
Despite increasing data breaches, ransomware attacks, and assorted cyber threats, convincing the Board of Directors to invest in robust cybersecurity isn't always easy for many businesses. The challenge originates mainly from the need to demonstrate a quantifiable Return On Investment (ROI) from any cybersecurity initiative. Many Boards concentrate on performance indicators, profits, and strategic resource distribution, while cybersecurity primarily focuses on risk mitigation.
It is crucial to bridge this communication gap to ensure that the Board understands and acknowledges the significance and value of cybersecurity.
Decoding the Language of the Board
To effectively communicate the importance and ROI of cybersecurity initiatives, it is necessary to understand and speak the Board's language. This language centers on business growth, risk management, and strategic investment.
Here are some key points to consider:
Investment Returns
A perennial concern for Board members is the ROI of any proposed investment. They demand clear insights into the concrete and abstract advantages the company will gain in relation to its investments. This is a reasonable expectation. The dilemma raised with cybersecurity is that the benefits often revolve around averting potential pitfalls rather than directly enhancing profits.
Solutions like Privileged Access Management (PAM) and secure Remote Desktop Protocol (RDP) can offer a quantifiable ROI by maximizing resources when it comes to securing access to applications and systems.
The ROI from PAM can come in several forms. First, there are direct cost savings from preventing security breaches. According to a recent report, the average cost of a data breach in 2023 is $4.45 million. By investing in a PAM solution, organizations can significantly reduce their risk of experiencing these breaches, which usually far outweighs the cost of implementing the solution.
Beyond direct cost savings, PAM also offers indirect benefits that contribute to ROI. For example, by controlling and monitoring privileged access to critical systems, organizations can ensure compliance with regulatory requirements. This can save businesses from costly legal fees and penalties for failing to comply with regulations.
Business Risk Management
Board members have a deep understanding of risk factors. They acknowledge that risks can't always be entirely eliminated, but can be supervised and minimized. In discussions about cybersecurity, underline how the proposed investment will help mitigate the risk of cyber events and the ensuing financial losses.
This approach should be unique and tailored to the specific organization and should start by clearly identifying the risks that are most relevant to the organization. This could include risks related to a specific vulnerability in remote access systems or risks posed by expanding IT infrastructures.
It's important that the information presented to board members uses accurately collected data, such as statistics and case studies to demonstrate the potential impact of these risks on the organization. Once the risks have been clearly identified and prioritized, the PAM solution can be presented as a key tool in mitigating these risks.
Cost-Effectiveness Analysis
Board members frequently use cost-effectiveness analysis to balance the anticipated benefits against the intrinsic costs of a project. In cybersecurity, the benefits often include protecting the company's reputation, evading regulatory fines, and shielding crucial business information.
Strategic Value Over Time
Board members favor initiatives that offer enduring strategic progress. In terms of cybersecurity, this entails maintaining customer trust, ensuring seamless business operations, and securing a competitive edge in the industry.
Unveiling the Hidden Expenses of Insufficient Cybersecurity
Cybersecurity is often seen as a cost center rather than an investment, but this perspective can be misleading. An insufficient cybersecurity strategy can lead to hidden costs that far outweigh the initial investment in robust security measures. Below are some examples of potential hidden costs:
1. Financial Loss from Data Breaches
The most obvious cost comes from data breaches. Depending on the sensitivity of compromised information, whether from a profit and loss spreadsheet or a complex business database, a company can incur costly extortion demands from cyber criminals, financial compensation for affected customers, and regulatory fines.
For instance, T-Mobile's 2021 breach compromised over 53 million customers' data, leading to around $350 million in fines and legal costs. Beyond this, the intangible loss of customer trust and reputation can have long-lasting financial impacts on the company.
2. Damage to Brand Reputation
A security breach involving sensitive data can have serious consequences for a company, damaging its standing in the public eye and affecting customer confidence and loyalty. Although it is challenging to quantify the precise repercussions, incidents like these can have a lasting effect on a company's economic health. Rebuilding a damaged reputation is a lengthy and resource-intensive process, further escalating the overall expenses.
