
What is the BlackLock ransomware?
BlackLock is a relatively new ransomware group. First seen in March 2024, the ransomware operation initially operated under the name El Dorado, before rebranding as BlackLock late last year.
BlackLock follows a RaaS (ransomware-as-a-service) business model, leasing its tools and infrastructure to affiliates who launch attacks, sharing a proportion of the proceeds with BlackLock.
And I guess they do the normal thing of encrypting your data and demanding a ransom?
Yes, like many other ransomware groups, BlackLock both encrypts victims' files and exfiltrates data - issuing threats to publish it if ransoms are not paid. BlackLock uses custom-built ransomware to target Windows, VMWare ESXi, and Linux environments.
So not just Windows?
No, although the Linux version of BlackLock's ransomware is not considered as mature as its Windows-based sibling.
So what makes BlackLock noteworthy?
BlackLock has become a big deal, very quickly. It has been predicted to be one of the biggest RaaS operations of 2025, following a dramatic increase in the number of posts on its dark web leak site.
BlackLock is reported to have launched 48 attacks in the first two months of 2024, impacting multiple industry sectors with construction and real estate firms hit the hardest.
In addition, BlackLock has been actively attracting new affiliates on RAMP, a Russian-language ransomware-focused cybercrime forum, as well recruiting developers, initial access brokers and traffers (people who direct victims to malicious content.)
BlackLock is represented on RAMP by an individual calling themselves "$$$", who has posted nine times more frequently than its nearest competitor (RansomHub) - giving some indication of the group's aggressive promotion to other criminals.
Shouldn't more be done to shut down cybercriminal forums like this?
It's not an easy problem to solve. But law enforcement has had success in seizing ransomware and other cybercriminal sites in the past. We can only hope that they will continue to have successes.
How will you know if your company has been hit by BlackLock?
It will be very obvious that you have a serious problem. Files will not only be encrypted, but also renamed - with random characters.
In addition, the ransomware drops a file on impacted systems entitled “HOW_RETURN_YOUR_DATA.TXT" which contains the extortion note, demanding a Bitcoin payment.
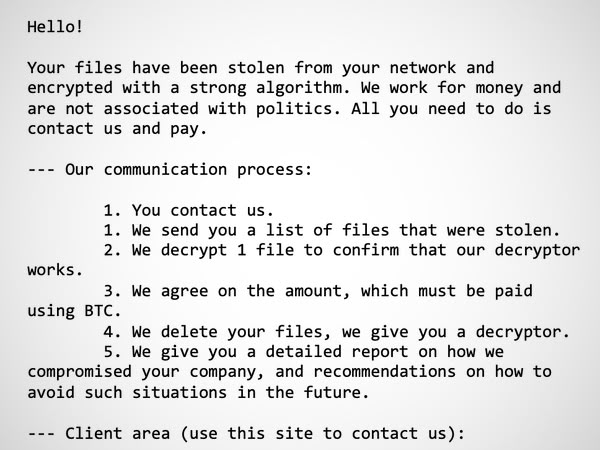
And, of course, if you don't co-operate with the BlackLock gang your data is published on its leak site?
Afraid so. Researchers who have looked at the BlackLock leak site say that it uses clever tricks to try to make it harder for investigators to download details of victims and figure out what files have been stolen, presumably in an attempt to pressure victims into paying out more quickly.
Ransomware experts have been able to carefully circumvent these barriers by using randomised download intervals, unique browser agents and other techniques to automate file downloads.
So how can my company protect itself from Blacklock?
The best advice is to follow our recommendations on how to protect your organisation from other ransomware. Those include:
- making secure offsite backups.
- running up-to-date security solutions and ensuring that your computers are protected with the latest security patches against vulnerabilities.
- using hard-to-crack unique passwords to protect sensitive data and accounts, as well as enabling multi-factor authentication.
- encrypting sensitive data wherever possible.
- reducing the attack surface by disabling functionality that your company does not need.
- educating and informing staff about the risks and methods used by cybercriminals to launch attacks and steal data.
Editor’s Note: The opinions expressed in this and other guest author articles are solely those of the contributor and do not necessarily reflect those of Tripwire.
Beating the Business of Ransomware
Learn how to beat cybercriminal’s ransomware business.
