
Having worked with many individuals responding to incidents where their digital private images were shared without consent, social media or email accounts had unauthorised access, and even physical safety was a concern, it is all too familiar how terrifying the unknown can be. As someone who has been on both the victim's and later the responder’s side, I am qualified to express both the terror and knowledge of things you can do to take back control. In 2017, I had the pleasure to speak with the Pint of Science group at a music festival on personal security, one of my more unique conference stages. It was brilliant fun, but it also led to many personal digital security discussions from the audience.

If you’re a technical person, remembering each and every piece of your online footprint can be an inconvenience. Mistakes happen, and information you might not have wanted revealed can accidentally be shown. In episode 141 of IntelTechniques podcast, guest Jack Rhysider, host of Darknet Diaries, talks about how even he was taken by surprise from this. Listen to the episode for exact details. (This part begins at around 14:40.) Essentially, a fan was able to locate where Jack lived, and they worked through clues within the posted video and used this to contact him at work. For non-technical persons, simply understanding the footprint we leave online, on our devices, and even in our daily interactions in life can be a nightmare. I spoke with one person who had their Facebook account taken over and funds stolen by a known terrorist group. All of this linked back to an email compromise. During an investigation with ITV’s The Kyle Files, I found another person who posted an image of their child and his sports certificate. Unfortunately, the information found on the said certificate provided all information needed to identify the child’s routine, family and location. One might intend a post to express pride for a notable achievement, but in an attacker’s hands, it could be used maliciously. Whilst our intentions are often positive, unfortunately, others aren’t always that. Understanding this distinction is the first challenge of recognizing the need for digital security.
Making a Conscious Decision Before Sharing Information
https://twitter.com/gabsmashh/status/1155289146505793536 Many sites use personal information as a form of digital authentication during a password reset, verification during a phone call, and/or the basis for answering security questions. When you share information online, consider what you’ve shared. Can it be used to access any of your accounts?
- Take a moment to think who the audience is of this shared information?
- How sensitive is this information?
- Are you concerned about specific persons, groups, and/or the public finding out this information?
- Can this information be used to access any of your accounts?
When information, images, videos, and more are shared digitally, no matter the initial audience it was shared with, it can be nigh on impossible to take it offline again. Additionally, even well-intentioned connections can accidentally share sensitive information to audiences that are broader in scope than what you might have expected. It is always a great idea to be prepared, in case the friends-only status update you posted becomes public knowledge. I can’t remember exactly who said it to me originally, but another way to think of it is “Imagine what you post becomes front page news in tomorrow’s Daily Mail.”
Be Mindful of the Data Aggregation
https://twitter.com/geminiimatt/status/1224047851698827265 No matter where you are on the technical scale, you have likely become aware of tailored ads on your social media platforms, search engines, and sites. This can be annoying to see ads, frustrating when it stops you from getting the cheapest flights, and even embarrassing. There are resources that can assist with understanding where this data is collected online. I’m not saying that this is something to be terrified of. Just be aware of it. An example of how this data can be used, we can look back to 2012 when Target figured out a teen’s pregnancy based on her shopping habits. In line with the previous point, just be aware that data is being collected and has value. Ultimately it’s being used to understand you, but this can be misused by malicious actors.
Limit the Information Being Collected
As mentioned above, there’s a lot of information being collected about us. At times, this is beneficial; it can yield things like loyalty points and discounts. A favorite of mine was the reordering of previous food shop products; it made ordering faster. But when the benefits are not outweighing the risks, you can practice these steps:
- Deletion of account: Create false data within the input fields such as a fake name, date of birth, and address and then delete the account.
- Providing limited information: In the case that there are legal requirements for legitimate data, you can restrict to only providing the required information for the required amount of time. Instead of a private residence, use a hired post box. Use an email address you have access to but isn’t used for password resets. Consider using initials vs. full names.
- Providing alias information: If you must create an account that doesn’t require 100% accurate information, you can always use an alias. When I create an alias account, I record their name, DOB, email address, and occupation in my password manager under Identities. This way, I can reuse this alias wherever there is no legal requirement for legitimate information. It saves me time. Plus, if there’s ever a need to validate myself, I’ve recorded my responses, so there's no need to memorize anything.
Beginning Your Privacy and Digital Security Plan
Oftentimes, I hear it’s ‘too late’ to start being safer online, and all the information is out there already. However, this simply isn’t true. The best time to start being security- and privacy-focused is today! To start, consider the information you do have online. Take time to collect accounts and subscriptions – stalk yourself!
Simple steps you can take:
- Make a list of all social media, online banking, and digital loyalty programs you’re signed up for.
