
I recently spoke at a Fortra Webinar about CIS and MITRE. More specifically, I discussed the intersection between the CIS Critical Security Controls, CIS Benchmarks, and MITRE ATT&CK. In this post, I won't go into deep details about the core background, but there are plenty of excellent references available online, including our breakdown of the various CIS Controls. I do, however, want to share the outcome of my research.
One of the things that prompted my decision to talk about the intersection between these offerings was a CIS blog post discussing how they would start mapping the CIS Benchmarks to MITRE ATT&CK and the CIS Community Defense Model. According to the write-up, they would start with the Windows 10 benchmark. I was excited to dig deeper, only to discover that the latest Windows 10 benchmark does not contain these efforts, and you need to go to an older version. Additionally, only the Excel version of the benchmark contains the mapping.
After spot-checking a few additional benchmarks, I decided that there had to be a better way and decided to leverage the CIS SecureSuite API. I figured that I could leverage Python to pull down the Excel docs for each benchmark and process them to see if they contained the MITRE ATT&CK mappings. Ultimately, this wasn't possible because the Download Benchmark endpoint only supports JSON, SCAP, YAML, XCCDF+AE, and Datastream. There is a separate endpoint for the PDF, but no such endpoint for Excel.
At this point, I was very much committed to mapping benchmarks to ATT&CK and saw a lot of value in how it could be used alongside ATT&CK Navigator to discuss enterprise security within organizations. So, I started to look at how I could get from point A (CIS Benchmark) to point B (MITRE ATT&CK).
Luckily, there was a third dataset that was associated with all the data I was interested in – the CIS Critical Security Controls. As part of the CIS Community Defense Model, CIS provides a mapping between the Controls and ATT&CK. Specifically, v8 of the Controls are mapped to V8.2 of MITRE ATT&CK. This is an older version of ATT&CK, but it gives us a dataset to work with. The Excel document with these mappings can be downloaded from CIS WorkBench or via a quick internet search. Since the CIS Benchmarks contain a mapping to the Controls, we can now tie our CIS Benchmarks back to MITRE ATT&CK.
Since we are using two separate datasets and forcing them together without a lot of context, we end up with a rough mapping, but it is good enough to get the discussion started. So, let's take a look at how you can build these mappings for any benchmarks that you use internally. We'll get started by taking a closer look at the CIS SecureSuite API.
Before we dig too deep into the API, I'd like to point out a typo in the documentation that impacted the work I did to implement this. An issue has been filed against the documentation.
- The documentation for the benchmarks endpoint, which allows you to List Available Benchmarks, incorrectly includes the field benchmarkUrl. That field is actually benchmarksUrl.
To accomplish my goal of mapping these two pieces of data, I wrote a couple of Python scripts, which you can access on GitHub. Within the repo, you'll find:
- requirements.txt: To be used with pip -r requirements.txt in order to install the Python packages used by the scripts.
- api.py: A partial implementation of the CIS API. It includes the following functions:
- get_token: To authenticate with your CIS SecureSuite license.
