
In 1971, Ray Tomlison developed the first email service while working at The Defense Advanced Research Projects Agency (DARPA). This development changed how we communicated. However, even though this was an exceptional tool, it was not very user-friendly, requiring users to have specific software installed on their computers.
In 1996, Sabeer Bhatia founded Hotmail, making it the first web-based email messaging service. Exactly one year after Microsoft acquired Hotmail, I opened my first email account. I still remember the feeling of euphoria that came from receiving a virtual response to the message I sent. It might seem so mundane now, but like all new and noteworthy human experiences, everyone remembers their first time.
Those may have seemed like simple times when the innocent and true inspiration behind building such a great tool was not soiled by malicious intent. Yet, the first phishing attack took place in 1995 when a group of hackers generated randomized credit card numbers to gain free internet access on the America Online (AOL) network. Back then, if you wanted to use the dial-up internet, you had to pay. The only way around it would be to either use a free 30-day trial via a floppy disk or create enough randomized credit card numbers to finally land on a legitimate one. The fraudulent accounts were then used for phishing other AOL subscribers.
Email was designed with fast and reliable communication in mind, without any thought to security. SMTP, which was developed back in 1971, wasn’t really built with security in mind. Although it’s a great protocol in terms of deliverability and speed, it lacks an authentication mechanism. This means it’s easy for attackers to hijack an SMTP Relay server or simply create a fraudulent server and impersonate the legitimate sender. This spoofing attack, when joined with phishing, is an extremely potent attack vector.
According to Fortra’s 2023 Business Email Compromise Trends, Targets and Changes in Techniques report, BEC accounted for 99% of reported threats. Even though historically, BEC has been by far the highest threat vector reported in user mailboxes, this is the first time since Fortra started recording stats that it’s reached 99%. This report makes for some very, very compelling reading, giving insights into some excellent BEC trends but also emphasising where companies should look at to reduce their attack surface. Spoofing makes up for an important part of the email threat environment, providing a degree of credibility to the email sent to unsuspecting victims.
The industry initially overcame the threat with the development of the Sender Policy Framework (SPF), which enables a sender to specify the IP addresses from which an email may originate for a given domain. This information is published as part of a TXT record against the specified domain’s DNS server or provider. Upon receiving the email, the receiver will verify with the DNS hosting provider whether this email was sent from or on behalf of the registered IP address. If it wasn’t, the email will fail authentication.
SPF wasn’t enough to contribute to email security, as it did not guarantee the integrity of the message. SPF also fails too often in legitimate delivery scenarios like forwarding and mailing lists. Since SPF authentication occurs against the envelope domain (which end users rarely see), the “From” field can still be spoofed in an SPF passing message.
This is where DKIM adds value. DKIM uses asymmetric encryption to give email senders a way to digitally sign all the outgoing emails from a given domain and publish the public keys necessary to validate those digital signatures. This enables receiving email providers to confirm that no changes have been made to the email in transit and confirms the source of the email.
When we think about spoofing, the “From” header is what is changed and is most important and damaging to the end recipient, and neither SPF nor DKIM do anything to address this issue.
Domain-based Message Authentication and Reporting and Conformance (DMARC) allows Admins to enforce policy around email to dictate what happens when either SPF or DKIM or both fail in their respective functionality. What happens to the mail can range from being monitored only and reported on, quarantined, or completely rejected. The main takeaway for DMARC is that its requirement for identifier alignment, that is, either the envelope domain that passes SPF or the d= signing domain that passes DKIM, must align with the “From” header domain in the message.
The other strong advantage of DMARC is its ability to request information about each message in the form of aggregated and forensic reports, providing deep email security and movement insights. Coupled with the policy aspect, this makes DMARC extremely powerful and something organisations should aspire to standardise.
In a continued effort to combat email threats, both Google and Yahoo announced that they would enforce several measures and safeguards to minimise spoofing, limit spamming and bolster security for email. These measures came into effect in February 2024. The main highlights of these requirements are:
- Authentication: Arguably, the most important aspect of this mandatory enforcement is that all senders of significant email volume will require strong authentication mechanisms in place, and that’s where SPF, DKIM, and DMARC come into play.
- Enable easy un-subscribes: This is already quite common with many providers, and we don’t see this as a big problem. But let’s discuss this a bit more in detail.
- Ensure only wanted emails are sent: The most interesting aspect of this policy is that Google and Yahoo already have some pretty effective spam filtering tools; to complement this, they’ve suggested some strict spam thresholds that senders must not exceed.
So, let’s dissect these in more detail, with examples.
Authentication: This requirement makes a lot of sense today, specifically given the rise of spam, phishing, and spoofing techniques and the fact that email is possibly the most exploited mechanism in an attacker’s toolkit. A common challenge that many organisations face is the volume of domains they need to manage and the lack of visibility on who’s standing up micro projects within the organisation to leverage email.
