
I recently came across the "Johari Window Model" and thought this would be a good way to gain inspiration to explain the conundrum faced by many cybersecurity customers. The table below shows us the breakdown of the stages that are applicable not just to IT and OT environments but also to other facets of our daily lives.
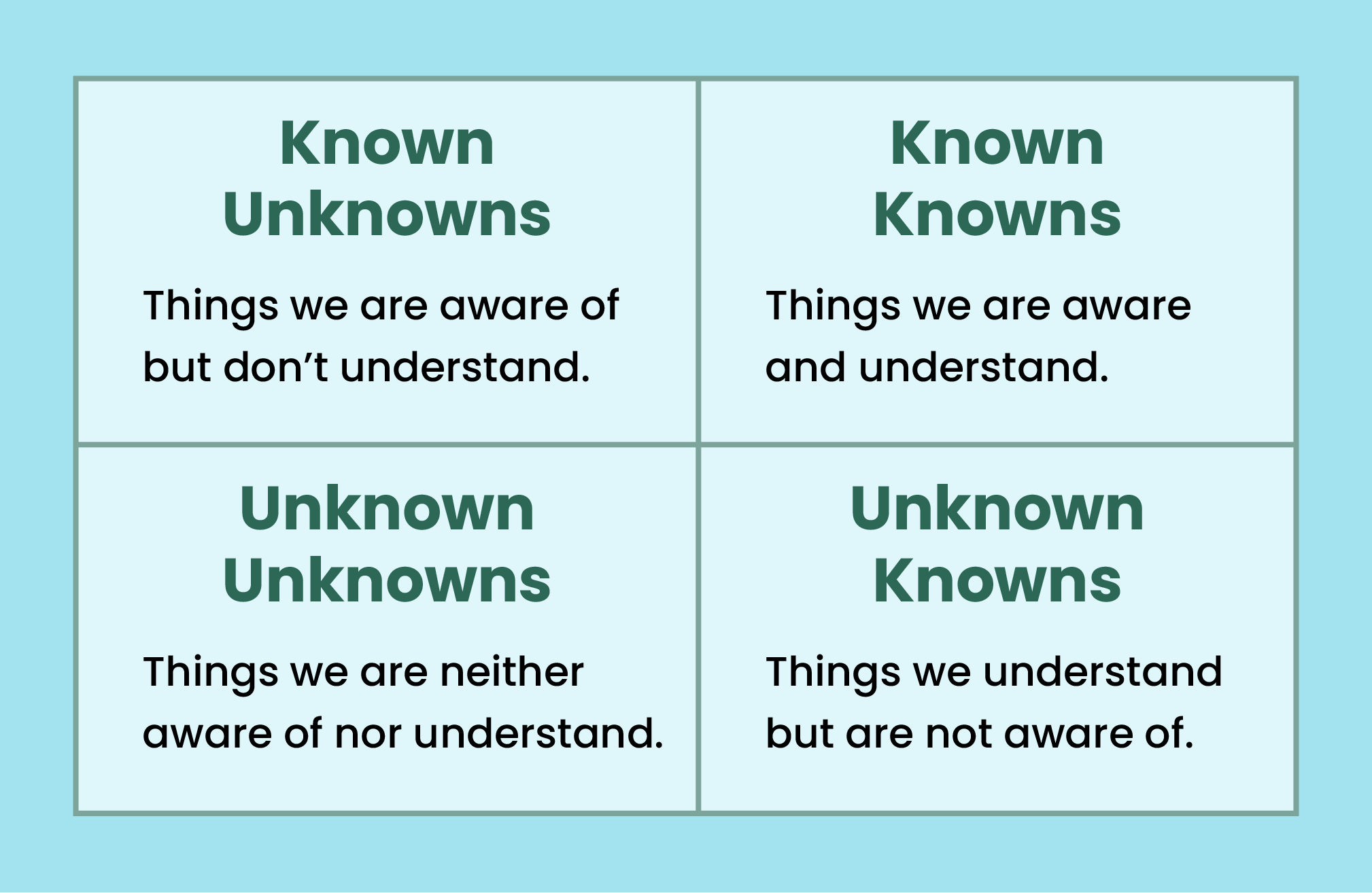
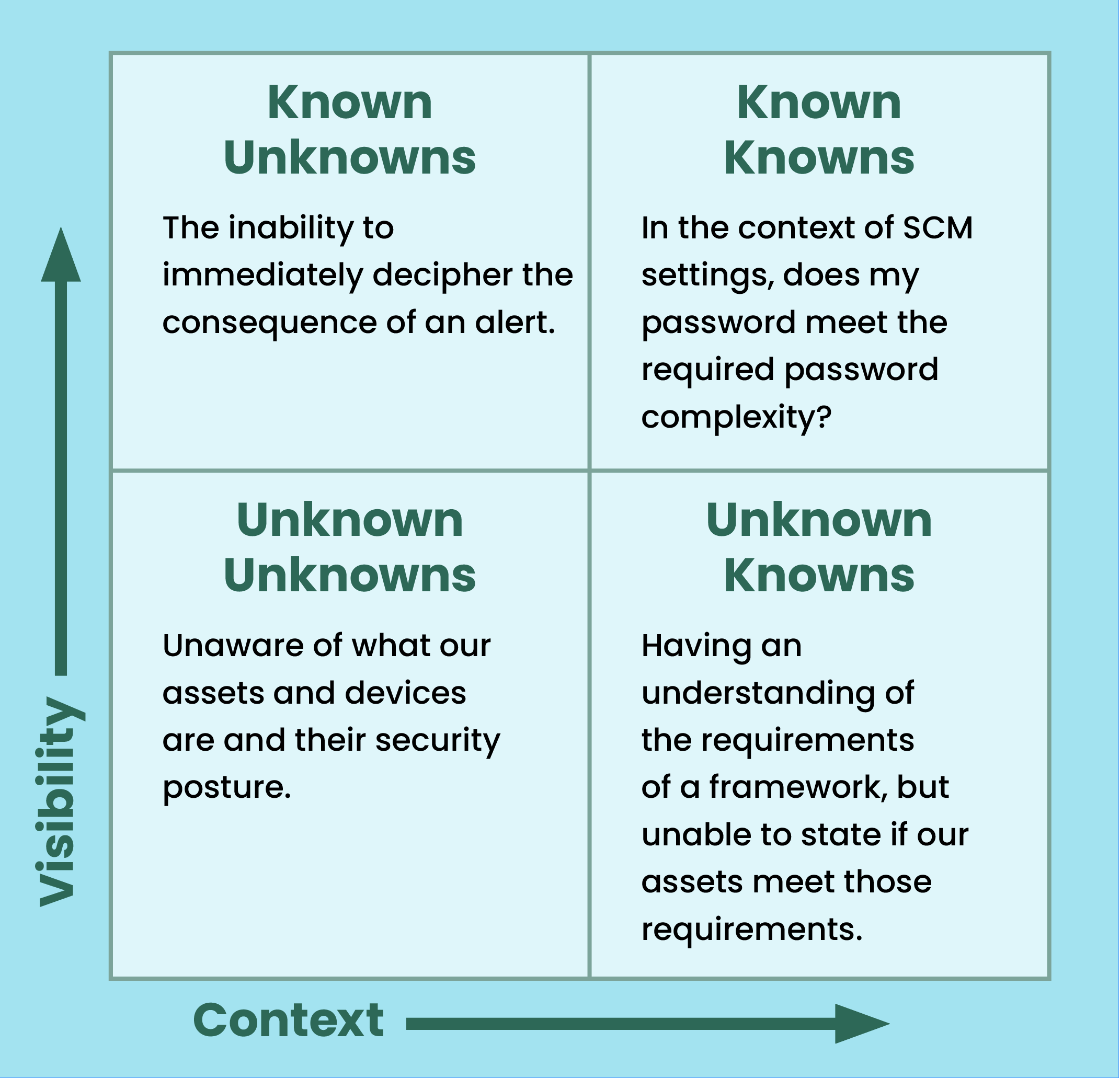
This model can be applied to asset discovery and Fortra's Security Configuration Management (SCM) system.
