and methods used by cybercriminals to launch attacks and steal data.
More information about the Venus ransomware threat can be found in the advisory published by the HHS.
The warning about Venus comes less than one month after the FBI, CISA and HSS issued a warning about the Daixin Team ransomware group encrypting healthcare servers and exfiltrating sensitive health information.
Editor’s Note: The opinions expressed in this and other guest author articles are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

