
Every security framework recommends that an organization has a cybersecurity training program for all employees, but few give much guidance about what the program should contain. What do you train them on? What actually works? Other than checking a box on the compliance forms, are these programs useful?
Why Have a Cybersecurity Training Program?
Don't discount “checking the box” on your compliance program as a motivator for your teammates. For some team members, just knowing that if they take this training, your company can be in compliance, and that it will impact the future growth and success of the business, will be encouragement enough.
Primarily, you want your people to be aware of potential security problems and how your company wants them to deal with those situations. You want this knowledge to stick and your teammates to take action. Having everyone attuned to the organization’s security approach will reduce issues, and give you a baseline for improving or changing the security culture.
The company currently has a security culture, but is it the culture you want to have? It is important to know where you are starting, and to know if the end goal is merely achieving compliance, learning to recognize a phishing scam, or a much higher ideal.
How Do Adults Learn?
Children's brains are made to absorb knowledge, taking in as much information they encounter. The science devoted to understanding how adults learn differently is called andragogy. One principle of the adult learning style is that adults must want to learn and will learn only what they feel they need to learn. They learn by doing and often their learning focuses on problem solving rather than sequentially. Adult learning is influenced by: their personal experience; the setting (such as an informal situation, and the need to be an equal partner in the process; and, of course, the overall enjoyment of the learning process. If we want the knowledge to stick, the training program should take these factors into account.
How do you increase an adult’s desire to learn? Know that your group will have a variety of motivations, and appeal to them all. Some may enjoy the break from their normal work to think about something new. Many will want to know how this training will help them solve a problem. Communicating about the training at different levels may help increase engagement at all levels.
Structuring a Program
There is a benefit to doing a single annual training - also known as “one and done” - but most of that benefit is on the program coordination side rather than on the student side. It's certainly easier to plan and track for compliance reporting, and if this satisfies the minimum standard, this method is certainly available. However, it's pretty easy for the learners to grumble through a long session to get their certificate and then not think about security again for the rest of the year, and new hires may miss out on this opportunity to learn the new security culture by months.
Another option is to use much smaller training modules, either monthly, or quarterly. This allows the training to be more approachable - it's a 15-minute task, rather than hours - and it happens regularly and pretty painlessly. It also makes security something the team thinks about all year long, rather than as a session they complete and then forget. However, tracking this for compliance purposes does take some thought or additional automation tools.
In addition to training videos or modules with quizzes, the training topics will be retained longer if the team member is exposed to it a second or third time. For example, your training video may focus on the topic of malware. Later that month, you may email around a link to an article on a competitor who was a malware victim, and what it cost to recover in time and money. Then, in a company meeting, a manager may bring up malware as a concern. Reiterating the topic not only gives it time to sink in, but it also presents the data in different ways, which increases the awareness of the topic.
The training should always be relevant to the audience. There are topics that may need to be repeated annually for all staff members. Password security and phishing are in perennial need - and there are some topics that may only be applicable to certain groups - CEO fraud is of interest to all financial staff, and Software Bill Of Materials (SBOM) security can be critical to developers. As part of your structure, you may also reserve a slot in the year for targeted training for issue pertinent to subgroups of teammates.
Current Topics
Consider potential topics for a general audience, as well as topics specific to your industry. Try not to use the same exact training modules year after year, as the team will become bored. Mix it up! Here are some ideas:
- Passwords
- Phishing
- Information Security
- Ransomware
- Social Engineering
- Removable Media
- Browser Security
- Mobile Security
- Physical Security
- Email security
- Public Wi-fi
- Multi Factor Authentication
- Remote work
To increase engagement, you may be able to gather a cross functional team to review and select the training modules - an individual learner may not have selected the training, but it's coming from their peers rather than some faceless corporate email. That team can also be used to assemble newsletters or be cybersecurity cheerleaders in their departments.