Recently, LastPass, a well-known password management company, faced a serious setback when it experienced a security breach. This incident led to the exposure of customer email addresses and password hashes. Given the nature of their business, this breach significantly impacted their reputation for reliability and security.
3. Operational Disruptions
Cyber attacks can disrupt business operations, leading to downtime and loss of productivity. The cost of these disruptions can escalate quickly, especially for businesses that heavily rely on digital operations.
For instance, businesses offering online services like e-commerce platforms or cloud-based applications can experience significant repercussions if there's a breach of their clients' data. Since these services typically operate on a subscription model and cater to a wide customer base, any operational disruptions can result in numerous missed revenue opportunities.
4. Legal Expenses
Companies may face lawsuits from affected customers or partners in a data breach. These legal proceedings can be costly in terms of monetary expenses and the time and resources required to manage them.
Frequently, lawsuits stemming from data breaches escalate into class-action cases, potentially resulting in substantial legal settlements and fines. These costs are an added burden following a cyber attack, further damaging a company's reputation and standing if held responsible for the breach. The widespread attention these lawsuits attract can also erode customer confidence.
5. Increased Insurance Premiums
Following a significant cyber incident, businesses often see a rise in insurance premiums. This is another hidden cost that can add up over time.
When combined with other expenses, such as legal fees and lost business opportunities, increased insurance premiums can significantly impact a company's bottom line.
Evaluating the ROI for Cybersecurity
Determining the ROI for cybersecurity can be complex due to its many intangible aspects.
In contrast to other investments, cybersecurity doesn't typically yield direct revenue. Instead, it is a protective shield, protecting revenue and safeguarding the company's assets. As such, the ROI for cybersecurity is often computed based on the cost savings from potential threats that were averted due to the security measures in place.
Here's a fundamental approach to assessing the ROI on cybersecurity:
- Identify Possible Losses: Identify what your organization will lose if targeted by a cyberattack. This includes direct costs such as system recovery and legal expenses and indirect consequences like brand damage and loss of customer trust.
- Estimate the Likelihood of a Cyberattack: While precise predictions are difficult, historical data and industry trends can provide insights into the likelihood of your business being targeted by a cyberattack.
- Calculate Potential Cost Savings: Multiply the evaluated risks of a cyberattack by its estimated likelihood to estimate the potential savings from specific cybersecurity measures.
- Deduct the Cost of Cybersecurity Measures: Lastly, subtract the cost of your cybersecurity efforts from the estimated savings to find the ROI.
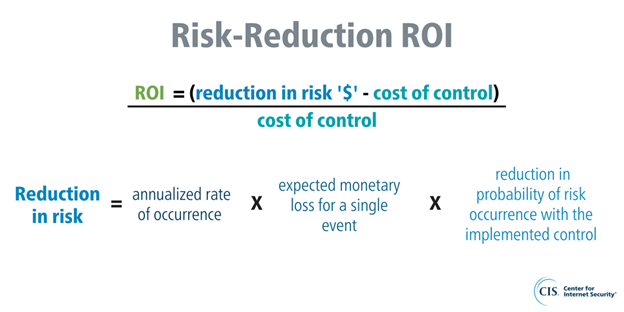
Image Source: CIS
Know How to Convince Your Board
Effectively communicating with your Board is essential when it comes to cybersecurity investments. By using language that resonates with Board members and presenting your ROI calculation clearly yet impactfully, you can ensure that your cybersecurity investments receive the attention and funding they rightfully deserve.

About the author:
Joseph Carson is a cybersecurity professional with more than 25 years of experience in enterprise security and infrastructure. Currently, Carson is the Chief Security Scientist & Advisory CISO at Delinea. He is an active member of the cybersecurity community and holds a CISSP credential. Carson is also a cybersecurity adviser to several governments, critical infrastructure organizations, and financial and transportation industries and speaks at conferences globally.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire.
Tripwire ExpertOps
Elevate your organization's cybersecurity with Tripwire ExpertOps! Explore our managed security service now to ensure round-the-clock protection and expert guidance in safeguarding your digital assets.

