
The world of IT is moving to the cloud. Market data varies but estimates of cloud usage show approximately 20-25% of overall computing workloads operate in public cloud environments today, with that number expected to grow to 50% over the next 5-10 years (Goldman-Sachs forecast). Organizations are starting to operate in a hybrid environment that includes both public cloud and private cloud, as well as virtualization. For most organizations, this will require security controls that can serve this complete infrastructure. Just like how perimeter defense isn’t enough to protect your corporate networks, workloads in the cloud aren’t secure by default. The AWS Shared Responsibility Model is very clear about this.
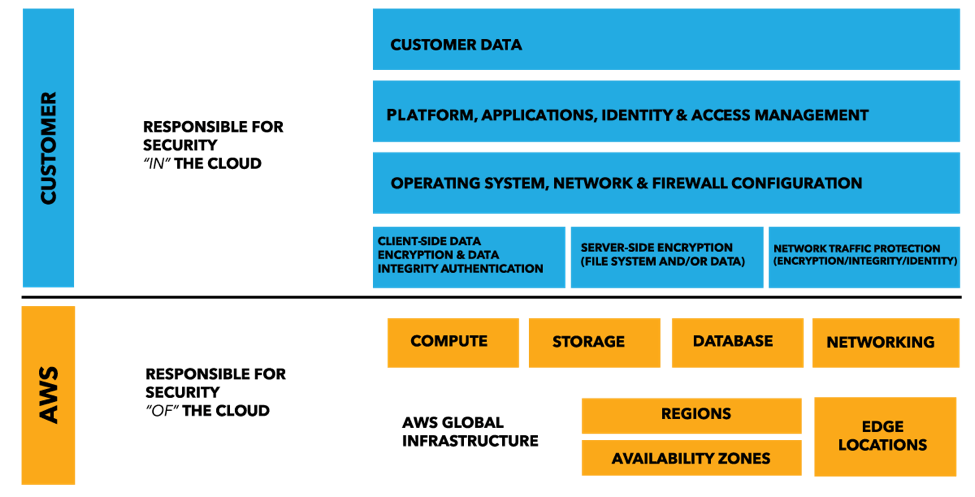
Shared Security Model. Credit: Amazon Web Services. AWS takes care of the underlying infrastructure but its customers are still responsible for the security, compliance and operational controls of their data and apps in the cloud. This means foundational controls like secure configurations, vulnerability management and log management are just as important in the cloud as they are on-premises. If you are planning on moving workloads from on-premises into the cloud, you may face a few challenges since controls may not work the same way in both environments. Cloud infrastructures are different from their on-premises counterparts. If your security and compliance controls were designed for on-premises environments, don’t assume they will work correctly in the cloud. For example, controls may lack support for cloud-oriented tech like Amazon Linux or Docker containers. Conversely, don’t assume that controls built for the cloud will work well or at all in on-premises environments. If your controls don’t support both types of environments, you may end up deploying multiple controls for multiple environments. Dealing with multiple controls for environments is time-consuming in terms of deployment, administration and reporting. In addition, gaps in monitoring can occur if the data is not consistently collected and centralized across all infrastructure. Another challenge is the dynamic nature of elastic computing environments where elastic assets come online and go offline to scale up and down to meet demand. Your security controls will need to match that demand as cloud assets are rapidly created and destroyed. Otherwise, gaps in visibility and errors can occur as hosts appear and disappear. An example of overcoming this challenge is a story of two large financial services organizations that sought to minimize the time between receiving and pushing out fresh machine images to their service providers. Both organizations implemented controls that automatically baseline each image as soon as it is received. Subsequent changes are detected in real-time, eradicating any windows of exposure and ensuring uninterrupted compliance with all prevailing policies. The ability to rapidly deploy images, even if only for a couple of hours, enabled their application developers to take full advantage of the unprecedented flexibility of the cloud through continuous protection and the permanent audit trail. In other words, make sure that your foundational controls support the polices, operating systems, platforms and technologies you use across your complete infrastructure. Consider a toolset that can:
- Monitor both on- and off-premises environments
- Apply the same robust controls across on-premises and cloud networks with unified management and reporting environment
- Dynamically on-boarding and off-boarding nodes to ensure continuous coverage in elastic environments
- Support for cloud policies and platforms in addition to the policies and platforms that you use on-premises
- Assess DevOps and cloud-oriented technologies like Docker containers
- Deploy easily with pre-hardened machine images for your environments of choice (i.e. AWS, Azure, VMWare, etc.)
In summary, you may need to protect both on- and off-premises environments in the foreseeable future. But not all solutions work equally well between on-premises and the cloud, so don’t assume that what worked on premises will work in the cloud. Are you migrating your infrastructure to the cloud? Download this paper to learn how to evaluate the security and compliance of your provider, and how Tripwire solutions can help.