Training Delivery
There are many companies that offer computer based training, often as short videos and quizzes. They also give the ability to keep records about who took which training class, or automatically remind them (or their managers) what's due. It is important to review these modules to confirm they meet your organizational demographics and goals. For instance, while your global company may transact business in a primary language, selecting training modules are multilingual allows you to give teammates the ability to review them in their most comfortable language. If you have specific password complexity requirements, don't use a module that contradicts your company's needs.
There are also other means of training or reinforcement:
You can find free videos on the internet, and show them in team meetings, with some questions to prompt discussion.
- Articles abound - if your topic is phishing, you can easily find an article on a recent phishing attack, and what it cost a company to recover. The reason these topics are hot is because there are problems in the wild, and news about breaches can show your teammates why it's important.
- Posters and newsletters can be created for display or an internal email blast, depending on whether your company culture involves gathering at the bulletin board or reading longer emails/blog posts.
- Games and toys are a creative way of driving participation in security training programs. You may see these in training tools, or you can create your own. For example, a slide presentation of emails, with teams deciding what's a phish or not. Passing out shortbread with a description of good internet cookies versus bad internet cookies. Without a lot of effort, the training program can be memorable and fun.
Delivering Feedback
After the employee completes the assigned training, there are several ways to provide feedback, which can snowball into future eagerness for cybersecurity training:
- Provide a certificate of completion. It can be an emailed document with the teammate's name, course title, length of session, and administering organization. Not only is this an instance acknowledgement that some teammates thrive on, there are professional organizations that will honor these as Continuing Education Units.
- Publish Key Performance Indicators. Note how many people completed their training on time, possibly by department. (Individually naming-and-shaming often backfires, and is best avoided.) This can be used to let folks know that the executives find this important, and often will spur managers to not let their group drop in the standings.
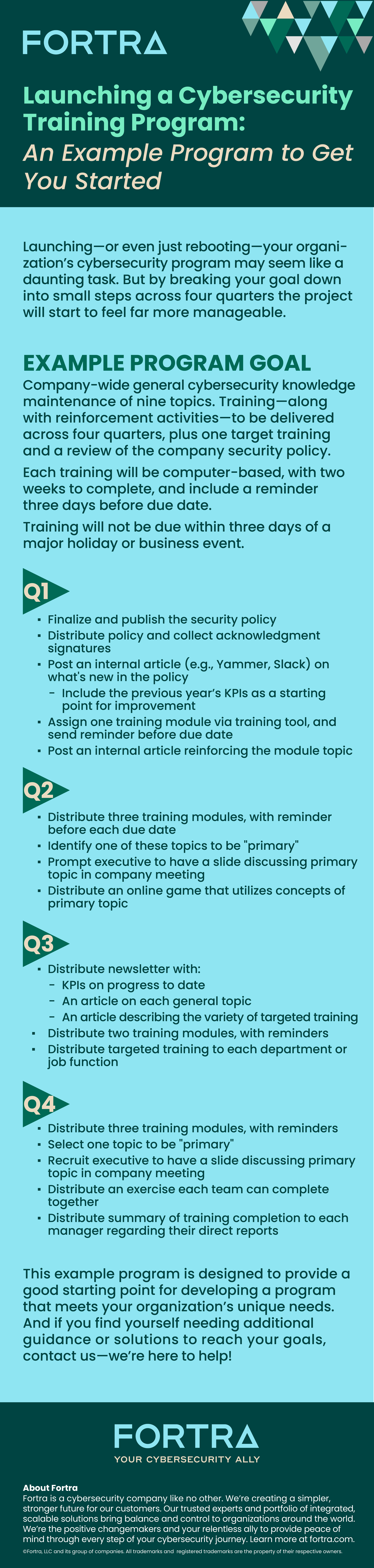
Conclusion
There are a lot of good ways to develop a training program, and what works is going to depend on your industry, your culture, and what you can invest into it. Each program should acknowledge its reachable goal and design, it's structure around the goal, aiming towards incorporating adult learning principles.
While training can be delivered without a specialized integrated tool, they certainly make distributing and tracking easier.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