There are situations when we lose insight into what our network asset inventory consists of. This is sometimes unintentional because, as busy individuals in the world of IT and cybersecurity, something always pops up! Sometimes, the inventory awareness gap is caused by a lack of the correct tools, the knowledge, and the know-how to be able to address rogue assets connecting to the environment.
If we examine "what we know," these would be the assets that are onboarded using a strictly defined and documented process that follows the rigorous steps required to connect to our network. These would be our "known knowns." Conversely, our "known unknowns" are those devices connecting to the environment for which we do not have visibility and detailed insight into each device's security posture. That leaves us to figure out the "unknown knowns" and "unknown unknowns."
Unknown unknowns can be likened to "Dark Matter," where the assets remain undetected, and worse, they remain undiscovered. The "unknown knowns" can be likened to a lack of awareness of assets even though there is ample experience and know-how about the environment.
How We Address the Most Difficult Johari Factors
Fortra's Tripwire Enterprise (TE) provides powerful insight into the security posture of every asset by capturing data and analysing it through the TE compliance engine. TE runs compliance checks with the most popular, industry-recognized compliance frameworks. The TE policy library is vast and extensive.
TE takes this a step further as well. It empowers you to unmask the "known unknowns" and the "unknown knowns." It does this by leveraging the Tripwire Data Collector to find previously undisclosed assets and the state of their security posture.
Tripwire Data Collector (TDC) is an extension of the Tripwire Enterprise (TE) console that enables TE to gather configuration data on industrial devices, look for changes, and assess compliance. TDC can integrate with a variety of intermediary industrial software packages for a unique "no touch" approach. It can also scan devices directly using a variety of standard industrial protocols such as Modbus/TCP, EtherNet/IP CIP, SNMP, and Web Retriever. All of the data collected by TDC can be incorporated into the same change and security configuration management workflows supported in TE.
The ability to investigate an unknown/suspicious/newly provisioned device cannot be overstated. Many organizations must adhere to an industry-defined standard, but in order to understand the device that has appeared in the environment, it must be held to a more stringent standard. This way, its inclusion can be affirmed with certitude.
All assets need to be compliant with a standard we defined specifically for this purpose. TE can conduct a compliance scan against a stricter standard before an asset can be reassigned to the relevant industry standard. This ensures a continuous risk management approach in the environment. The advantage of subjecting an asset to a stricter standard than necessary is that it reveals the full range of information about an asset without hindering the services and functionality provided by the asset. Why is it important? Because if it is something that is connecting to your infrastructure for a legitimate reason, TE raises visibility for the most accurate compliance assignment in the environment.
This approach provides you with the ability to document the security posture and state of the asset from its initial onboarding to its acceptance into the environment. It provides full reporting capabilities from the initial discovery of the asset.
The Ultimate Goal of the Johari Asset Conundrum
It is important to understand that what we know defines the limits of what we do not know. When it comes to asset discovery and management, we need to bridge this gap by moving to the top left of that "Johari Window." By using agent and agent-less methods in TE, you will be able to discover new assets and support a vast array of different devices. TE applies context to help you understand and interpret the data.
Perhaps most importantly, TE gives you the ability to fill in the gaps by ensuring that IT teams have full visibility into the environment. This moves you into that sweet spot in the top left corner of the "Johari Window."
Learn more about how Tripwire Enterprise can help your organization can have more "known knowns" in your environment.
Tripwire Enterprise: Security Configuration Management (SCM) Software
Enhance your organization's cybersecurity with Tripwire Enterprise! Explore our advanced security and compliance management solution now to protect your valuable assets and data.
