In today's expanding world of digital security threats, some truths are self-evident. Information security professionals must understand:
- That change happens
- That protecting customers and preventing unnecessary downtime is both a financial and moral imperative
- That we can only collect intelligence on things that we monitor
- That we must constantly verify the state of all our devices.
To succeed in these objectives, IT security experts must stay abreast of the latest threats confronting their organization. More than that, IT security experts must lay a solid foundation of controls that preempt, detect and help remediate risks.
An Overview of the Threats Involved
Steve Weisman, a professor at Bentley University, as well as a leading expert in scams and identity theft, told USA Today he thought three concerns would dominate organizations' digital security strategies in 2016 and beyond. These are as follows:
1. Hackers' Continued Abuse of The Internet of Things
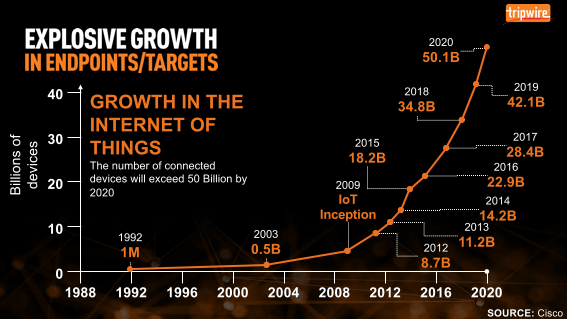
The Internet of Things (IoT) promises to make our lives simpler with innovations, such as smart cars and connected medical devices. Even so, IoT security leaves much to be desired. Many IoT manufacturers currently don't design their products with security in mind, and when users purchase the devices, they don't change their default login credentials or take other steps to protect them against hackers. It's these behaviors that enable Mirai and other malware to amass IoT botnets. Until organizations and users alike take IoT security seriously, we'll likely see more incidents that mirror the distributed denial-of-service attack that targeted Dyn in October 2016.
2. The Proliferation of Exploit Kits There are as many nefarious exploit kits for sale as there are stars in the sky, it seems. What is important here is not the volume of evil products but the ease with which they can be used. One example is the use of massively distributed malware. MAD Malware refers to bad actors' use of previously distributed malware families, such as Dyre, Citadel, Zeus, SpyEye and Shylock, for the purpose of performing new attacks. In fact, the global cloud computing company Salesforce.com had warned its customers that attackers might use the Dyre Trojan to target their login credentials. It is now possible to rent malware that has already affected millions of machines and change “payload" to meet the new objective. These offshoots add to the malware family tree and must, therefore, be accounted for. Another important development is the ease with which criminals can create new malware overall. For instance, researchers at Iswatlab and the University of Sannio (Italy) discovered they could create new malware using a tool they call the "Malware Washing Machine." This engine takes an existing malware sample and transforms it via disassembling and reassembling, repacking, changing the package name, renaming the identifier, encoding the data, reordering the code, inserting junk code, and other techniques. None of these processes change the behavior of the malware but they do create new strains that don't bear the same AV signature as their parent.
3. Computer Criminals' Focus on Infiltrating the Cloud
Companies are interested in purchasing software-as-a-service (SaaS) offerings for the cloud provided by Oracle, Salesforce and others. However, companies need to remember that their provider only protects data that's in their possession. Organizations are still responsible for protecting the data end-to-end, a duty which includes securely transmitting the data between their servers and those of the cloud provider. At the end of the day, attackers want to capitalize on the growth of the cloud, so they are conducting some attacks against cloud-based services. (See the above reference to SalesForce.com.) But they also know that companies take their investment in the cloud for granted, which means they will continue to launch phishing attacks and try to leverage vulnerabilities into network access.
A Digital Security Strategy for the Future
To address the IoT, the proliferation of malware, and migration to the cloud, organizations need to build a solid foundation for their security program. The best way they can do that is by implementing foundational controls. Fortunately for us, these security measures come with their own self-evident truths:
- Know what you have.
- Know its security state, i.e. its configuration and known vulnerabilities.
- Know when it changes.
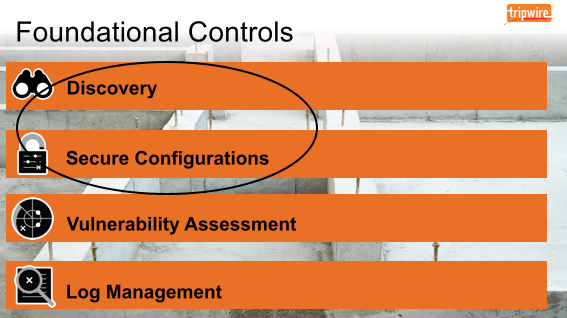
All frameworks refer to these truths in the controls. As a result, many solutions aspire to embed the controls into their functionality. For more information on how foundational controls can revolutionize your organization's security program, please click here.

About the Author: Christopher Beier is a Sr. Product Marketing Manager for Tripwire. Christopher brings impressive security DNA through his 22 years’ experience working for some of the largest cyber security firms in the world. Christopher has deep knowledge and experience in the financial services and online banking security. He is also a 12 year US Navy veteran where he applied IT administration skills to the US submarine corp.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