Consider the marketing department within a company that needs to send marketing emails to its customers. How many times have we heard of business units engaging in shadow IT activities, taking the easiest path to register domains and send emails on behalf of their project? It’s hard for the IT team to manage and maintain the current set of DNS records and domains with their corresponding DKIM and SPF settings without having this concern thrust upon them.
The case for DMARC is very strong here, where both DKIM and SPF need to be set up to implement a successful DMARC policy successfully. Organisations can start off with a “p=none” state and slowly build their way up to the ideal state of “p=reject”, without having to compromise on key security, authentication, and integrity. This requirement in itself will be an excellent step to drastically reduce spam, spoofing, and domain impersonation while also pulling companies into cyber resilience and helping reduce their attack surface. A good, robust DMARC solution gives the IT department the ability to centrally detect, monitor, and manage all third parties sending on their behalf.
As with all security solutions, there is some work to get this in place in the short term, but the key here is that at least once DKIM, SPF, and DMARC are set, companies can move towards the “p=reject” state over time. The key goals are twofold: enhance security by reducing risk with minimal loss to productivity and enhance brand protection.
Easy Unsubscribes: The unsubscribe initiative has made some good progress over the years, specifically since the introduction of standards like GDPR, which require companies to immediately delete all customer data when requested. GDPR also restricts what information third parties can collect and how. From an email perspective, a requirement of GDPR is to allow users to unsubscribe from all unwanted mail with as simple a process as possible.
The one problem or challenge is when users receive phishing emails with a fraudulent unsubscribe button at the bottom. See the example below:
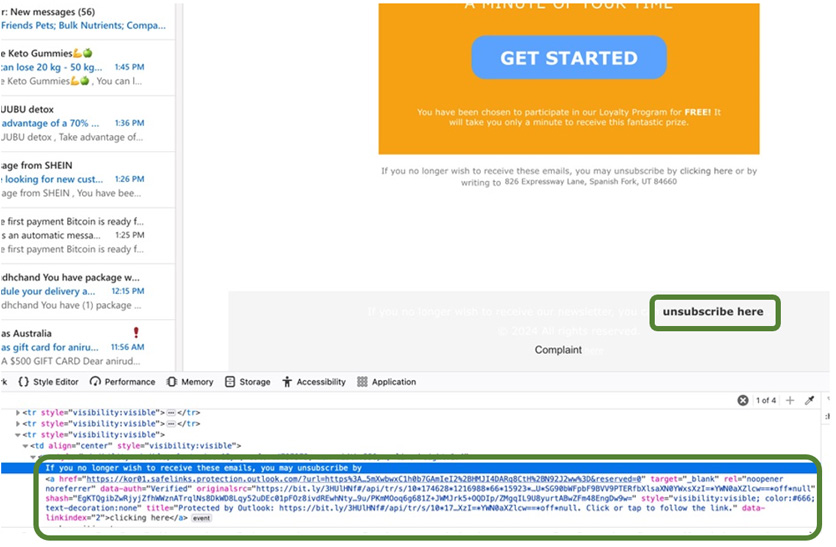
The unsubscribe link outlined above is the same phishing link as the one in the email body.
Of course, security awareness training is one of the best tools that organisations have in their arsenal. Having the ability to train employees and then provide them with very simple options for reporting phishing emails will go a long way to reducing this risk.
Ensure Wanted Emails are Sent: Google and Yahoo will reduce their spam tolerance threshold, aiming to be below 0.1% and not exceeding 0.3%. The implication of crossing this threshold is that both Google and Yahoo will block your company’s email. This could be contentious, as it may conflict with a legitimate organization’s marketing efforts. Reducing spam tolerance is good email hygiene, though, and we have had ample warning time (4 months) to ensure that we adjust our marketing campaigns to adhere to the required standards.
