
A new phishing campaign is targeting LinkedIn users, leveraging hacked accounts to send malicious links via the platform’s private messaging feature. According to security researchers at Malwarebytes, the campaign abuses Premium membership accounts, which can message other LinkedIn users – regardless of whether they’re connected or not. “The fraudulent message includes a reference to a shared document and a link that redirects to a phishing site for Gmail and other email providers that require potential victims to log in,” explained Jérôme Segura, lead malware intelligence analyst at Malwarebytes, in a blog post. Users who fall for the bait ultimately hand over their username, password and phone number to malicious actors. In the attack, the perpetrators abuse URL shorteners (ow.ly) and a free hosting provider (gdk.mx) to redirect unsuspecting victims to the phishing page, which is hosted on a hacked website. The phishing page is designed to look like a Gmail login page, but will also ask for Yahoo or AOL usernames and passwords. When users attempt to log in to access the attachment, the page requests to verify their identity by providing a phone number. Researchers have observed the phishing links being sent via instant message, in addition to LinkedIn’s InMail, which includes a "security footer."
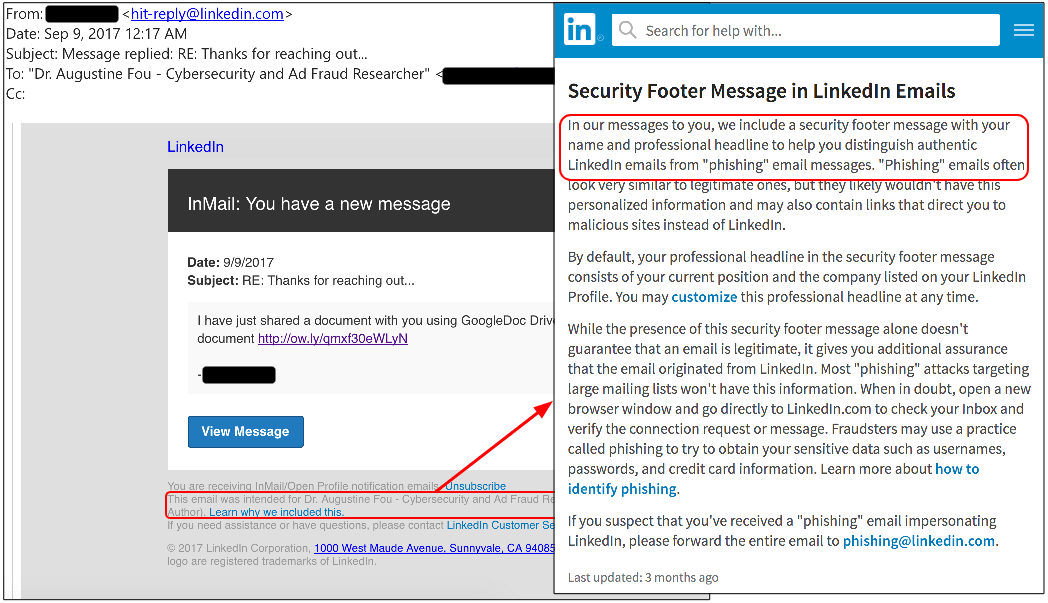
Source: Malwarebytes “This kind of attack via social media is not new – we have seen hacked Skype or Facebook accounts send spam – but it reminds us of how much more difficult it is to block malicious activity when it comes from longstanding and trusted user accounts, not to mention work acquaintances or relatives,” added Segura. Users who suspect their LinkedIn account may have been compromised are advised to immediately review their account settings, change their password and enable two-step verification.

