
The ransomware, malware and phishing attacks going on in the healthcare industry are quite alarming these days. The customers' data in the healthcare industry is more sensitive than in most industries, and this has proven to be a sweet spot for threat actors. Recent research by Infloblox reported that in 2022, there were over 546 major data breaches due to malicious activity. This follows a 4% increase over the 521 major data breaches reported by healthcare institutions in 2023. These numbers have continued to rise steadily for over 5 years.
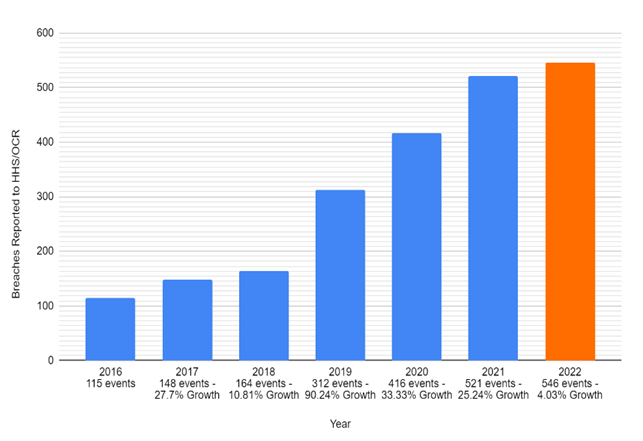
The data also shows that from 2016 to 2022, the total healthcare data stolen in the U.S. due to cybercrime included 178,240,656 records. Today, the healthcare industry has become one of the most vulnerable sectors to cybercrime, but the question is: how can leaders in the healthcare industry minimize it? Domain Name System (DNS) security may be an effective tool to help combat healthcare cybercrime.
How does DNS work?
We continually hear about malicious attacks in different business sectors and many times, DNS is the attack vector. When most people use the internet, they use domain names to specify the website that they want to visit, for instance, tripwire.com. These domain names are mapped by DNS to Internet Protocol (IP) Devices.
DNS is a protocol that acts as the phonebook for the internet, providing human-readable names for web-based services. For example, when the people-friendly domain name tripwire.com is typed into a browser, a program in the operating system (OS) called a DNS resolver looks up the numerical IP address. After this, the person is directed to the site.
In a DNS attack, the criminals alter the pointer records, sending fraudulent information to the requestor, and subsequently redirecting the browser to a different site entirely. This becomes worse if the person is taken to a fraudulent login page, surreptitiously recording the person's credentials.
Disproportionate and persistent
The healthcare industry experienced a disproportionate number of attacks compared to other industries during the COVID-19 pandemic. This trend has stuck, probably because the data remains so valuable. There are different types of DNS attacks, ranging from Denial of Service (DoS), DNS amplification, and Cache poisoning.
Malware and ransomware are frequently used against healthcare institutions — they might be a foul request from cybercriminals to compromise the DNS in a medical imaging system, which can lead to a deteriorated system, and easy access to patient health records.
Attack Effects
- Cloud service downtime.
- Loss of business customers.
- Stolen customer information.
One of the primary reasons for the high value of healthcare data is that the information follows a person for the remainder of their life. Biological information is impossible to change, so the data has broad resale value for a variety of fraudulent purposes, from prescription and insurance fraud to identity theft. "Metadata stored within medical images, including X-rays and CT scans, can disclose confidential information, like patient names, photographed body parts, and the medical centres or physicians involved, leading to patient identification," explains Jean-Philippe Cabay, data scientist at NTT Global in Belgium.
DNS Security in Healthcare
DNS security plays an essential role in safeguarding healthcare services. DNS Security Extensions (DNSSEC) involve a set of specifications for authenticating DNS requests and responses using cryptographic digital signatures. With DNSSEC, a DNS server makes sure the root name server is permitted to send a response and that the information in the response is safe. DNSSEC also ensures that the response was not modified while in transit.
- DNS logging - This records client activity and keeps track of issues related to DNS queries. DNS logging is simply the process of compiling a detailed overview of data on DNS traffic. This is used to help network administrators resolve DNS errors. If you want to monitor network security in real-time and block upcoming attacks, then DNS logging should be one of your go-to practices.
- Lock your DNS cache - Locking your DNS cache involves controlling when people can access it. When the cache is locked, it's harder for malicious actors to sneak in and exploit the information stored inside the cache. You can also use DNSSEC to validate your DNS data security. DNSSEC uses digital signatures to make sure that the information clients receive is valid.
Wrapping up
With the healthcare industry becoming a gold mine for threat actors, every leader in the industry must become intentional about boosting their cybersecurity setup to avoid troubling issues for their customers. There are many ways to create a better security environment, including specialized tools to keep abreast of changes in your environment. An often overlooked security vulnerability is DNS. Some simple steps can help you to reduce this hidden risk.

About the author:
Chinwoke Nnamani is a B2B Content writer who specializes in creating well-researched and data-driven content that drives traffic and increases conversions for businesses — small startups and large businesses alike. He has bylines at Tripwire, SendSpark, Capitalism, and FutureofSaaS.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

