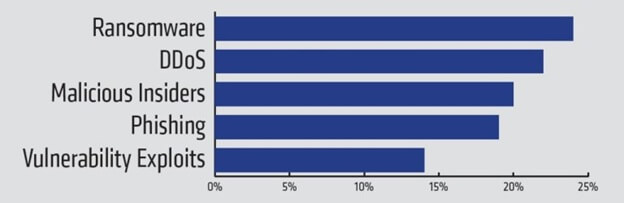
In January 2017, Tripwire completed a survey of 403 IT Security professionals about the most common attack types and how prepared organizations are to defend against them. You can read about the details here. There are two important conclusions from the research that I have to share for the purposes of this post. First, the top five attack types from the survey respondents:
The second conclusion is that the majority of respondents said they weren’t prepared to defend against all five of these. There were varying percentages for each attack type individually (though never a majority that felt prepared), but overall, 90% said they didn’t have the skills, and 97% said they didn’t have the technology, to protect against all five. Simply identifying problems isn’t really what Tripwire is about, nor is that what information security in general is about. Most of us are here to solve problems. One outcome from the survey is that the majority of respondents (93%) felt that foundational security controls would definitely help with these attack types. A survey isn’t a great place for a long explanation, but I wanted to make sure that we’ve outlined how specific foundational controls can help with these attack types. In order to undertake this task with a view to something actionable, I’ve selected the Center For Internet Security 20 Critical Security Controls as a framework of foundational controls from which to draw. Here’s a chart on how the CIS controls apply to the attack types identified in the Tripwire survey.
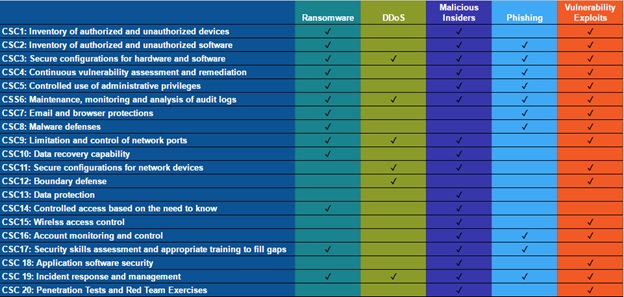
A chart, while handy, isn’t really an explanation, so we’ll approach this one attack type at a time. There’s no silver bullet here, but we can significantly reduce the risk from these attacks by implementing foundational controls.
Ransomware
Ransomware can be devastating and costly, which is why it ranks number one for the survey respondents. It doesn’t have to be, however. Addressing ransomware is really a two part process: prevention and remediation. Detection isn’t a big problem here. Since you can’t pay a ransom you don’t know about, attackers are incented to advertise the compromise. We may not think of backups as a foundational security control, but disaster recovery and business continuity are certainly information security disciplines. Keeping backups that can easily be restored is the key to recovering from ransomware. Late last year, the San Francisco MUNI transportation agency experienced a ransomware attack, but because they had backups and the ability to restore systems, they didn’t pay the ransom and the operational impact was minimized. Recovering from ransomware is good, but it’s far more preferable to avoid it entirely. That’s where prevention comes into play. The prevention steps for ransomware aren’t as straightforward as remediation. Ransomware doesn’t arrive on your systems via a single attack vector, so prevention is really about addressing the most common vectors, and that’s where foundational controls excel. In April of 2016, Deloitte published this paper on ransomware, including an exploration of the most common attack vectors. They were:
- SPAM
- Exploit Kits
- JBoss Vulnerabilities
- RDP Attacks
Let’s first acknowledge that SPAM is a huge delivery mechanism for ransomware and malware in general. There’s little doubt that email security is a foundational control, CSC 7 in fact, and that it’s key to preventing ransomware. That being said, email security isn’t the only line of defense against ransomware. Much of the malicious emails carrying ransomware into organizations require an additional criterion to be successful: a vulnerability. If the email in question has a malicious attachment, chances are that the attachment exploits a vulnerability to install the ransomware. If the email carries a malicious link, chances are that the link requires a vulnerability to exploit to install the ransomware. In fact, if you look through the remaining three attack vectors, they all have a vulnerability component. Exploit kits? Well, they exploit vulnerabilities. JBoss vulnerabilities are just that, and RDP attacks also exploit vulnerabilities in RDP. It seems painfully clear that vulnerability management, which is CSC 4, is a key foundational control for preventing ransomware. At a layer lower than addressing the vulnerabilities, deploying secure configuration management can also help reduce the attack surface available to ransomware. Ensuring that systems don’t have extraneous applications available for exploit can eliminate vulnerabilities before they exist. Closing off services like RDP, except where necessary, can also prevent exploits from having an opportunity to run. Ensuring you know what’s in your environment and that your systems are configured securely fall into CSC 1, CSC 2, and CSC 3.