- get_benchmarks: To access the public list of all CIS Benchmarks.
- get_benchmark: To download a single benchmark in the specified format and return the benchmark content (CIS SecureSuite License required).
- write_benchmark: To download a single benchmark and write the files to disk (CIS SecureSuite License required).
- get_pdfs: To access the public list of all CIS Benchmark PDFs.
- write_pdf: To download a single benchmark PDF and write the file to disk.
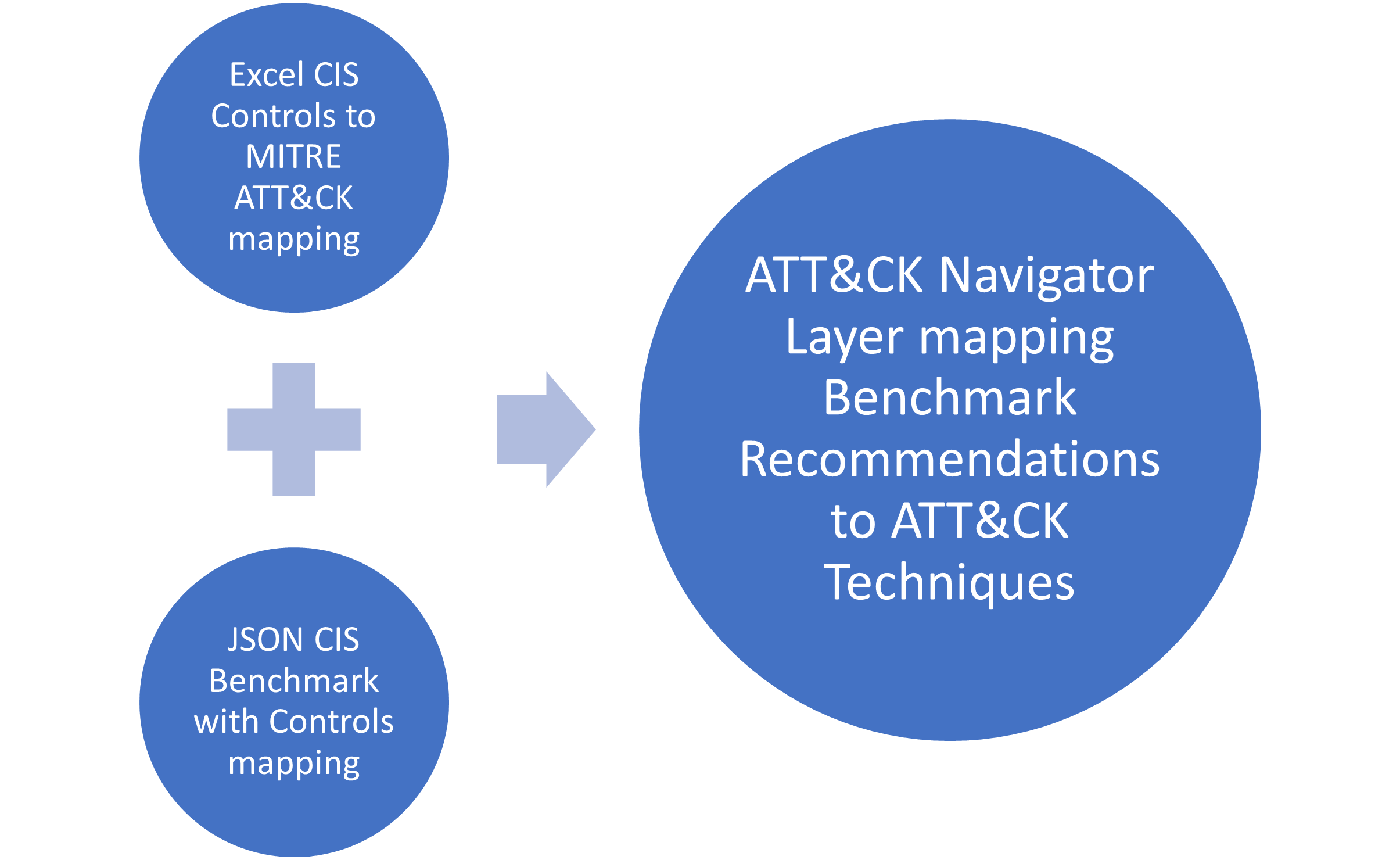
- mapper.py: A script to parse the CIS Community Defense Model Critical Security Controls to the MITRE ATT&CK Excel mapping file and map it to the JSON CIS Benchmarks that include CIS Security Controls. The output is an ATT&CK Navigator layer file.
When you run mapper.py, you'll get help output that looks like this:
CANTREGULYM3:cis-api treguly$ ./mapper.py
usage: mapper.py [-h] [-f FILENAME] [-o OUTFILE] [-l LICENSE_FILE] [-b BENCHMARK_ID] [-1] [-2]
Map CIS and ATT&CK Content!
options:
-h, --help show this help message and exit
-f FILENAME, --file FILENAME
Input Filename
-o OUTFILE, --out OUTFILE
Output filename (default: attack_layer.json).
-l LICENSE_FILE, --license LICENSE_FILE
CIS SecureSuite License File
-b BENCHMARK_ID, --benchmark BENCHMARK_ID
CIS Benchmark ID
-1, --can Generate a json file that maps CIS Critical Security Controls to MITRE ATT&CK for ATT&CK Navigator
-2, --ban Generate a json file that maps a CIS Benchmark to MITRE ATT&CK for ATT&CK Navigator
You can then generate a JSON layer for ATT&CK Navigator using the following command:
CANTREGULYM3:cis-api treguly$ ./mapper.py -2 -l license.xml -b 12741 -f 'CIS Controls v8 to Enterprise ATT&CK v8.2 Master Mapping - 5.26.2021.xlsx' -o cisco.json
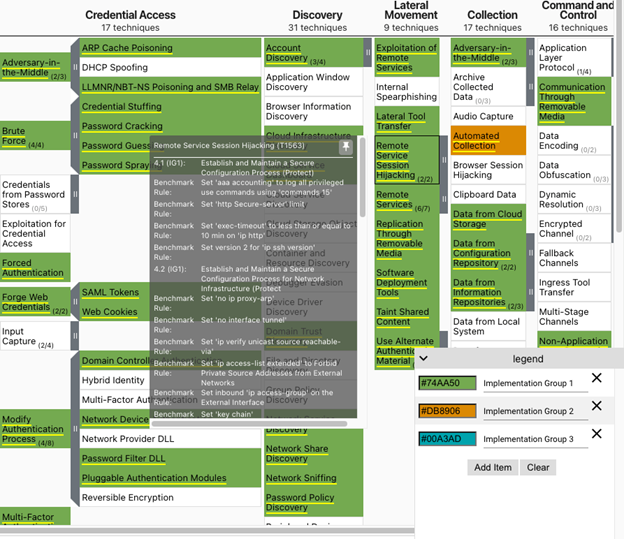
The written JSON file, in this case, cisco.json, contains all the data required to create a new layer within ATT&CK Navigator. Simply browse to ATT&CK Navigator and use the "Open Existing Layer" option. The result will be a color-coded Navigator layer highlighting all of the techniques that are associated with the Critical Security Controls that were included in the original benchmark, which might be more easily represented with an image.
When loaded into Navigator, the resulting layer is filled with a plethora of information. Techniques are color-coded based on the Implementation Group of the Critical Security Control Safeguard, as indicated by the legend. The tooltip (which can be seen when hovering or by right-clicking and selecting "pin/unpin tooltip") includes the Benchmark Recommendations and the Critical Security Control Safeguard ID, Title, and Implementation Group. Finally, the right-click menu on any highlighted technique includes links to Fortra and Tripwire.
While there's still work to do to provide a full implementation of the API and likely some clean-up that could be done with the mapping to provide more concise data, the ability to map your implemented benchmarks to ATT&CK techniques allows enterprises to have more accurate conversations around their organizational and operational security posture. If you end up leveraging this in your organization, I'd love to hear how you're using it and if you've found it useful.
Mastering Security Configuration Management
Master Security Configuration Management with Tripwire's guide on best practices. This resource explores SCM's role in modern cybersecurity, reducing the attack surface, and achieving compliance with regulations. Gain practical insights for using SCM effectively in various environments.