Agari DMARC Protection and Final Thoughts
Phishing emails sent to your current customers or prospects are unpleasant and can erode your brand's image. One can argue that all three of the requirements above will in some way contribute to brand protection, but none as effectively as Authentication, as shown in the following image:
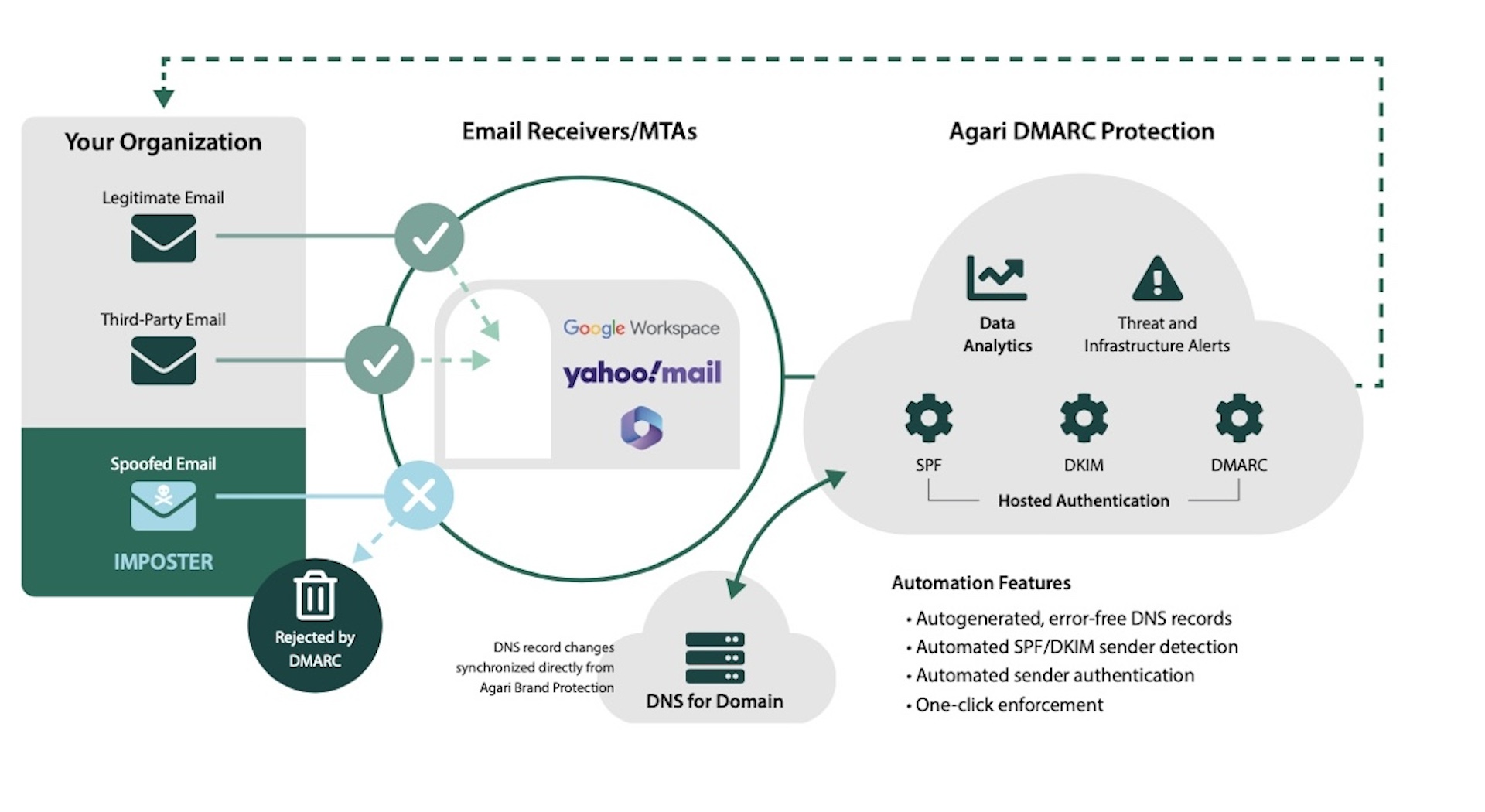
In this scenario, when a spoofed email is sent through an email receiver with a good DMARC policy in place, actions can be taken, depending on the policy set. The email can be rejected, quarantined, or monitored if either SPF, DKIM, or both fail. At a minimum, a report generated on each email delivery will be delivered to the sender, giving them more visibility on their email trends.
At a minimum, a good DMARC solution must be able to support and enhance your brand protection priorities and should have the following functionality:
- Ability to host and manage multiple DKIM/SPF and Brand Indicator Message Identification (BIMI) records: a central repository that can align with your DNS provider to update records instantaneously when new domains are discovered, sending emails on your behalf or when any TXT records need modification.
- Provide granular analytic data through DMARC tags to understand various details about email activity. This contextual information is valuable when reacting to any email risk.
- Threat feed and intelligence sharing to provide further context to support your security and business decisions.
- Adequate support when you embark on the DMARC journey with a skilled and experienced team or process to guide you to your ultimate goal: “p=reject”. Failure to engage the right guidance in the journey to attain a “p=reject” state is probably the key reason why organisations hesitate to adopt DMARC.
Only time will tell what impact these requirements will have on organisations. The is no doubt that DMARC will greatly assist in email hygiene and security.
Fortra's Agari DMARC Protection
Agari DMARC Protection is designed to automate DMARC email authentication and enforcement, safeguarding your brand from misuse and shielding your customers from expensive phishing attacks.