DDoS
Distributed denial of service attacks are some of the most complex to defend against because they’re not just one attack type. In fact, DDoS is really a class of attacks that can be broken down into a multiple specific attacks. Mitigation strategies need to address the individual attack types at a technical level, which can be both tedious and challenging. Rachel Kartch of Carnegie Mellon produced a complete and very clear explanation of the variations of DDoS attacks along with a wide-reaching set of recommendations. For the purposes of this post, the objective is not to describe the detailed mitigations for DDoS attacks but to identify where foundational security controls can help. In this case, the foundational control that’s primarily useful are secure configuration management and change detection. CSC 4 and CSC 11 encompass secure configuration for hardware, software, and network devices. Change detection is identified in the Critical Security Controls as file integrity monitoring in CSC 3. These two controls can be used to ensure that the DDoS mitigations are in place and functioning. Deploying specific hardware or features to mitigate DDoS attacks does no good if their not configured properly.
Malicious Insiders
As a category, malicious insiders is very broad. This attack type really includes anyone inside the organization who takes actions with the intent to harm the company. That covers everything from full blown espionage to a sales person downloading customer data to take to another company. The breadth of this threat is what makes it an ideal candidate for risk reduction through foundational controls. Broadly, the malicious insider threat can be broken down into a few categories:
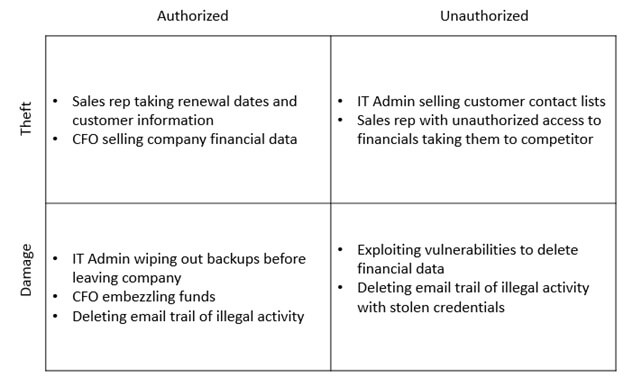
Given these four quadrants, how do we apply foundational controls? In this case, it’s actually easier to identify the controls that are least likely to help with malicious insiders. Any control that secures systems, tracks or identifies data, or manages privileges is going to help. What’s left over? Email and browser protections (CSC 7) along with malware defenses (CSC 8) are not as likely to apply here. These controls are more effective for malicious outsiders than insiders. Likewise, boundary defenses (CSC 12) are focused on protecting systems from outside attackers. The remaining 17 of the CIS Controls will find some applicability for malicious insiders. Top of the list, however, are going to be those that protect data directly, like CSC 13 (Data Protection), and those that monitor or manage privileged access, like CSC 5 (Controlled use of administrative privileges) and CSC 6 (Maintenance, monitoring and analysis of audit logs).
Phishing
Phishing is really the start of an attack, but its tentacles can reach deep into an organization. Usually, phishing presents a first contact opportunity for an attack, and the results are either compromised information or a compromised system. Either way, the attacker is generally looking forward to another objective beyond that phishing interaction. CIS identifies two foundational controls that are specifically targeted at defense against phishing. CSC 7 (Email and Web Browser Protections) is directly applicable here. The specific controls within this family are targeted at reducing the attack surface for browsers and email as well as preventing malicious email from getting to the end user. A phishing email often attempts to exploit a vulnerability on the system to install malware or steal data, so controls that reduce the attack surface or address vulnerabilities are key. Beyond CSC 7, there are others that broadly address the peripheral conditions that make phishing successful (CSC 2-6, CSC 8, CSC 16-17 and CSC 19). Finally, CSC 17 (Security Skills Assessment and Appropriate Training to Fill Gaps) is also worth calling out specifically. This control includes training users to recognize and avoid fraudulent emails. Technical controls can do a lot to defend against and respond to phishing, but user training is also a key component.
Vulnerability Exploits
If there’s one attack type that most clearly maps to a foundational control, it’s this one. If you’re worried about vulnerability exploits in your environment, then you probably need to consider CSC 4 for Continuous vulnerability assessment and remediation. Most organizations have implemented some vulnerability scanning, but while simply running scans may be sufficient to comply with some standards, it’s not enough to address this attack type. The CIS CSC is specific in requiring continuous assessment and remediation. That means that you have to be able to run scans at the rate of change in your environment (and in the threat landscape) as well as have a process for dealing with the results. I won’t attempt to enumerate the entirety of VM best practices here, but if this is the area where you need to focus, consider checking out a more complete treatment of it here. The most important aspect to keep in mind is that you can’t simply buy a tool to successfully deal with vulnerabilities. Identifying them is a good start, but the people and process aspects need to follow the technology to actually make progress.
Conclusion
It’s common in information security to look at the most recent innovative attack in the news and imagine that you need a shiny new tool to deal with it. A fair amount of the information security industry is based on just this pattern. The fact is, however, that foundational controls are foundational because they deal with the breadth necessary to manage risk in a changing landscape. New controls may become foundational over time, but the old ones largely remain core to successful risk management. Anytime there’s a new threat to deal with, rather than using it as a means to acquire a new shiny objects, consider how that might be used to drive more excellence in the foundational controls you have today.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