- Go to different search engines such as Google, Bing, and DuckDuckGo and search your name. You can add further details such as Name, Country, and Occupation. See what comes up in your search. You can further reduce the scope by using things like Advanced Google Search or Advanced Twitter Search.
- Set up digital alerts on yourself using services like Google Alerts or Twilert for examples. There are also many more options out there.
- View your social media accounts from a public perspective. On some sites, you can select ‘View As’ others you can sign out to view. Further still, you might need an unconnected account to view. Another option is to ask a trusted friend to look at your accounts for you. See what information is displayed and to whom. Working together, your friend can search for you, and you can search for your friend.
- Consider separation of emails, I personally have an everyday email, one for mailing lists, another one for password resets, and others. Most emails forward to my everyday email, but a few I am signed in separately.
- When creating new accounts, consider the connection between them. Do you want to provide your real DOB? Do you want to use the same email address, or can you use an email that forwards to yours? Even if ‘sign in with your Facebook account’ is an option, why not select the separate login option?
Controls you can put in place:
- Keep devices up to date.
- Use strong passwords.
- Consider a password manager. Some have family packages; consider sharing passwords through this or other physical solutions.
- Enable multi-factor authentication. This can be done using SMS, application, or physical tokens.
- Sign up to be notified when a breach happens on Have I Been Pwned?
- Use ad-blockers and limit tracking. This can be done via plugins or through specific browsers such as Brave. You can also view security and privacy settings and verify that things align with your needs.
- Use VPNs when connecting to unknown WiFi or restrict to mobile data when traveling.
- Install anti-virus on devices that support this, including mobile devices.
Talking Security to Children
When I was a kid, I wanted to be accepted. There wasn’t Facebook then, but if it did exist, I can imagine I would have wanted to have taken part. I also can imagine that if someone had asked to connect with me, I would have accepted because of that need to be included. When kids and vulnerable persons create accounts, it's always valuable to:
- Discuss their rights.
- Explain that at times malicious actors will pretend to be friends.
- Share and discuss easier-to-understand Terms and Conditions.
- Highlight how location data can be collected and used against you.
- Provide a guideline for use. While limiting the hours and monitoring use might seem invasive, it is beneficial in identifying when something isn’t right.
- Have open and safe discussions on social engineering, manipulative ads, and more.
Empower your child to know that they can say no to friend requests, having their picture taken, being tagged in a photo, and creating an account in the first place. Be the safe person whom they can ask for support and advice.
Maintaining Personal Security in the Long Term
Share your personal security plan with loved ones, including children, family, and friends. When someone doesn’t follow your request, speak to them on why you want to follow this – i.e. a family member of mine doesn’t allow their children’s photos to be posted online. Instead, they’ll be happy to post physical copies of pictures or share privately on email or secure file storage. If an image is shared, they will politely remind the poster of their request. I have another friend who has discussed with their child they have a right to say no to pictures. By discussing this with the child, and empowering them to respond when someone has not followed their request, this child now actively is in control of who can take their photo. This has included public discussions with strangers who take their photo without permission. As a child grows, it’s important to remind them of not only their rights but how to recognize when someone is overstepping. Cyber bullying is a massive problem, and unfortunately, most platforms are under-equipped to handle this. If your loved one, of any age, knows they can come to you and discuss something without fear of punishment, it will be easier to keep on top of it.
Understanding your Threats
The above advice is a great place to start. However, it shouldn’t be seen as a specific plan. Realise that each person has a different threat map, and your security planning should include this:
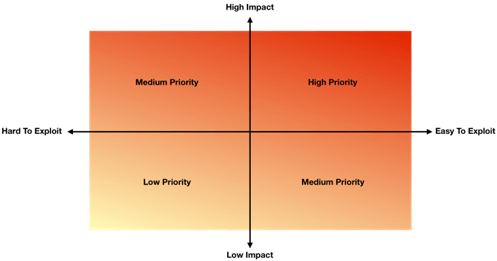
Looking at the above heat map, you can start to align your needs based on the asset i.e. a child’s photograph, a social media account, a piece of information such as a mobile number. In the example shared previously, the photograph of the child and their certificate was easy to find because it was posted online publicly (easy to exploit) and the information given was highly valuable to a malicious actor (high impact). Therefore, the parent could recognize this, take the image offline, or take a picture without the certificate, and mitigate the impact (less identifying information) and lower the impact (knowing the child plays football, but not where, when, age, or name).
In Conclusion
When building a digital security plan for yourself, your loved ones, and your friends, make sure to be aware of the risks you are concerned with. Be upfront about your wishes, and instead of perfection, strive for continuous improvement. Do not set out to embed a highly strict and unusable solution. Build something that is proportionate to your risks, understanding, and capabilities. What comes challenging now can become natural over time.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

